Keystone Packet Answers and Solutions
In any network setup, troubleshooting and resolving common communication issues are essential for ensuring smooth operations. Identifying and addressing connectivity problems can greatly improve overall system performance and efficiency. This section will explore various techniques and strategies to handle such challenges effectively.
Network integrity can be compromised by a variety of factors, ranging from misconfigurations to external interference. Understanding the core elements that impact data flow is crucial for pinpointing problems and applying the right fixes. Whether it involves adjusting settings or optimizing traffic routes, knowing the right approach can save both time and resources.
By mastering these troubleshooting methods, users can prevent disruptions and maintain optimal network health, which is crucial for both personal and business applications. The following sections will guide you through practical solutions and expert recommendations for overcoming the most common network-related difficulties.
Keystone Packet Answers

When dealing with network communication issues, it’s important to have a solid understanding of the data flow and common obstacles that can disrupt seamless transmission. Identifying the root cause of any interruptions is the first step toward resolution. This section provides insights into common troubleshooting techniques and practical solutions for improving connectivity.
Network disruptions can stem from various factors, including incorrect configurations, hardware failures, or interference. By focusing on key aspects such as signal quality, bandwidth allocation, and device compatibility, you can effectively address these problems. Understanding how data is transferred and what may cause delays or loss is critical in diagnosing and fixing issues.
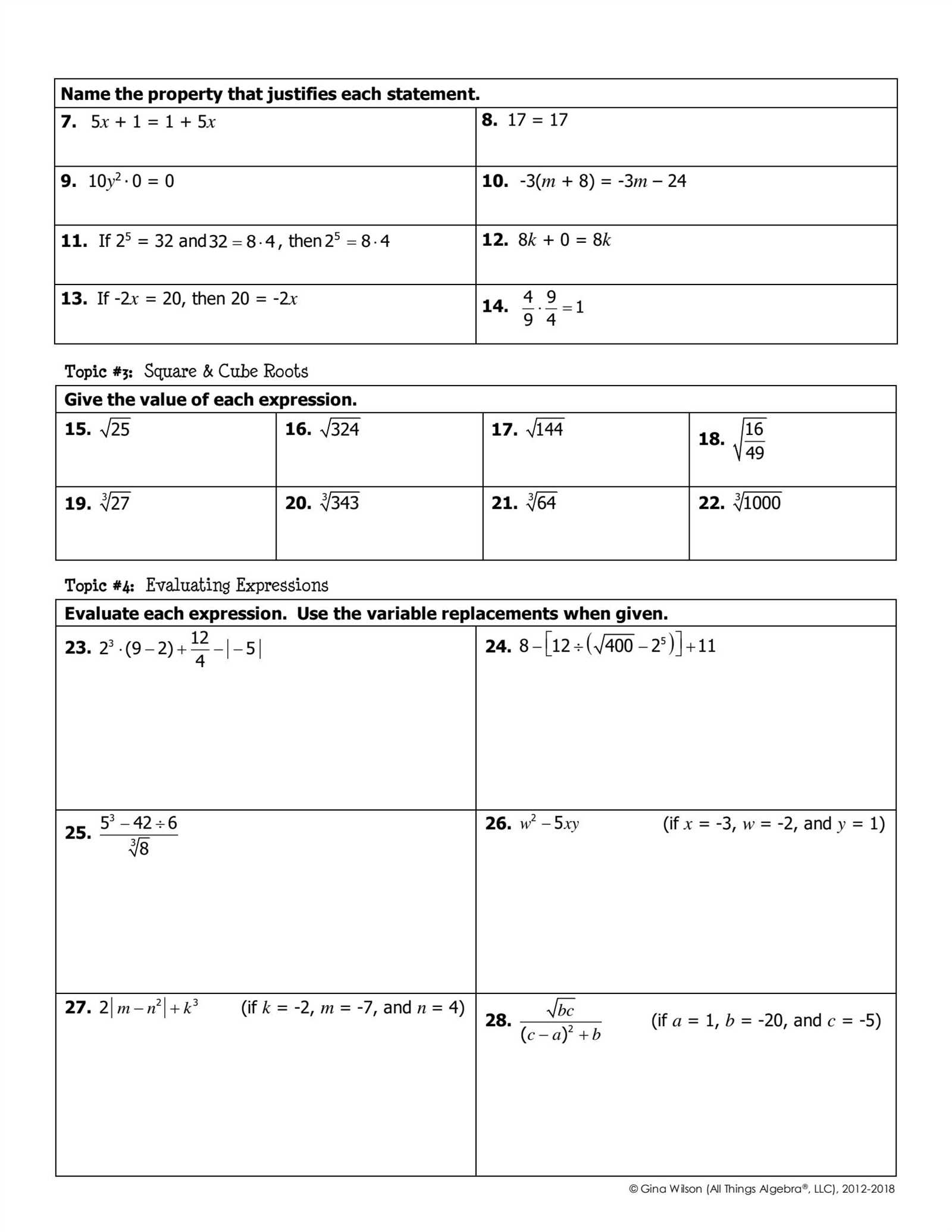
Implementing the right fixes requires a systematic approach, from examining network settings to verifying the integrity of connections. Whether you are adjusting parameters or replacing malfunctioning components, each step plays a vital role in restoring optimal functionality. This guide will help you navigate through these challenges and maintain a robust, efficient network system.
