Chapter 5 CCNA Exam Answers Explained
In this section, we dive deep into essential topics related to network configurations, protocols, and management techniques that are critical for mastering fundamental networking concepts. The focus is on understanding core principles that will enhance your practical skills and theoretical knowledge.
Network design and configuration play a significant role in ensuring smooth communication within systems. From addressing schemes to the configuration of network devices, understanding how these elements interact is crucial for success. Subnetting and routing are also fundamental skills that enable efficient data transmission across multiple networks.
Throughout this guide, we’ll explore various strategies and methods to tackle the most challenging aspects of networking. With a strong grasp of these topics, you’ll be equipped to troubleshoot issues and optimize network performance, ensuring seamless connectivity across a range of devices and environments.
Chapter 5 Network Configuration Insights
This section explores the critical concepts and practical knowledge necessary for mastering the configuration and management of network devices. It focuses on key topics that will help you understand how different components of a network interact and how to effectively implement various protocols and configurations.
To succeed in this area, it’s essential to familiarize yourself with the following concepts:
- Understanding network addressing and subnetting
- Configuring routing protocols for efficient data flow
- Setting up VLANs for better network management
- Applying security measures to safeguard network operations
Each topic plays a vital role in ensuring smooth and secure communication within a network. The practical application of these concepts will significantly improve your ability to design, configure, and troubleshoot network systems. By mastering these foundational elements, you’ll gain the expertise needed to excel in any networking environment.
As you review these key topics, focus on the practical skills required to implement and configure networking solutions effectively. Familiarity with various routing protocols, IP addressing schemes, and security best practices will provide the confidence necessary for tackling real-world scenarios.
Understanding Key Networking Topics
This section focuses on the fundamental concepts that are essential for mastering network configurations and operations. These topics form the backbone of network management, and understanding them will provide a solid foundation for building, securing, and optimizing network systems.
Network addressing is the first critical topic to grasp. It involves assigning unique identifiers to devices, allowing them to communicate efficiently across networks. Subnetting plays a key role in segmenting networks for better performance and security.
Another essential area is routing protocols, which help determine the best paths for data to travel between devices. These protocols are crucial for ensuring reliable and efficient communication across different network segments. Along with this, understanding network security practices is vital for protecting data and maintaining system integrity.
By mastering these topics, you’ll be better equipped to design, configure, and troubleshoot networks, ensuring both their functionality and security. These are the building blocks for anyone looking to pursue a career in network management or administration.
Key Concepts in Networking Fundamentals
This section delves into the essential principles that form the foundation of networking. Understanding these core concepts is crucial for building, maintaining, and troubleshooting network systems. These topics cover everything from device configuration to protocol implementation, helping to ensure efficient and secure communication across networks.
Important Networking Principles
- IP Addressing: The process of assigning unique identifiers to devices, enabling them to communicate across various networks.
- Subnetting: Dividing a larger network into smaller, manageable segments for better performance and security.
- Routing Protocols: Determining the best routes for data to travel between networks, ensuring efficient data delivery.
- VLAN Configuration: Creating virtual networks within a physical network to improve traffic management and security.
Network Security and Troubleshooting
- Access Control Lists (ACLs): Configuring rules to control the flow of traffic in and out of the network, improving security.
- Network Address Translation (NAT): A technique for remapping IP addresses to improve security and reduce network congestion.
- Common Troubleshooting Techniques: Identifying and resolving issues such as IP conflicts, connectivity failures, and protocol misconfigurations.
By mastering these concepts, you will gain the necessary skills to design, configure, and secure networks effectively, ensuring that systems remain operational and protected from external threats.
Networking Protocols Covered in Chapter 5
This section explores the key communication protocols that play a central role in modern networking. These protocols ensure that data is transmitted reliably and efficiently across various network environments. Understanding how these protocols function is essential for managing and troubleshooting network systems effectively.
