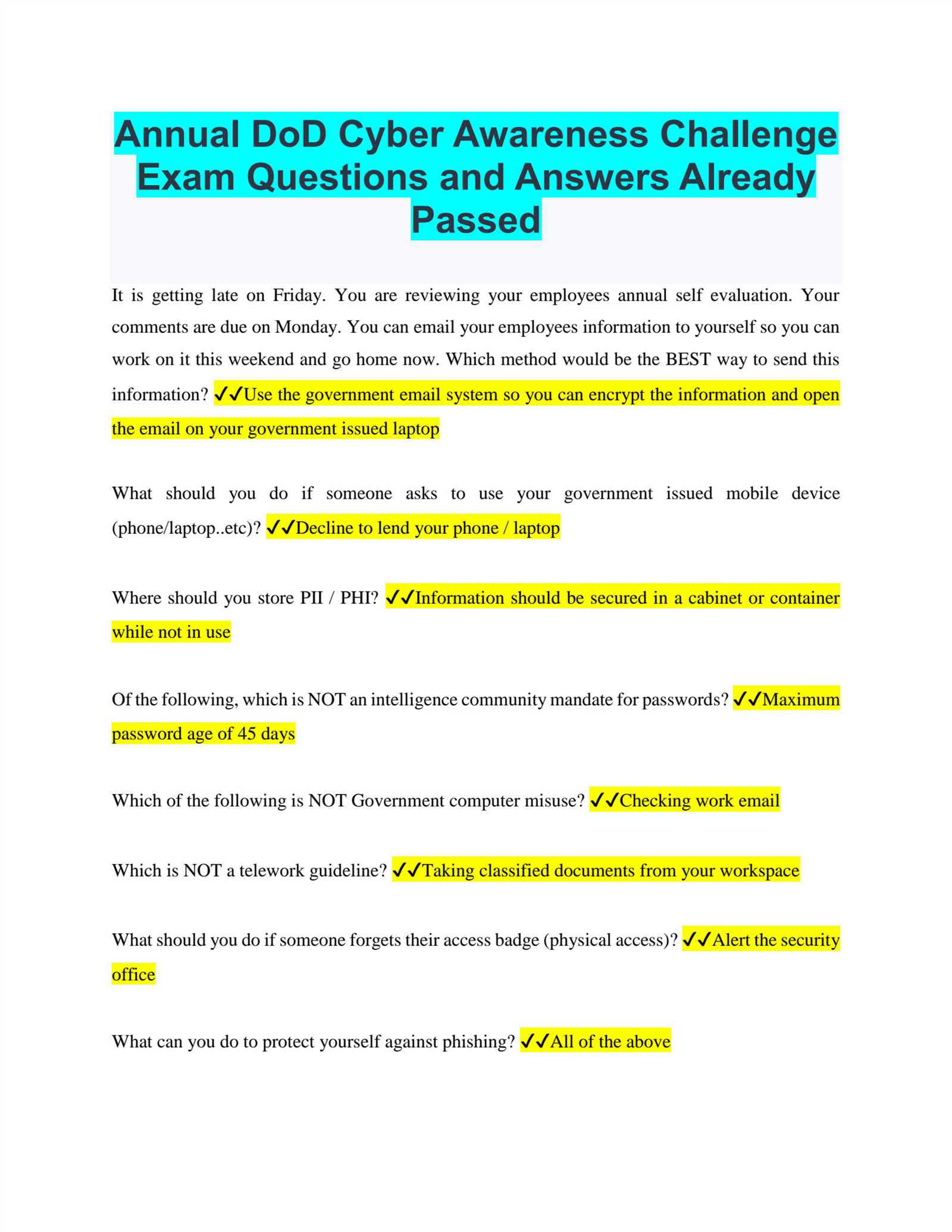
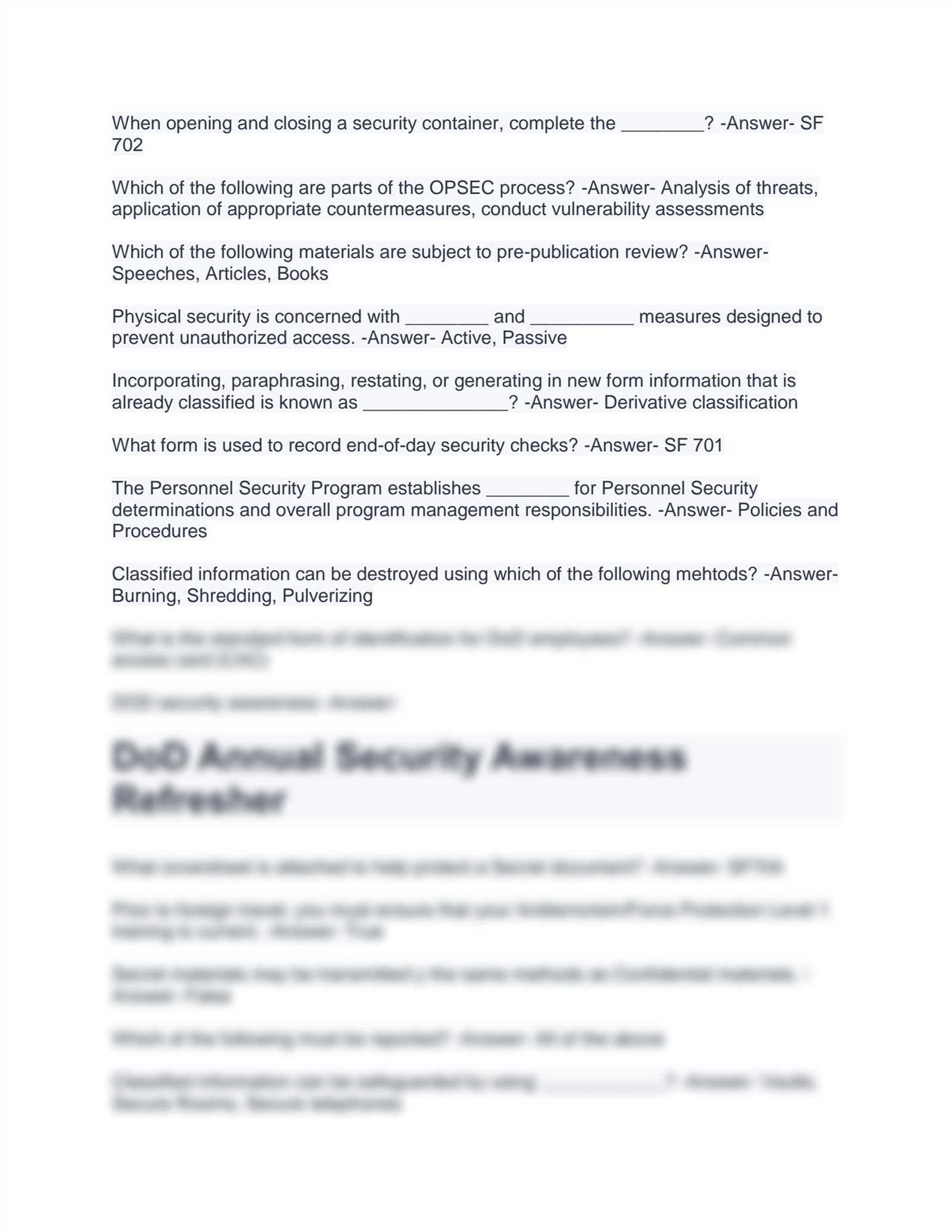
DoD Cyber Awareness Challenge Exam Answers

Ensuring proper knowledge of information protection and risk management is crucial for anyone working in a government or defense-related field. The training provided focuses on equipping personnel with the necessary skills to identify, prevent, and respond to potential security threats. As the digital landscape constantly evolves, staying informed about security protocols is essential for maintaining operational integrity and confidentiality.
Participants are tested on various critical topics designed to assess their understanding of best practices in maintaining a safe and secure environment. From identifying phishing attempts to safeguarding sensitive data, the training covers a wide range of subjects. This preparation is vital not only for compliance but also for the overall safety of the organization’s digital infrastructure.
In this guide, we will discuss the key elements of the training process, highlighting common themes, tips for success, and how to navigate the resources available to achieve a high level of proficiency. By following these recommendations, individuals can enhance their understanding and readiness to handle potential security challenges with confidence.
DoD Security Training Test Preparation
In any organization handling sensitive information, it is essential to ensure that all personnel are equipped with the knowledge needed to identify, mitigate, and respond to security threats. One key aspect of this training involves a comprehensive evaluation that tests employees’ understanding of digital safety protocols. The assessment covers various topics related to securing sensitive data and responding to potential risks.
Successful completion of this assessment requires not only memorizing facts but also applying the learned principles to real-world situations. To help you prepare, it’s important to understand the core subjects frequently tested during the evaluation. Below are some key areas you should focus on:
- Phishing and Social Engineering: Recognizing fraudulent emails, links, and messages designed to steal sensitive information.