Understanding Keystone Packet Basics
At the core of any successful communication network lies the ability to send and receive data efficiently. Understanding the fundamental components that facilitate this exchange is crucial for diagnosing issues and optimizing performance. This section will explore the basic principles behind data transmission and the elements involved in ensuring smooth and uninterrupted connections.
Data transmission relies on specific protocols and structures that define how information is broken down, transmitted, and reassembled. Each piece of data must be properly formatted and routed through the network to its destination. These components work together to ensure that signals reach their intended targets without significant delay or error.
Key elements such as network topology, error correction methods, and signal integrity all play critical roles in maintaining the flow of data. By understanding these basic building blocks, network administrators and users can better identify potential weaknesses and take the necessary steps to improve reliability and speed.
Common Issues with Keystone Packets

In any network system, several factors can interfere with the smooth transmission of data. While some issues are easy to identify, others may be more subtle and require deeper analysis. Common problems often arise from configuration errors, physical disruptions, or improper handling of signals, all of which can compromise communication efficiency.
Some of the most frequent challenges encountered in these systems include:
- Data Loss: This occurs when signals fail to reach their intended destination, often due to interference or network congestion.
- Signal Degradation: Poor signal strength can result in slow data transfer or frequent disconnections.
- Configuration Errors: Incorrect settings or misconfigured devices can cause communication breakdowns.
- Latency Issues: Delays in transmission can lead to slow response times and poor user experience.
- Compatibility Problems: Devices or systems that are incompatible may struggle to communicate properly, leading to failures in data exchange.
Identifying the root cause of these issues requires careful troubleshooting, focusing on both hardware and software components. Addressing these common problems can significantly improve network performance and ensure more reliable data transmission.
How to Troubleshoot Keystone Packets
When communication issues arise in a network, the key to resolving them quickly lies in a structured troubleshooting approach. Identifying the source of problems requires a methodical process that addresses both hardware and software components. This section outlines effective steps to diagnose and resolve common network-related challenges.
Begin by checking the basic setup, ensuring that all devices are properly connected and powered on. Network cables and connectors should be inspected for any visible signs of wear or damage. Sometimes, physical issues like loose connections or faulty equipment can be the root cause of disruptions.
Next, verify the configuration settings. Incorrect configurations, such as mismatched IP addresses, wrong subnet masks, or faulty routing protocols, can lead to significant problems. Use diagnostic tools like ping tests or traceroute to check the health of the network and identify any bottlenecks or failures in the transmission path.
If issues persist, examine network traffic for congestion or excessive load. Monitoring software can help detect unusually high data volumes that may cause delays or loss. In some cases, adjusting traffic management settings or upgrading network infrastructure may be necessary to restore optimal performance.
Lastly, ensure that firmware and software updates are up to date. Outdated software can introduce vulnerabilities or compatibility issues that hinder smooth data exchange. By following these troubleshooting steps, most common network problems can be resolved effectively, leading to improved reliability and performance.