The following table summarizes some of the most important networking protocols you will encounter:
| Protocol | Description | Purpose |
|---|---|---|
| TCP/IP | A set of protocols used for transmitting data across the internet and local networks. | Facilitates communication between devices on a network, ensuring reliable and error-free data transfer. |
| UDP | A connectionless protocol used for fast, low-overhead transmission of data. | Used for applications that require speed rather than reliability, such as streaming or VoIP. |
| HTTP | The protocol used for transferring web pages on the internet. | Enables communication between web browsers and web servers for delivering content. |
| DNS | The system that translates human-readable domain names into IP addresses. | Allows users to access websites using domain names instead of numeric IP addresses. |
| FTP | A protocol for transferring files between computers over a network. | Used for uploading and downloading files, commonly in web development and server management. |
Each of these protocols plays a vital role in ensuring seamless data exchange, and a solid understanding of their functions will help you in configuring and managing networks more efficiently. Being familiar with these communication standards is crucial for anyone working in network administration and support roles.
Common Questions from Networking Concepts

This section highlights typical questions that assess your understanding of core networking topics. These questions often focus on key principles, protocols, and configurations that are essential for successful network management. Preparing for these types of questions can help reinforce your knowledge and ensure you’re ready to tackle real-world network challenges.
Some of the most common types of questions you may encounter include:
- Configuring IP addresses and subnet masks for network devices
- Identifying and troubleshooting routing protocol issues
- Understanding the differences between TCP and UDP and their applications
- Explaining how VLANs improve network segmentation and security
- Configuring and verifying NAT and its role in IP address translation
- Describing the process of network troubleshooting using diagnostic tools
By practicing these types of questions and thoroughly reviewing the underlying concepts, you will build a deeper understanding of how to design, configure, and maintain network systems efficiently and securely.
IP Addressing Explained
In this section, we will explore the foundational concept of IP addressing, a crucial component for enabling communication between devices on a network. Proper addressing ensures that each device can be uniquely identified and interact efficiently with others, both locally and across the internet.
IP addressing involves assigning a unique numerical identifier to each device, which can be either a public or private address depending on the network. The format of an IP address is composed of four octets, with each octet representing a number from 0 to 255. These addresses are categorized into different classes to manage the available address space effectively.
Understanding the following key aspects is essential for grasping IP addressing:
- IP Classes: Different ranges of addresses (Class A, B, C, etc.) serve distinct purposes, such as large-scale networks or smaller local networks.
- Subnetting: This process divides a network into smaller, more manageable sections, improving performance and security.
- Private and Public Addresses: Public addresses are used on the internet, while private addresses are reserved for internal network communication.
- Network vs. Host Portions: An IP address is split into a network portion (identifying the network) and a host portion (identifying the device within the network).
Mastering IP addressing is essential for network configuration and troubleshooting, allowing network administrators to ensure seamless connectivity and efficient use of available address space.
Subnetting Techniques for Network Management
Subnetting is a critical skill for network professionals, enabling efficient use of IP address space and optimizing network performance. By dividing large networks into smaller subnets, subnetting enhances security, improves traffic management, and simplifies network administration. This section outlines the most effective techniques for performing subnetting, focusing on methods that ensure scalability and efficient network design.
Understanding Subnetting Basics
- Subnet Mask: A subnet mask determines which portion of an IP address refers to the network and which part identifies the host. By manipulating the mask, you can create multiple subnets from a single network.
- Classful Addressing: Networks are initially divided into classes (A, B, C), each with predefined ranges of IP addresses. Understanding these classes helps in efficiently assigning and subdividing address spaces.
- Network and Host Bits: Subnetting involves adjusting the number of bits used for the network and host portions of an IP address. This helps in creating more subnets or allocating more hosts per subnet, depending on requirements.
Subnetting Calculation Methods

- Borrowing Bits: By borrowing bits from the host portion of an address, you can create additional subnets. This allows for more efficient use of available IP space in a network.
- CIDR Notation: Classless Inter-Domain Routing (CIDR) allows for more flexible subnetting by specifying the number of network bits directly, rather than relying on traditional class boundaries.