- Proper Handling of Classified Information: Guidelines on maintaining confidentiality and preventing unauthorized access to critical data.
- Incident Reporting: The correct process for identifying and reporting security breaches or suspicious activity.
- Data Encryption and Protection: Best practices for safeguarding information both in transit and storage.
- Network Security Protocols: Understanding firewalls, secure connections, and other tools to defend against external threats.
Reviewing these topics will significantly improve your chances of passing the evaluation. In addition, practicing situational awareness and familiarizing yourself with common risk scenarios can provide a deeper understanding of the concepts tested.
Remember, the goal of this evaluation is not just to pass the test but to ensure that you can effectively apply the knowledge in your daily work. Keeping up-to-date with the latest security protocols and continuing your education on best practices is essential for long-term success in maintaining a secure environment.
Understanding the DoD Security Training Test
The test designed to assess employees’ understanding of essential safety protocols is a crucial part of maintaining a secure environment within any organization. It focuses on evaluating an individual’s ability to recognize and respond to potential risks and threats. This assessment is not only a means of testing knowledge but also a way to ensure that personnel can apply security practices in real-world situations.
The structure of this test covers a wide range of topics related to protecting sensitive information, identifying vulnerabilities, and preventing data breaches. Participants are expected to demonstrate their ability to adhere to established guidelines and protocols designed to safeguard digital assets. By successfully completing this test, individuals show their commitment to maintaining the integrity of their organization’s security framework.
Throughout the test, scenarios are presented to challenge individuals’ understanding and decision-making skills. The aim is to assess their preparedness to act appropriately in case of security threats, whether those involve phishing attempts, unauthorized data access, or network breaches. The scenarios encourage participants to think critically and apply security principles effectively under pressure.
Importance of Cybersecurity in the DoD
In any government or defense-related organization, safeguarding digital information and ensuring secure operations is of paramount importance. With sensitive data and critical systems at stake, a strong focus on protecting against malicious threats and unauthorized access is essential for maintaining operational integrity and national security. Implementing robust security measures helps to minimize risks and prevent costly breaches that could compromise the mission.
Personnel working within these organizations must be well-versed in security protocols to prevent and mitigate potential attacks. Regular training and testing ensure that all members are aware of current threats and equipped with the knowledge to recognize and respond effectively. Security practices must remain up-to-date to counter the evolving nature of digital threats, from phishing to advanced persistent threats (APT).
Here is a table showing key components of security that are emphasized in training programs:
| Security Component | Description |
|---|---|
| Data Protection | Ensuring sensitive information is encrypted and securely stored to prevent unauthorized access. |
| Threat Detection | Identifying potential threats early through monitoring tools and proactive measures. |
| Incident Response | Developing a clear plan to respond to security incidents to minimize damage and recover quickly. |
| Access Control | Managing user privileges and ensuring that only authorized personnel can access sensitive systems. |
Understanding and practicing these fundamental principles allows individuals to contribute to a secure environment, protecting vital information and maintaining the trust of both the public and stakeholders. The security of data and systems directly impacts the effectiveness of any mission and the safety of national interests.
How to Prepare for the Test

Preparation is key to ensuring success in any security-related evaluation. The goal is not just to pass the test but to gain a deep understanding of the principles and practices that are essential for safeguarding sensitive information. By studying the material thoroughly and familiarizing yourself with common scenarios, you can improve your ability to apply security protocols effectively in real-world situations.
There are several steps you can take to ensure you are fully prepared. First, it’s important to review the fundamental concepts covered in the test. This includes understanding the different types of security threats, knowing how to recognize potential risks, and learning how to respond appropriately. Additionally, practicing with sample questions or scenarios can help solidify your knowledge and build confidence.
Key Areas to Focus On
When preparing for the test, it’s important to concentrate on the following core topics:
| Topic | Description |
|---|---|
| Security Protocols | Understanding the procedures for protecting data and identifying vulnerabilities. |
| Incident Reporting | Knowing how to report security breaches or suspicious activities quickly and accurately. |
| Phishing and Scams | Recognizing fraudulent emails, links, and messages that attempt to steal personal or organizational information. |
| Access Management | Ensuring that sensitive information is only accessible by authorized individuals through secure access controls. |
Effective Study Strategies
To maximize your chances of success, consider these study strategies:
- Break down the material into manageable sections and study one section at a time.