Identifying Packet Loss Problems

One of the most common issues in a network is the loss of data during transmission. This problem can cause significant delays, interruptions, and poor overall performance. Identifying the cause of lost data requires a careful approach, as there are several factors that could lead to such disruptions.
Packet loss typically occurs when data fails to reach its destination, either due to network congestion, poor signal quality, or faulty hardware. When this happens, users may experience slow load times, lag during online activities, or complete failures in communication. Understanding how to detect and pinpoint this problem is crucial for effective resolution.
One of the first steps in identifying packet loss is to run diagnostic tools such as ping tests or traceroute. These tools help determine if data is being lost during transit and at what point the failure occurs. A high number of dropped packets during these tests is a strong indication of a problem in the network path.
Additionally, network monitoring tools can help track real-time data flow and detect irregularities in performance. By observing the behavior of data packets as they move through the system, it’s possible to identify patterns and locate the source of the issue, whether it’s a router, switch, or cable.
Once the cause of packet loss has been identified, steps can be taken to resolve it, such as optimizing the network, replacing faulty hardware, or adjusting settings to manage traffic more effectively. Understanding and addressing packet loss issues is key to maintaining a smooth, high-performance network.
Resolving Network Latency with Keystone

Network latency, or the delay in data transmission, can significantly impact the overall performance of a system. Slow response times can lead to frustrating user experiences, especially in environments requiring real-time communication. Addressing latency involves identifying the causes of delays and implementing solutions to streamline data flow.
Several factors contribute to network latency, including:
- Network Congestion: High levels of traffic can cause bottlenecks, slowing down the transmission speed and increasing delays.
- Distance: The physical distance between devices can impact how long it takes for data to travel from one point to another.
- Device Performance: Older or underperforming hardware may struggle to process data quickly enough, contributing to delays.
- Protocol Overhead: Some communication protocols introduce additional processing time, which can increase latency.
To effectively reduce latency, start by evaluating the network’s architecture. Consider optimizing the configuration of routers and switches, ensuring that data takes the most efficient path through the network. You may also want to prioritize traffic for latency-sensitive applications to ensure they are not impacted by other network activities.
Another key step is upgrading hardware, particularly routers, switches, or any other network components that may be causing delays due to age or inefficiency. Using high-performance devices can significantly reduce response times and enhance overall system performance.
Additionally, employing techniques such as traffic shaping and quality of service (QoS) can help allocate bandwidth more effectively, reducing congestion and improving latency for critical applications. By implementing these strategies, it is possible to minimize delays and enhance the speed and efficiency of your network.
Configuring Keystone Packets for Performance
Optimizing network traffic is crucial for ensuring high performance and efficiency in any system. Proper configuration of data transmission elements plays a key role in maintaining fast, reliable communication. By fine-tuning settings and addressing potential bottlenecks, it’s possible to significantly enhance overall network performance.
Network Configuration and Optimization
One of the first steps in improving performance is to configure the network devices properly. This includes setting optimal routing paths, adjusting MTU (Maximum Transmission Unit) sizes, and ensuring that hardware components such as switches and routers are capable of handling high data volumes. Reducing unnecessary traffic and eliminating inefficiencies in routing can lead to faster data flow and reduced latency.
Managing Bandwidth and Traffic Prioritization
Traffic management plays an important role in maintaining performance, especially in networks with high traffic loads. Implementing Quality of Service (QoS) settings allows for prioritizing important data streams, ensuring that critical traffic receives the necessary bandwidth. In addition, bandwidth allocation tools can help prevent congestion, making sure that each type of communication gets the resources it needs without causing delays.
Through these configurations, networks can be optimized for speed, reducing delays and improving reliability for all users. Ensuring that the data transmission process is streamlined and well-managed is key to maintaining a high-performance network that can handle diverse demands.
How to Fix Keystone Packet Errors
Network communication errors can disrupt the smooth flow of data, leading to poor performance and delays. These issues are often caused by misconfigurations, hardware malfunctions, or external interference. Understanding how to identify and address these errors is essential for restoring optimal network functionality.
Identifying the Source of Errors
The first step in resolving network errors is to identify the root cause. Start by running diagnostic tools such as ping tests or traceroutes to pinpoint where the communication failure occurs. A high rate of failed transmissions or dropped signals may indicate a specific issue, such as a faulty router or damaged cables. Once you have located the source, you can take the necessary steps to correct the issue.