- Subnetting Formula: The formula for determining the number of subnets and hosts per subnet is based on the number of borrowed bits. For example, with a subnet mask of 255.255.255.0, you have 256 possible addresses, including network and broadcast addresses.
Practicing these techniques will help you efficiently divide and manage networks, ensuring that IP addresses are used effectively while supporting scalable and secure network architecture.
Routing Protocols Overview
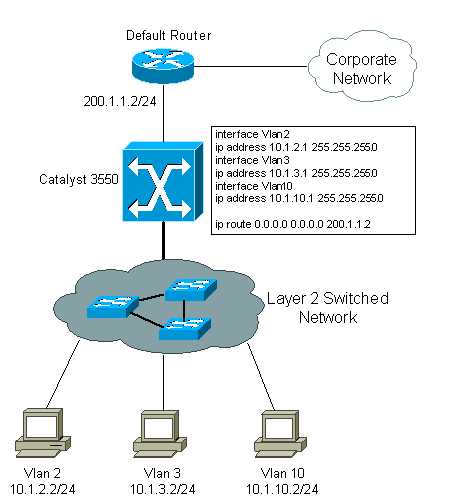
Routing protocols are essential for enabling communication between different networks by determining the best paths for data to travel. These protocols dynamically exchange routing information, allowing routers to update their routing tables and adapt to network changes. Proper understanding of routing protocols is crucial for optimizing network performance, ensuring reliable data transmission, and maintaining network stability.
Routing protocols can be classified into different categories based on their functionality, such as distance-vector, link-state, and hybrid protocols. Each type has its own advantages and use cases, depending on the network size, complexity, and performance requirements.
The most commonly used routing protocols include:
- RIP (Routing Information Protocol): A distance-vector protocol that uses hop count as its metric to determine the best path. It’s best suited for small networks due to its simplicity.
- OSPF (Open Shortest Path First): A link-state protocol that uses a more sophisticated metric, allowing for faster convergence and more efficient use of network resources in larger, more complex networks.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid protocol that combines the best features of both distance-vector and link-state protocols, providing scalability and faster convergence times.
- BGP (Border Gateway Protocol): A path-vector protocol used primarily for routing between different autonomous systems on the internet, making it crucial for inter-network communication.
Understanding how these protocols work and their strengths and weaknesses is vital for configuring efficient routing in a network. Choosing the appropriate routing protocol can significantly improve network performance and minimize issues such as packet loss or delays.
Managing Network Devices Efficiently
Effective management of network devices is crucial for maintaining optimal performance, security, and scalability within a network. Properly configured and well-maintained devices ensure seamless communication, minimize downtime, and improve the overall reliability of the network. This section covers key strategies and best practices for managing routers, switches, firewalls, and other network components efficiently.
One of the primary goals of network device management is to ensure that all devices are properly configured, monitored, and updated to keep the network running smoothly. Regular monitoring helps identify potential issues before they affect performance, while automated management tools can streamline configuration tasks and reduce the risk of human error.
Here are some essential practices for efficient network device management:
- Device Configuration: Establish and maintain standardized configuration templates for all network devices to ensure consistency and simplify troubleshooting.
- Firmware and Software Updates: Regularly update device firmware and software to enhance security, fix bugs, and improve performance.
- Monitoring and Logging: Use network monitoring tools to track device performance, detect faults, and review logs for suspicious activity or issues.
- Access Control: Implement strict access control policies, ensuring that only authorized personnel can modify device settings or access sensitive information.
- Backups and Recovery: Regularly back up device configurations to prevent data loss and ensure quick recovery in case of a failure.
By adhering to these management practices, network administrators can ensure the stability and security of the entire network infrastructure, minimizing risks and maximizing operational efficiency.