- Take practice quizzes to familiarize yourself with the format and test your understanding.
- Review the training materials regularly to reinforce key concepts.
- Ask questions and engage with colleagues or instructors to clarify any doubts you may have.
By focusing on these strategies and dedicating time to review the material thoroughly, you’ll be well-equipped to succeed in the evaluation and demonstrate your readiness to handle security-related tasks confidently.
Common Topics Covered in the Test
When preparing for a security assessment, it’s important to focus on the key topics that are most likely to be covered. The test assesses your understanding of various principles and practices designed to protect sensitive information and ensure safe digital environments. These topics span across different areas of information security, including threat detection, response procedures, and best practices for data protection.
Key Areas of Focus
The following are some of the most common subjects you’ll encounter during the test:
- Phishing and Social Engineering: Recognizing deceptive tactics used by malicious actors to trick individuals into revealing sensitive information.
- Data Protection: Techniques for safeguarding personal and organizational data from unauthorized access or theft.
- Incident Response: Procedures for reporting and addressing potential security breaches or threats promptly and effectively.
- Access Control: Best practices for managing permissions to ensure that only authorized personnel can access sensitive systems and information.
Practical Scenarios and Threats

In addition to theoretical knowledge, the test also evaluates your ability to recognize and respond to real-world security threats. Some of the most common practical scenarios include:
- Phishing Emails: Identifying suspicious emails designed to harvest login credentials or install malicious software.
- Malware and Ransomware: Recognizing signs of malware infections and understanding the steps to take in case of an attack.
- Physical Security: Ensuring that devices and physical infrastructure are protected from unauthorized access or theft.
Familiarizing yourself with these topics will not only help you succeed in the test but also prepare you for handling security risks effectively in your day-to-day work environment.
Key Questions from the Security Evaluation
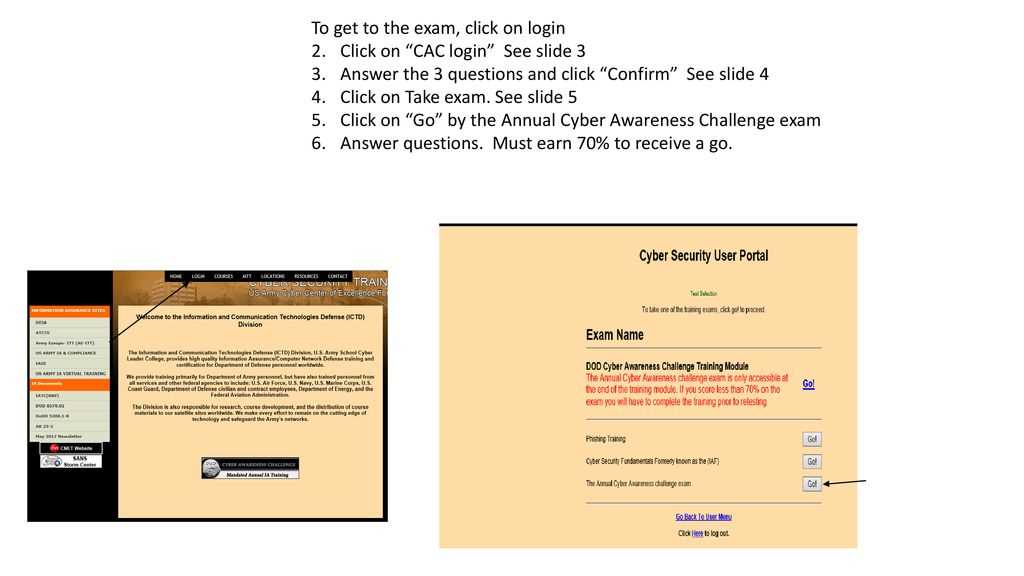
Preparing for a security assessment often requires a thorough understanding of the key principles and best practices essential for protecting sensitive information. The evaluation consists of questions designed to test your knowledge of critical topics related to digital safety, risk management, and how to recognize and respond to potential threats. The focus is on practical knowledge, ensuring that you can apply security measures effectively in real-life situations.
Commonly Asked Questions
The following are examples of some of the most frequently encountered questions in security evaluations:
- What steps should you take if you receive a suspicious email? This question tests your ability to identify phishing attempts and fraudulent communications.
- How would you respond to a data breach? This question assesses your understanding of the incident response process, including reporting and mitigation steps.
- What is the best way to secure sensitive information on your device? This evaluates your knowledge of encryption, password management, and other security protocols for protecting digital assets.