Correcting Configuration and Hardware Issues
If the error stems from a configuration problem, ensure that network settings, such as IP addresses, subnet masks, and routing protocols, are correctly configured. Incorrect settings can often prevent proper data flow between devices. For hardware-related issues, inspect all physical components, such as switches, routers, and cables, to ensure they are functioning properly. Replacing damaged equipment or updating firmware may also resolve underlying issues that affect performance.
By carefully analyzing the problem and following these corrective steps, you can resolve errors and restore smooth, efficient communication within the network. Regular maintenance and monitoring are also recommended to prevent future issues from arising.
Keystone Packet Security and Encryption
In today’s interconnected world, protecting data during transmission is crucial to ensuring privacy and integrity. Security measures, such as encryption, play a vital role in safeguarding sensitive information from unauthorized access or tampering. When transmitting data over a network, it is essential to apply strong security protocols to protect against various threats, including eavesdropping, man-in-the-middle attacks, and data breaches.
Encryption is one of the most effective ways to secure data in transit. By converting data into an unreadable format, it ensures that even if intercepted, the information remains protected. Various encryption methods, such as SSL/TLS for web traffic or IPsec for network communications, can be applied depending on the requirements of the network and the sensitivity of the transmitted data.
Additionally, network security practices should include proper authentication, access control, and monitoring to detect and prevent malicious activities. Regularly updating encryption protocols and ensuring that network components are compliant with industry standards are also essential steps to maintain a secure environment.
Implementing robust security measures for data transmission not only protects sensitive information but also enhances trust in the network’s reliability and integrity. With the right encryption techniques and best practices in place, organizations can ensure that their communications remain secure and resilient against evolving cyber threats.
Improving Data Integrity with Keystone
Ensuring the accuracy and consistency of data during transmission is essential for maintaining the reliability of a network. Data integrity refers to the protection of data from corruption, loss, or unauthorized modifications. By implementing the right strategies and tools, it is possible to safeguard the data exchange process, ensuring that information remains intact and trustworthy across systems.
Key Methods for Enhancing Data Integrity
Several methods can be employed to improve data integrity, from checksum verification to encryption. Below are some of the most effective approaches:
| Method | Description | Benefits |
|---|---|---|
| Checksums | Using algorithms to generate a unique value for data to detect errors during transmission. | Quick error detection, low computational cost. |
| Hash Functions | Generating a fixed-size hash from variable-length data to verify its integrity. | Provides a strong guarantee of data consistency and authenticity. |
| Encryption | Encrypting data to prevent unauthorized modifications and access. | Secures data, preventing tampering and unauthorized interception. |
| Redundancy | Sending duplicate copies of data over multiple paths to ensure it reaches its destination intact. | Improves reliability and minimizes the impact of network failures. |
Ensuring Long-Term Data Reliability

In addition to these methods, ensuring data integrity involves regular monitoring and testing of the systems and protocols in place. Data audits and error-checking mechanisms should be implemented to continually assess the reliability of data transactions. With the right measures, data integrity can be enhanced significantly, ensuring that the information exchanged within a network remains accurate, uncorrupted, and secure over time.
Testing Keystone Packet Connectivity
Ensuring the connectivity of network components is essential for maintaining reliable communication across systems. Connectivity testing involves evaluating how well data is transmitted between devices and identifying any issues that may disrupt the flow of information. By thoroughly testing the network’s performance, it is possible to diagnose potential connectivity problems and take appropriate measures to resolve them.
Connectivity tests typically focus on several key aspects, including signal strength, latency, bandwidth, and error rates. Tools such as ping tests, traceroutes, and throughput measurements are commonly used to evaluate network performance and ensure smooth communication. These tests help identify any disruptions, bottlenecks, or inefficiencies that could impact data transmission.
Regularly testing connectivity not only helps prevent issues but also allows for ongoing optimization of network performance. By performing these tests proactively, organizations can maintain high levels of reliability and address potential challenges before they affect system functionality.