OSI Model Relevance in Networking

The OSI (Open Systems Interconnection) model serves as a fundamental framework for understanding how different network protocols interact within a system. By breaking down the communication process into seven distinct layers, the OSI model helps simplify complex network interactions, making troubleshooting, configuration, and optimization more manageable. Its relevance remains crucial in practical network design and operations, as it provides a common language for professionals to describe and address networking issues.
Each layer of the OSI model corresponds to specific functions that contribute to data transmission across networks. By understanding how protocols operate at each layer, network engineers can diagnose problems more efficiently, select appropriate technologies, and optimize network performance.
Here’s a summary of the seven layers of the OSI model:
| Layer Number | Layer Name | Function |
|---|---|---|
| 7 | Application | Enables end-user applications to communicate over the network, including web browsers and email clients. |
| 6 | Presentation | Translates data formats, encrypts, and compresses data for secure transmission. |
| 5 | Session | Manages sessions or connections between devices, ensuring communication is maintained. |
| 4 | Transport | Ensures reliable data transfer and error correction, managing flow control and data segmentation. |
| 3 | Network | Routes data packets between devices across different networks. |
| 2 | Data Link | Provides error detection and correction and manages the physical addressing of data packets. |
| 1 | Physical | Transmits raw data bits over a physical medium, such as cables or wireless connections. |
Understanding the OSI model is essential for troubleshooting network issues, as it helps professionals pinpoint where problems are occurring in the communication process. It also aids in choosing the right tools and techniques for configuring devices and optimizing network performance at each layer.
VLAN Configuration Insights
Virtual Local Area Networks (VLANs) are an essential aspect of network segmentation, enabling network administrators to create logical groupings of devices within the same physical infrastructure. By isolating broadcast domains, VLANs improve network security, performance, and management efficiency. Proper configuration of VLANs is crucial for ensuring that network traffic is efficiently routed, while minimizing congestion and unnecessary traffic.
Configuring VLANs effectively allows administrators to control how traffic flows across the network, ensuring that only the necessary devices can communicate with each other. This reduces the chances of network bottlenecks and helps optimize overall performance. Understanding the key components involved in VLAN configuration is essential for maintaining a secure and efficient network.
Below are some key VLAN configuration steps and best practices:
| Step | Action | Explanation |
|---|---|---|
| 1 | Create VLANs | Define VLANs on network switches, assigning them unique identifiers (VLAN IDs) for better management and segmentation. |
| 2 | Assign Ports to VLANs | Assign switch ports to specific VLANs based on the devices that need to be grouped together for communication. |
| 3 | Configure VLAN Trunking | Enable trunking on switches to allow multiple VLANs to pass through a single link between devices, using protocols like IEEE 802.1Q. |
| 4 | Verify VLAN Configurations | Use network tools such as “show vlan” or “show interface” commands to confirm that VLAN settings are correctly applied and functioning. |
| 5 | Configure Inter-VLAN Routing | Set up routing protocols or Layer 3 switches to enable communication between devices on different VLANs. |
By following these steps and best practices, network administrators can ensure that their VLAN configurations are efficient, secure, and capable of meeting the needs of the organization. Proper VLAN management reduces network complexity, improves traffic flow, and enhances overall network security.
Configuring Static and Dynamic Routing
Routing is a fundamental process in networking, where data is directed from one device to another across networks. The method used for routing can greatly affect network efficiency and traffic management. Two primary routing types exist: static and dynamic. Static routing is manually configured and offers stability, while dynamic routing allows routers to automatically adjust routes based on network conditions. Understanding how to configure both routing methods is essential for ensuring optimal performance and reliability in network design.
Static routing is useful in smaller networks where routes rarely change. By defining explicit paths for data to follow, static routes provide simplicity and control. However, dynamic routing protocols are necessary for larger, more complex networks where routing decisions must adapt to changing conditions and failures.
Below are the key differences and configuration steps for static and dynamic routing:
Static Routing Configuration
- Static routes are manually entered into a router’s configuration.
- Useful for small networks with predictable traffic flow.
- Requires detailed knowledge of the network topology.