- How do you ensure safe access to restricted systems? This question examines your understanding of access control measures and the importance of managing permissions.
Scenarios to Prepare For
In addition to direct questions, the evaluation often includes scenarios where you need to apply your knowledge to potential security situations. These might include:
- Receiving a message from an unknown sender asking for confidential information. How do you handle this situation to protect sensitive data?
- Discovering that your system has been compromised by malware. What steps do you take to contain the issue and prevent further damage?
- Noticing a colleague accessing restricted areas of the network without proper authorization. How do you respond to this potential security violation?
By reviewing these types of questions and scenarios, you can better prepare for the security assessment and ensure that you are equipped to manage any risks that may arise in the workplace.
Tips for Passing the Security Evaluation
Successfully completing a security evaluation requires more than just memorizing facts. It involves understanding core principles, applying best practices, and being able to recognize and respond to real-world security threats. To ensure that you are fully prepared and can perform well on the assessment, it’s important to approach the preparation strategically and practice the skills that will be tested.
Here are some useful tips that can help you pass the security evaluation:
- Study the Fundamentals: Focus on understanding the basic concepts of information protection, risk management, and threat identification. Ensure that you can clearly explain common security terms and procedures.
- Review Common Threat Scenarios: Go through examples of typical security risks, such as phishing emails, unauthorized access, and data breaches. Know how to recognize these threats and the appropriate response protocols.
- Use Practice Materials: Test your knowledge using available practice questions or mock scenarios. This will help you get comfortable with the format of the evaluation and allow you to identify areas that need more attention.
- Understand Security Protocols: Make sure you are familiar with the security measures that protect systems and data, such as encryption, access control, and incident response procedures. The evaluation will often assess your knowledge of these essential practices.
Stay Calm and Focused: During the evaluation, take your time to read through each question carefully. Avoid rushing, and make sure you fully understand what’s being asked before selecting your answer. Many questions are designed to test your ability to think critically and apply security practices in realistic situations.
Clarify Doubts: If there are any concepts you don’t fully understand, don’t hesitate to ask questions or seek clarification. Whether through study materials, colleagues, or instructors, gaining a clear understanding of security principles is essential to performing well on the test.
By following these tips, you can increase your chances of passing the security evaluation and demonstrate your readiness to handle the responsibilities of protecting sensitive information and maintaining a secure work environment.
Security Evaluation Rules and Guidelines
When preparing for a security evaluation, it’s essential to understand the rules and guidelines that govern the assessment. These rules are designed to ensure that all participants are treated fairly and that the evaluation accurately measures their knowledge of key security principles. Adhering to these guidelines is important not only for passing the evaluation but also for maintaining a professional approach to security matters.
The following rules and guidelines are typically in place for such assessments:
- Complete the Test Independently: You are expected to complete the evaluation on your own without assistance from others. Collaboration is not permitted, and any attempts to cheat will result in disqualification.
- Time Limits: Most security evaluations have a set time limit. Be sure to manage your time wisely, reading each question carefully and answering within the allocated time frame.
- Familiarity with Topics: The evaluation will cover a range of topics related to information protection, risk management, and threat identification. It’s important to familiarize yourself with the material before taking the assessment.
- Honesty and Integrity: Ethical behavior is critical. Any attempts to manipulate or bypass the test system will result in penalties and may lead to further consequences.
- Follow Instructions: Pay close attention to any instructions provided throughout the test. Each section may have specific guidelines on how to answer or approach questions.
By following these guidelines, you ensure that the test remains a valid measure of your knowledge and your commitment to maintaining a secure environment. Proper preparation and adherence to the rules will help you succeed in the evaluation and enhance your ability to protect sensitive information.
How to Improve Your Cyber Hygiene
Maintaining strong digital habits is crucial to safeguarding personal and professional information. Proper online practices can greatly reduce the risk of falling victim to various online threats, such as phishing attacks, data breaches, and malware infections. Improving your digital hygiene involves adopting consistent, proactive steps to protect yourself and your devices in the online environment.
Essential Practices for Enhanced Security
Here are some key steps you can take to boost your security hygiene:
- Use Strong Passwords: Create unique, complex passwords for every account. Avoid reusing passwords across multiple sites to reduce the risk if one is compromised.
- Enable Two-Factor Authentication (2FA): Whenever possible, activate 2FA for an added layer of security. This ensures that even if someone obtains your password, they cannot access your accounts without the second verification step.
