9.2.2.6 Lab Answers and Solutions for Networking
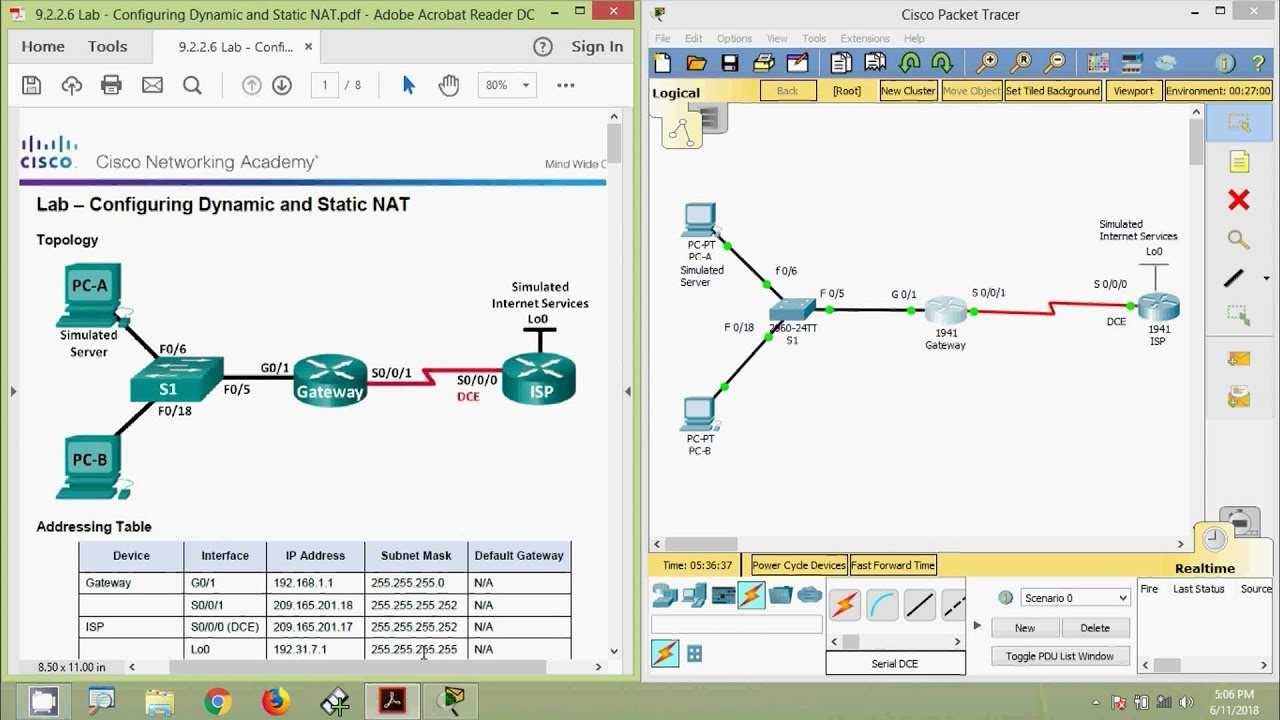
In this section, we explore a hands-on approach to understanding essential networking concepts through practical exercises. These activities are designed to enhance your ability to configure and troubleshoot various network devices and protocols effectively. By engaging with the content, you will develop a deeper understanding of how to apply theoretical knowledge in real-world scenarios.
Successful completion of these tasks requires careful attention to detail and a strong grasp of the fundamentals. As you progress, you will encounter key challenges that will help you refine your problem-solving skills. This process not only boosts your technical capabilities but also prepares you for more advanced networking tasks and certifications.
Effective troubleshooting and network configuration are vital skills for any IT professional. Mastering these activities ensures you can navigate complex network setups with confidence and precision, whether in a classroom environment or a professional setting.
6 Task Solutions Overview
This section provides a comprehensive overview of the solutions for a series of practical networking exercises. The goal is to guide you through each step, highlighting key concepts and procedures necessary to complete the exercises successfully. By following the outlined steps, you’ll gain a clearer understanding of network configuration, troubleshooting, and protocol management.
Key Objectives of the Exercises
The exercises aim to reinforce core networking principles by requiring you to implement configurations and resolve common issues. They emphasize practical skills such as device setup, command-line usage, and traffic analysis, which are essential for working in real-world network environments.
Approach to Problem Solving
Each solution follows a structured approach to problem-solving. The tasks are broken down into manageable steps that allow you to focus on understanding the underlying principles, rather than just completing the task. By tackling these challenges, you will improve your ability to think critically and troubleshoot effectively.
Understanding Networking Basics in the Exercise
This section focuses on the foundational concepts necessary for mastering network configuration and troubleshooting. It introduces key networking elements such as devices, protocols, and addressing schemes. By understanding these basics, you will be equipped to configure and manage networks efficiently in real-world scenarios.
The core of the exercise revolves around familiarizing yourself with essential tools and commands used in network setup. This knowledge allows you to establish and maintain reliable communication between devices, ensuring that networks run smoothly and issues are resolved quickly. Grasping these principles forms the bedrock for more advanced network tasks and certifications.