- Can be configured using commands such as
ip routein Cisco devices. - Offers greater control but lacks flexibility.
Dynamic Routing Configuration
- Dynamic routing protocols automatically exchange routing information between routers.
- Protocols like RIP, OSPF, and EIGRP are used to discover routes in real-time.
- Adapt to network changes, such as link failures or topology changes.
- Requires configuration of routing protocol settings on all involved routers.
- Can handle large and complex networks with ease, offering flexibility and scalability.
When configuring static and dynamic routing, it’s important to consider the network size, performance requirements, and redundancy needs. Static routing offers simplicity and control for smaller networks, while dynamic routing excels in larger, more dynamic environments where automatic adjustment to changes is necessary.
IP Routing Tables Interpretation
Routing tables are essential components in networking, as they determine the best path for data packets to travel across a network. Each router maintains a routing table, which consists of multiple routes that help direct the flow of traffic. Understanding how to interpret the information in these tables is crucial for diagnosing network issues, optimizing traffic flow, and ensuring reliable communication between devices.
Each entry in a routing table typically includes the destination network, the next-hop address, the routing metric, and the interface through which the packet should be forwarded. By analyzing these entries, network administrators can assess how traffic will be routed, whether through static or dynamic routes, and how different paths affect performance and reliability.
Key elements to focus on when interpreting routing tables:
- Destination Network: The IP address of the network that the router can reach.
- Next-Hop Address: The IP address of the next router or device that will forward the packet.
- Interface: The router interface through which the packet will be sent.
- Metric: A value indicating the “cost” of the route, used to determine the most efficient path.
- Routing Protocol: Identifies how the route was learned (e.g., OSPF, RIP, static).
By interpreting the routing table, administrators can ensure that data packets are traveling along the most efficient paths, detect misconfigurations, and troubleshoot issues such as incorrect routing or network congestion. Proper analysis of routing tables is key to maintaining a well-optimized and reliable network environment.
Network Security Topics in CCNA
Network security is a critical aspect of modern networking, ensuring that data and communication remain protected from unauthorized access, tampering, and disruptions. As networks grow in size and complexity, the need to implement strong security measures becomes even more essential. Topics related to network security cover a wide range of strategies and technologies aimed at safeguarding the integrity and confidentiality of data as it travels across the network.
Understanding key security concepts is vital for anyone working with networks, from small businesses to large enterprise environments. These concepts include access control, encryption, firewalls, and intrusion detection systems, each of which plays a unique role in mitigating security risks. Moreover, the proper configuration of security features such as Virtual Private Networks (VPNs) and network access control policies is essential for preventing unauthorized access and ensuring safe communication between devices.
Here are some of the core network security topics that are important in networking education:
- Access Control: Methods for controlling who can access the network and what resources they can use.
- Firewalls: Devices or software used to monitor and control incoming and outgoing network traffic based on security rules.
- Intrusion Detection Systems (IDS): Tools that detect and respond to malicious activities on a network.
- VPN (Virtual Private Network): A method to create a secure connection over a public network, ensuring private data transmission.
- Encryption: The process of encoding data to prevent unauthorized access and ensure its integrity during transmission.
- Authentication Protocols: Protocols such as RADIUS and TACACS+ used to verify the identity of users or devices on a network.
- Network Access Control (NAC): Policies that regulate which devices are allowed to connect to the network based on security criteria.
Mastering these network security topics is vital for maintaining a secure and resilient network. Without proper security measures in place, networks are vulnerable to attacks that could lead to data loss, service interruptions, and damage to the organization’s reputation.
Practical Scenarios in Chapter 5
In networking, theoretical knowledge is essential, but it is the practical application of concepts that truly prepares individuals for real-world challenges. Practical scenarios help illustrate how networking principles can be applied in various situations, providing hands-on experience with critical technologies and tools. These scenarios focus on addressing common issues, configuring network devices, and implementing security measures, giving learners a chance to apply their knowledge in practical settings.