- Keep Software Updated: Ensure that all of your devices, applications, and security software are regularly updated. Updates often include patches that fix vulnerabilities in the system.
- Be Cautious with Emails and Links: Avoid clicking on suspicious links or downloading attachments from unknown sources. Phishing attacks are one of the most common ways that cybercriminals gain access to sensitive information.
Regular Maintenance and Monitoring
In addition to the practices above, consistent monitoring and maintenance of your devices can prevent potential threats:
- Run Regular Security Scans: Use antivirus software to scan your devices periodically for any threats or malware.
- Backup Your Data: Regularly back up important files to ensure that you can recover them in case of a cyber incident like ransomware.
- Review Privacy Settings: Review and adjust the privacy settings on your social media accounts and online services to limit the information that is publicly available.
By adopting these habits and remaining vigilant, you can significantly improve your digital hygiene and reduce your exposure to cyber threats. Practicing good habits online helps create a safer and more secure digital experience for yourself and others.
Why Regular Security Training is Crucial

In today’s digital world, threats to sensitive information and systems are more prevalent than ever. Regular training on security best practices helps individuals and organizations stay vigilant and prepared to tackle new and evolving risks. It ensures that everyone is aware of the latest threats and knows how to respond appropriately to safeguard their data and resources.
Key Benefits of Ongoing Security Training
Continuous learning about security has several key advantages:
- Stay Updated on New Threats: As new types of online threats emerge, training programs help individuals stay informed about the latest risks, including malware, phishing scams, and ransomware attacks.
- Strengthen Overall Defense: Regular training reinforces the importance of good security practices, helping employees and individuals avoid common mistakes that lead to breaches.
- Improve Incident Response: By understanding best practices and emergency procedures, individuals can react swiftly and effectively to minimize damage in the event of a security incident.
- Reduce Human Error: One of the biggest vulnerabilities in any security system is human error. Ongoing training helps people develop good habits and avoid common pitfalls that might lead to data breaches.
Fostering a Security-Conscious Culture
Regular training doesn’t just provide practical knowledge–it also fosters a culture of awareness and responsibility. When individuals understand the risks and the steps they can take to mitigate them, they are more likely to adopt secure behaviors in their daily work activities. This, in turn, enhances the overall security posture of the organization or team.
By prioritizing regular security training, organizations and individuals can build resilience against cyber threats and ensure they are well-prepared to handle potential risks. It is a proactive approach to creating a secure and reliable digital environment.
Common Mistakes to Avoid in the Evaluation

When participating in a security evaluation, it’s essential to avoid common mistakes that can hinder your performance or even disqualify you. Being mindful of these errors will help you navigate the process smoothly and ensure you provide accurate, thoughtful responses. By focusing on the critical aspects and adhering to best practices, you can improve your chances of success and gain valuable insights into security protocols.
Typical Errors to Watch Out For
Here are some of the most common mistakes individuals make during a security assessment:
- Rushing Through Questions: Taking your time to read and understand each question is essential. Rushing may lead to misinterpretation or overlooking key details that affect your answers.
- Ignoring Instructions: Every evaluation provides specific instructions for how to approach questions. Failing to follow these directions can lead to unnecessary mistakes or a misunderstanding of what is being asked.
- Skipping Review: After completing the test, take a moment to review your responses. Skipping this step can result in overlooked mistakes, such as typos or incorrect selections.
- Overthinking Answers: Sometimes, the simplest solution is the correct one. Overthinking or second-guessing yourself may cause unnecessary confusion and mistakes.
- Failing to Manage Time: Make sure you allocate enough time for each section. Spending too long on one question can prevent you from completing the entire evaluation effectively.
Strategies to Avoid These Pitfalls
To prevent these mistakes and perform at your best, consider the following strategies:
| Strategy | Benefit |
|---|---|
| Read Each Question Carefully | Avoid misinterpretation and ensure accurate answers. |
| Follow Instructions Precisely | Ensure that all requirements are met, leading to more accurate results. |
| Review Your Work | Catch errors or overlooked details before submitting. |
| Practice Time Management | Make sure to pace yourself and allocate time for every question. |
By being aware of these common pitfalls and implementing strategies to avoid them, you can increase your chances of successfully completing the evaluation. Proper preparation and thoughtful execution are key to achieving a strong performance.
How to Access Security Resources
Accessing valuable resources to strengthen your understanding of information protection is crucial for anyone involved in secure operations. These resources provide essential tools and guidelines to ensure that individuals are well-equipped to handle the latest security challenges. Whether you are part of a governmental agency or a private entity, having easy access to these materials will help you stay informed and prepared.