Managing Keystone Packets in Large Networks
Managing data transmission in large-scale networks presents unique challenges due to the complexity and volume of communication between multiple devices. As the network grows, maintaining efficient and error-free data flow becomes increasingly difficult. Proper management of data traffic ensures that all network components can communicate seamlessly, minimizing delays and preventing data loss.
In large networks, it is crucial to implement strategies that prioritize data flow, monitor network health, and optimize resource allocation. Tools for traffic analysis, such as network monitoring systems, can help administrators detect bottlenecks, congestion points, and potential failures. Additionally, segmentation and proper routing protocols allow for better control over the flow of data and the ability to scale as needed without sacrificing performance.
Effective management also involves regularly updating network components, ensuring all devices are configured correctly, and performing routine tests to assess connectivity and performance. By leveraging automated systems and best practices, network administrators can maintain a high level of reliability and responsiveness, even in highly complex environments.
Optimizing Keystone Packets for Speed
Enhancing the speed of data transmission across a network is critical to ensure efficient communication and minimize latency. Optimizing data flow allows for faster processing, reduces delays, and improves overall network performance. To achieve this, various strategies can be implemented to ensure that data is transmitted as quickly and smoothly as possible without unnecessary interruptions or bottlenecks.
Techniques for Speed Optimization
Several techniques can help improve the speed of data transmission, including:
- Compression: Reducing the size of the data being transmitted minimizes the amount of information that needs to be sent, allowing for faster transfers.
- Quality of Service (QoS): Prioritizing time-sensitive data ensures that critical information is transmitted first, reducing the chances of delays for high-priority applications.
- Reducing Protocol Overhead: Optimizing communication protocols can eliminate unnecessary steps, reducing the time spent on packet handling and increasing throughput.
- Load Balancing: Distributing data across multiple paths or servers helps prevent network congestion and ensures that no single point becomes a bottleneck.
Ensuring Consistent High-Speed Performance
In addition to these techniques, continuous monitoring and periodic optimization are essential to maintain high-speed data flow. By regularly testing network performance, identifying bottlenecks, and adjusting configurations, organizations can ensure that their networks remain fast and responsive, even as demand increases. Proper maintenance and proactive management are key to sustaining optimal performance over time.
Keystone Packets and Network Monitoring
Effective network monitoring is essential for ensuring the smooth operation of communication systems. By tracking data traffic and identifying any anomalies, network administrators can detect and resolve issues before they escalate. Monitoring tools allow for real-time visibility into the flow of information across the network, providing insights into performance, bottlenecks, and potential vulnerabilities.
Key Metrics for Monitoring Network Traffic
To assess the health and efficiency of a network, administrators focus on several key performance indicators (KPIs). These metrics help evaluate the flow of information and ensure the network is functioning optimally:
| Metric | Description | Importance |
|---|---|---|
| Latency | The delay in data transmission between devices | Low latency ensures faster communication |
| Bandwidth Utilization | The amount of data transmitted relative to the network’s capacity | Helps identify potential congestion or underutilization |
| Error Rates | The frequency of errors in data transmission | Indicates issues with data integrity or hardware faults |
| Packet Loss | The percentage of data lost during transmission | High packet loss can severely impact network performance |
Tools for Network Monitoring
There are various tools available for monitoring and analyzing network traffic. These tools provide real-time data and diagnostic capabilities, helping administrators quickly identify and troubleshoot issues. Some commonly used network monitoring tools include:
- Wireshark: A network protocol analyzer that captures and inspects packets in real-time, providing detailed insights into network performance.
- PingPlotter: A tool that visually represents latency and packet loss across the network, helping to identify performance bottlenecks.
- SolarWinds Network Performance Monitor: A comprehensive tool for monitoring bandwidth, latency, and network health across large networks.
- PRTG Network Monitor: A tool that offers detailed reports on network performance, traffic analysis, and error detection.
Understanding Packet Size Limitations
In the realm of network communication, the size of the data units being transmitted plays a crucial role in both performance and efficiency. The limitations on data unit sizes are determined by several factors, including the hardware, protocols, and network infrastructure in use. These limitations can impact network throughput, latency, and error rates, making it essential to understand how to optimize the size of the data being transmitted.