Understanding how to approach networking challenges in a structured manner is crucial. In practice, network administrators must deal with tasks such as configuring IP addresses, troubleshooting connectivity problems, or ensuring data security. Below are some of the practical scenarios that are frequently encountered in networking:
Network Configuration and Troubleshooting
When configuring a network, it is important to ensure all devices are properly set up and can communicate efficiently. Troubleshooting issues often involves identifying incorrect settings, misconfigured routes, or hardware failures. Key tasks in these scenarios include:
- Assigning static and dynamic IP addresses
- Configuring subnet masks and gateways
- Resolving issues with DNS settings
- Diagnosing routing problems using tools like ping and traceroute
Network Security Implementation
Security is a major concern for any network. Configuring secure devices and ensuring protection against potential threats are ongoing tasks. Common practices include:
- Implementing access control lists (ACLs) to restrict network access
- Setting up firewalls to block unauthorized traffic
- Configuring VPNs for secure remote access
- Monitoring network traffic for suspicious activity using intrusion detection systems (IDS)
By engaging with practical scenarios, learners can gain a deeper understanding of the real-world challenges they will face in the field. These hands-on experiences enhance problem-solving abilities and improve overall proficiency in network management.
Exam Tips for Chapter 5
When preparing for any assessment in networking, a strategic approach is crucial for mastering the content and boosting confidence. The material covered in this section is fundamental for understanding how networks operate, from basic configurations to advanced troubleshooting. To perform well in an assessment, it’s important to focus not only on theoretical knowledge but also on practical application and critical thinking skills. Below are some valuable tips to help you succeed in this portion of the course:
1. Master Key Concepts and Terminology
Having a strong grasp of core concepts and technical terms is essential. Make sure to review the fundamental principles behind network addressing, routing, and security protocols. Understanding key terms such as subnetting, VLANs, and routing protocols will help you answer questions accurately and efficiently.
2. Practice Hands-On Configuration
While theoretical knowledge is important, practical skills are equally necessary. Setting up network devices, configuring IP addresses, and working with routing tables can help reinforce your understanding. Spend time working with tools like packet tracers or simulators to replicate real-world scenarios and solidify your hands-on experience.
3. Focus on Troubleshooting Techniques
Many assessments test your ability to diagnose and fix issues in a network. Practice troubleshooting by simulating common problems, such as connectivity failures or incorrect IP configurations. Familiarize yourself with diagnostic tools like ping, traceroute, and netstat to troubleshoot effectively.
4. Review Practice Questions and Case Studies
Working through practice questions can help you get familiar with the type of content and question formats you may encounter. Additionally, reviewing case studies will enhance your ability to apply theoretical knowledge to real-world situations, which is critical for tackling complex questions.
5. Manage Your Time Wisely
Time management is key during assessments. Prioritize easier questions first to build confidence and ensure you have enough time to tackle more challenging ones. Stay calm, read each question carefully, and avoid spending too much time on any single question.
By following these tips and focusing on understanding both the theory and practical aspects of networking, you will be well-prepared to tackle any challenge in this section of the course. Consistent study, practice, and review will lead to success.
Common Mistakes in Chapter 5
When studying networking concepts and configurations, learners often make mistakes that can hinder their understanding and performance. These errors usually stem from overlooking important details or misapplying concepts. In this section, we will highlight some of the most common mistakes that students encounter and provide tips to avoid them. Identifying these pitfalls can significantly improve your grasp of the material and help you prepare more effectively.
- Misunderstanding Subnetting
- Overlooking Routing Table Entries
- Ignoring VLAN Configuration
- Inadequate IP Address Planning
- Relying Too Much on Default Configurations
- Neglecting Security Protocols
- Forgetting to Save Configurations
One of the most common errors is confusion with subnetting calculations. Incorrectly determining subnet masks or addressing ranges can lead to network misconfigurations. Practice subnetting regularly to become familiar with how to break down addresses and understand CIDR notation.