Steps to Access Available Materials
To effectively utilize security resources, follow these steps:
- Visit Official Websites: Many organizations and government agencies offer centralized portals where individuals can access training modules, documentation, and other educational materials related to security protocols.
- Register for Training Programs: Many platforms require users to register for specific courses before gaining access to learning materials. Ensure that you complete the registration process and follow the instructions provided.
- Utilize Online Portals: Secure online portals provide interactive learning experiences, quizzes, and informational videos to enhance your understanding. Make sure to check for resources such as manuals and FAQs.
Additional Support Options
Beyond standard training programs, there are additional support options available to assist learners in their journey:
- Interactive Communities: Join forums or groups where you can engage with peers, ask questions, and share insights on security topics.
- Webinars and Workshops: Many institutions regularly offer live or recorded webinars and workshops on relevant security topics. These sessions can provide real-time answers to pressing questions.
- Documentation and FAQs: Comprehensive documentation and frequently asked questions sections are often available to guide you through common challenges.
By following these steps and utilizing available resources, you can gain the knowledge and confidence needed to navigate security protocols and protect sensitive information.
The Role of Phishing in Security Training
Phishing is one of the most common and dangerous tactics used by cybercriminals to compromise sensitive information. By understanding how these attacks work and recognizing their signs, individuals can better protect themselves and their organizations. Educating users on the methods and risks associated with phishing is an essential part of any security program.
How Phishing Works
Phishing attacks typically involve fraudulent communication, often disguised as legitimate emails or messages, designed to trick individuals into disclosing personal or confidential information. These attacks can take many forms, including:
- Deceptive Emails: Fake emails that appear to come from trusted sources, like banks or government organizations, asking recipients to click on malicious links or provide sensitive data.
- Fake Websites: Cybercriminals create fake websites that closely resemble real ones to capture login credentials, payment information, or other personal details.
- SMS Phishing (Smishing): Similar to phishing emails, these attacks are carried out through text messages, often tricking individuals into clicking on harmful links.
Preventing Phishing Attacks
Recognizing phishing attempts and taking appropriate actions can significantly reduce the risk of falling victim to these attacks. Here are some key strategies to mitigate phishing threats:
- Verify the Source: Always check the sender’s email address, especially if the message is asking for sensitive information or seems unusual in any way.
- Look for Red Flags: Phishing messages often contain urgent language, spelling errors, or odd-looking links. Be cautious when anything seems out of place.
- Use Multi-Factor Authentication: Even if attackers manage to steal login credentials, multi-factor authentication can provide an added layer of protection against unauthorized access.
By training individuals to identify and respond to phishing attempts, organizations can strengthen their defenses against one of the most pervasive threats in the digital world.
Understanding Digital Threats and Risks
In today’s interconnected world, understanding the risks posed by various malicious activities is essential for safeguarding sensitive information and ensuring the integrity of systems. Digital threats come in many forms, from data breaches to malware attacks, and can have devastating consequences for individuals and organizations alike. Recognizing the various types of threats and the potential risks they pose is the first step in building a strong defense against them.
These risks are not limited to a specific industry or environment; they affect everyone who relies on digital tools and the internet. Whether through social engineering, software vulnerabilities, or unauthorized access, digital threats are constantly evolving. By staying informed and proactive, individuals can better protect themselves from falling victim to these attacks.
Types of Digital Threats
There are several common types of digital threats that individuals and organizations face today:
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to systems. Examples include viruses, worms, ransomware, and trojans.
- Phishing: Deceptive attempts to acquire sensitive information by pretending to be a trustworthy entity, often via email or fake websites.
- Social Engineering: Manipulative tactics used by attackers to trick individuals into revealing confidential information or performing certain actions that compromise security.
- Insider Threats: Risks posed by individuals within an organization who may intentionally or unintentionally compromise the security of the system.
Mitigating Risks and Enhancing Protection
To minimize the impact of digital threats, it’s crucial to adopt best practices and implement robust security measures. Some essential strategies include:
- Regular Software Updates: Keeping software and systems up-to-date ensures that known vulnerabilities are patched, making it harder for attackers to exploit weaknesses.
- Strong Passwords: Using complex, unique passwords and implementing multi-factor authentication helps protect access to sensitive accounts and data.
- Employee Training: Regular security training and awareness programs can help individuals recognize potential threats, such as phishing scams or social engineering tactics, and respond accordingly.