When data is transferred across a network, it is broken down into smaller chunks, each with a specific size. This size is influenced by the maximum transmission unit (MTU) of the network’s hardware and the specific protocol being used. Exceeding the optimal data size can lead to issues such as fragmentation, inefficiency, and delays in transmission. Understanding these limitations is key to ensuring smooth communication between devices.
| Limitation | Description | Impact |
|---|---|---|
| Maximum Transmission Unit (MTU) | The largest size of a data unit that can be transmitted over the network | Exceeding the MTU causes fragmentation, which can reduce network performance |
| Protocol Overhead | The extra data required for routing, error-checking, and control information | Excessive overhead reduces the efficiency of the data transfer |
| Network Topology | The physical and logical layout of the network infrastructure | Certain network topologies may impose stricter limits on data unit sizes |
| Device Limitations | The hardware capabilities of network devices such as routers and switches | Devices with lower processing power may struggle with larger data units |
By optimizing the size of data units based on these limitations, network administrators can improve efficiency and minimize network congestion. Balancing the need for larger data units and the constraints of network infrastructure ensures that data is transmitted in the most effective manner possible.
Keystone Packet Compatibility Issues
In complex network environments, ensuring that data units are compatible across various devices and protocols is critical for maintaining seamless communication. Compatibility issues can arise when different network devices or systems fail to align on how data is processed, transmitted, or received. These problems can lead to inefficiencies, delays, and even failures in data transmission, negatively impacting overall network performance.
There are several factors that contribute to compatibility issues within network configurations. These include differences in protocol support, hardware capabilities, and network configurations. Often, the mismatch between these elements can result in data corruption, loss, or delays, which can severely affect the reliability of the system. Identifying and addressing compatibility problems is essential for ensuring that data is processed and transmitted accurately across diverse network devices.
Some common causes of compatibility issues include:
- Protocol Incompatibility: Different devices or systems may use incompatible communication protocols, leading to miscommunication or failure in data transmission.
- Hardware Limitations: Network devices with outdated hardware may not support the latest transmission technologies or standards, causing performance bottlenecks or data losses.
- Configuration Mismatches: Misconfigured network settings, such as MTU sizes or addressing schemes, can result in inconsistent data flows.
- Version Discrepancies: Software or firmware versions on devices might not be compatible, preventing proper data exchange.
Addressing these issues involves thorough testing, upgrading hardware when necessary, and ensuring that all devices adhere to a common communication standard. Regular audits of network components, software updates, and proper configuration can help avoid compatibility problems, ensuring smooth and efficient data transfer across all devices in the network.
Best Practices for Keystone Packet Usage
When working with network communication protocols and data transfer, following best practices is essential to ensure efficiency, security, and reliability. Proper implementation of data transmission methods helps minimize errors, optimize performance, and maintain smooth communication between different devices. By adhering to industry standards and proven techniques, network administrators can ensure that data flows seamlessly through their systems while reducing potential disruptions.
Key Guidelines for Optimizing Network Performance
- Standardize Data Formats: Ensure all devices on the network are using compatible formats for data exchange. This reduces the chances of errors caused by format mismatches.
- Use Efficient Protocols: Choose lightweight and well-supported protocols that are known to optimize data transmission, avoiding unnecessary overhead.
- Optimize Data Chunk Sizes: Adjust the size of data packets to match the capabilities of the network and devices involved. This helps avoid fragmentation and improves efficiency.
- Maintain Proper Error Handling: Implement robust error detection and correction mechanisms to address issues promptly without interrupting data flow.
- Monitor Network Traffic: Regularly analyze network traffic to detect potential bottlenecks or inefficiencies, allowing for timely adjustments.
Security Considerations for Safe Data Exchange
- Encrypt Sensitive Data: Use encryption methods to protect data in transit, ensuring that sensitive information is not exposed to unauthorized parties.
- Authenticate Devices: Ensure that all devices in the network are authenticated before allowing them to send or receive data, preventing unauthorized access.
- Apply Regular Software Updates: Keep all devices and systems up to date with the latest security patches to mitigate vulnerabilities that could be exploited.
- Limit Access to Data: Use access control measures to restrict who can send and receive data, protecting against unauthorized data manipulation.
By implementing these best practices, network administrators can improve both the performance and security of their systems. A consistent approach to managing data transmission and securing the network will help maintain a reliable and efficient environment for all users involved.