Routing tables are a critical part of networking, and failing to properly interpret or configure routes can cause connectivity issues. Ensure you understand the difference between static and dynamic routes, and verify that routes are correctly configured on each device in the network.
When configuring VLANs, students sometimes neglect to assign ports properly or forget to enable trunking on switches. This results in communication problems between different segments of the network. Always double-check VLAN configurations and trunking settings to avoid issues with inter-VLAN routing.
Improper IP addressing can create a range of issues, from network conflicts to inefficient use of address space. Be sure to follow IP address planning best practices, especially when dividing networks into subnets or assigning addresses to devices.
While default settings on devices may work in some cases, they often don’t provide the necessary flexibility or security. Customizing configurations to suit the specific needs of the network is essential for optimization and security.
In the rush to configure networks, security settings such as access control lists (ACLs) and port security may be overlooked. Always implement necessary security measures to prevent unauthorized access and ensure safe operation of the network.
One of the simplest mistakes is forgetting to save configurations after making changes. If configurations are not saved, they will be lost after a reboot. Make sure to save changes using the write memory or copy running-config startup-config commands.
Avoiding these common mistakes requires attention to detail and consistent practice. By focusing on the fundamentals and reviewing configurations thoroughly, you can ensure that you fully understand the material and are ready to tackle any challenge.
Preparing for the Certification Test
When preparing for a networking certification, it’s crucial to approach the study process methodically and with focus. Mastering the key concepts, understanding the practical applications, and getting familiar with the test format are essential steps for success. This section provides strategies and tips to ensure thorough preparation and a confident approach on test day.
Effective preparation requires a balanced approach, which includes reviewing theoretical concepts, practicing hands-on tasks, and assessing your progress with mock tests. A structured plan can help identify weak areas and give more time to those topics that need extra attention. The following strategies will guide your efforts:
1. Master the Core Concepts
Focus on understanding the fundamental principles of networking. Key topics include:
- IP addressing and subnetting
- Routing protocols
- Network topologies and devices
- VLANs and network segmentation
- Security protocols and measures
It’s essential to grasp these concepts deeply, as they form the foundation for more advanced topics and practical tasks.
2. Hands-on Practice
Theory is important, but practical experience is key to understanding how to configure and troubleshoot networks. Set up a test environment, such as a virtual lab or real hardware, to practice tasks like:
- Configuring routers and switches
- Setting up IP addressing and subnets
- Implementing security features
- Verifying and troubleshooting network connections
Use network simulators like Packet Tracer or GNS3 if real equipment is not available. These tools help you practice without the need for physical devices.
3. Take Practice Tests

Mock tests are invaluable for gauging your readiness. They help you become familiar with the test format and identify areas where you may need further study. Regularly testing yourself also helps manage time effectively, ensuring that you’re prepared to complete the test within the allotted time frame.
4. Focus on Commonly Tested Areas
While all topics are important, certain areas tend to be tested more frequently. These include:
- IP addressing and subnetting
- Routing protocols like OSPF and EIGRP
- VLAN configuration and management
- Network security best practices
By focusing on these commonly tested areas, you can increase your chances of success. However, don’t neglect other topics entirely, as the test may include questions on less common areas.
5. Create a Study Schedule
Establishing a clear, manageable study schedule is critical for staying on track. Break down topics into manageable chunks and assign specific times each week to cover them. This ensures that you don’t overlook any subject area and can approach the test with confidence.
6. Join Study Groups
Collaborating with peers can enhance your learning experience. Study groups provide an opportunity to share knowledge, ask questions, and clarify difficult concepts. Online forums and communities dedicated to networking certifications can also be valuable resources for guidance and support.
7. Stay Calm and Confident
On the day of the test, maintain a calm and focused mindset. Ensure that you’re well-rested, have all necessary materials prepared, and arrive with ample time to spare. A positive attitude and a clear mind will help you approach each question with confidence.
By following these strategies and dedicating time to both theoretical learning and hands-on practice, you will be well-prepared to succeed in your certification journey.