Understanding and addressing digital threats is crucial for maintaining the security of both personal and organizational information. By staying informed and implementing preventive measures, individuals can better protect themselves from the ever-present risks of the digital age.
How to Report Security Incidents
When a security breach or suspicious activity occurs, it’s crucial to report the incident promptly to prevent further damage and ensure proper mitigation. Recognizing and reporting such incidents helps organizations respond quickly and take corrective actions before any sensitive information is compromised or systems are severely impacted. Proper incident reporting not only assists in resolving the immediate issue but also aids in preventing future threats.
Clear and accurate reporting ensures that the right teams can analyze the situation and implement appropriate countermeasures. Every individual within an organization plays a vital role in identifying potential security risks and acting swiftly. Knowing how to report an incident and what information to include can make a significant difference in the response time and effectiveness of the solution.
Steps for Reporting Security Incidents
If you encounter a security issue, follow these essential steps to ensure effective reporting:
- Identify the Incident: Confirm the nature of the security issue. Is it a potential data breach, malware infection, or an unauthorized access attempt? Be as specific as possible.
- Document the Details: Record key details about the incident, including the time it occurred, the type of threat, any affected systems, and how you discovered it. This will help the response team assess the situation.
- Report to the Designated Team: Most organizations have a specific team or individual designated to handle security incidents. Report your findings directly to them, ensuring you follow the appropriate communication channels.
- Preserve Evidence: Do not attempt to fix the problem yourself unless instructed. Preserve logs, files, or any other relevant evidence that can assist the investigation.
- Follow Up: Stay engaged with the response team for updates on the status of the incident. Be ready to provide any additional information if needed.
Best Practices for Reporting
To ensure that your report is clear and helpful, consider the following best practices:
- Be Prompt: Report the incident as soon as you notice any suspicious activity. Early detection and response can significantly reduce the potential damage.
- Provide Accurate Information: The more specific and accurate your report, the easier it will be for security teams to assess the situation and take action.
- Follow Organizational Procedures: Every organization should have a predefined protocol for reporting security incidents. Familiarize yourself with these procedures to ensure you follow the correct steps.
- Maintain Confidentiality: Keep the details of the incident confidential until it is resolved. Sharing sensitive information prematurely could lead to misinformation or further security risks.
By following these guidelines, you help create a safer digital environment, ensuring swift and effective resolution of any security incidents. Proper reporting is a critical step in the overall security strategy of any organization.
Staying Up-to-Date with Security Best Practices
In an ever-evolving digital landscape, it is essential to continuously adapt to new threats and improve security measures. Keeping up with the latest trends and best practices ensures that individuals and organizations remain protected against emerging risks. Regularly updating your knowledge and skills is crucial for identifying vulnerabilities and applying the most effective defense strategies.
The dynamic nature of technology means that new threats, tools, and techniques are constantly being developed. Therefore, staying informed about security updates, practices, and technologies is a key part of reducing potential exposure to harm. Consistent learning and adaptation are vital for fostering a proactive security culture that mitigates risks before they become critical issues.
Effective Ways to Stay Informed
There are several strategies you can use to stay current with security best practices:
- Follow Industry Blogs and News: Subscribe to trusted cybersecurity blogs, news outlets, and forums where experts discuss the latest vulnerabilities, updates, and trends in security.
- Attend Webinars and Conferences: Participate in webinars, workshops, and conferences to gain insights from leading professionals in the field. These events often highlight the most pressing issues and innovations.
- Join Online Communities: Engage with online groups or communities focused on security. Collaboration with peers can provide valuable perspectives and solutions for common security challenges.
- Use Security Tools and Software: Stay updated on the latest security tools and software designed to help identify and mitigate risks. Regularly update your systems to ensure they are equipped with the latest protective features.
Ongoing Education and Training

One of the most effective ways to stay up-to-date is through continuous learning. Regular training ensures that your knowledge is aligned with the latest standards and developments in the field. Many organizations provide training programs that focus on the latest security protocols, which can be invaluable for individuals looking to stay ahead of cyber threats.
Additionally, self-paced courses, certifications, and workshops offer the opportunity to deepen your understanding of key security principles. Certifications from recognized organizations demonstrate expertise and a commitment to keeping pace with the industry’s best practices.
By staying engaged with current security trends, tools, and educational opportunities, you can significantly enhance your ability to identify and prevent potential security threats. This proactive approach helps ensure that you and your organization remain well-prepared to face any challenges in the digital world.