Key Concepts Covered in the Exercise
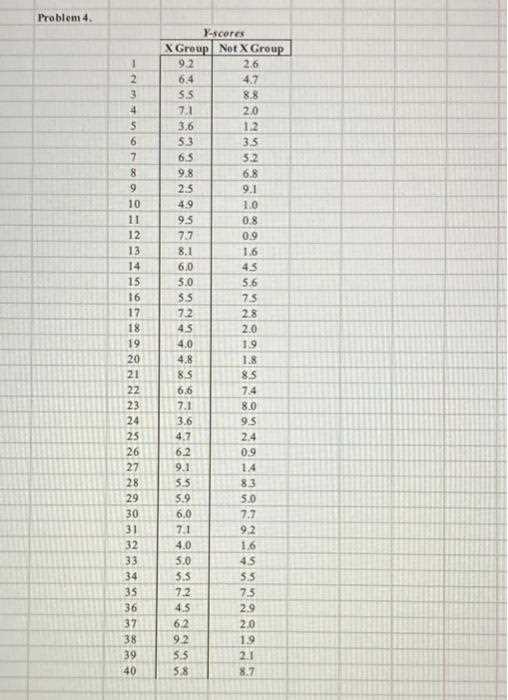
This section highlights the essential networking concepts that are explored in the practical exercise. The focus is on understanding the various components involved in network configurations, from device setup to troubleshooting common connectivity issues. Key topics include network addressing, protocol management, and the use of commands for effective configuration.
| Concept | Description |
|---|---|
| Network Addressing | Understanding IP addressing and subnetting to correctly configure network devices. |
| Device Configuration | Setting up routers, switches, and other networking devices for communication. |
| Protocol Management | Managing communication protocols like TCP/IP to ensure efficient data transfer. |
| Troubleshooting | Identifying and resolving common network connectivity issues. |
These concepts are essential for building a strong foundation in network administration, and mastering them will enable you to handle more advanced networking tasks with confidence.
Step-by-Step Guide to Completing the Exercise
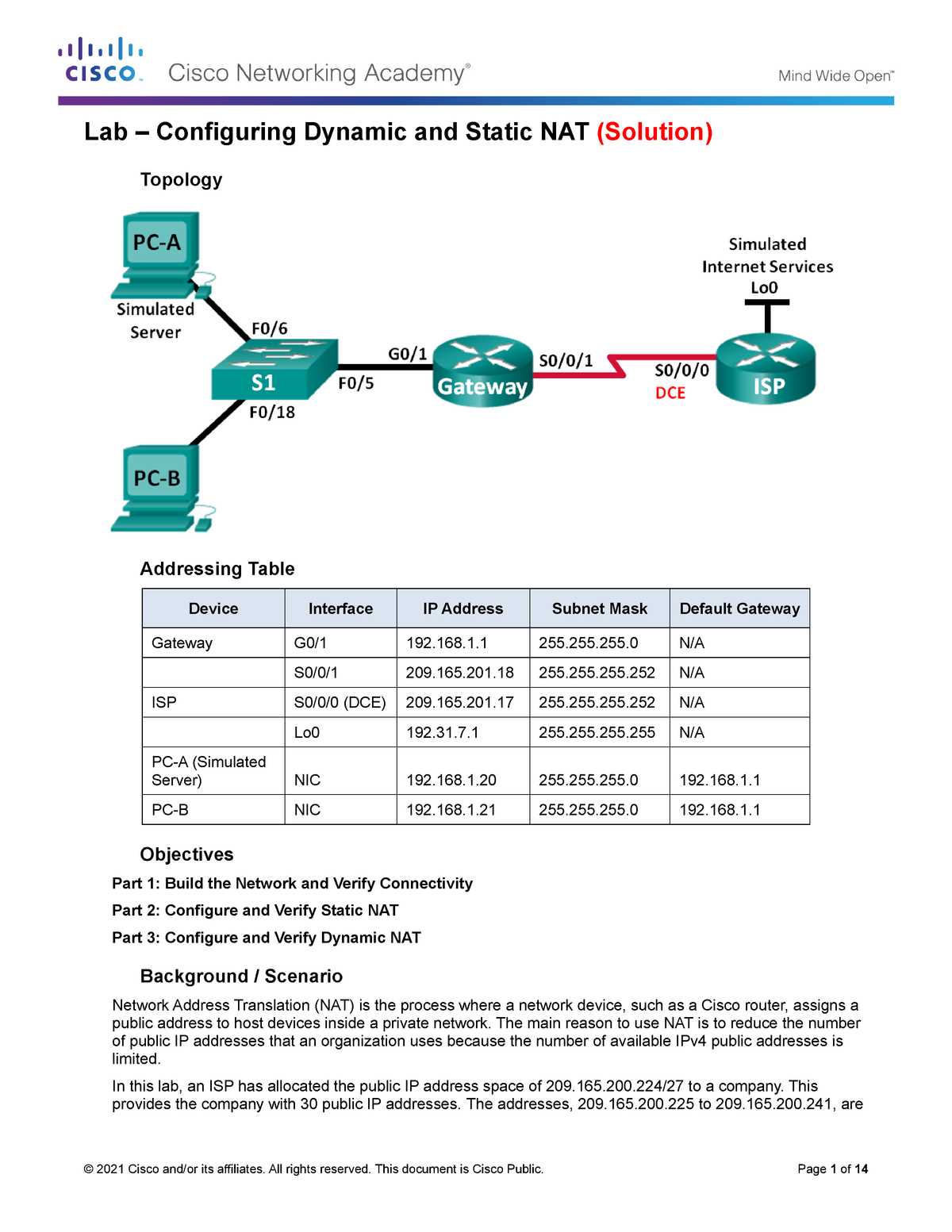
This section provides a detailed walkthrough of how to complete the practical networking tasks. It breaks down the process into manageable steps, ensuring that each phase of the configuration and troubleshooting is clearly understood. By following this guide, you’ll learn the correct sequence of actions needed to achieve a successful network setup.
Preparation and Initial Setup
Before beginning the exercise, it’s important to prepare the necessary devices and ensure that all configurations align with the required network topology. This phase includes verifying network interfaces, ensuring connectivity, and checking the configuration settings for each device involved.
Configuring Devices and Verifying Setup
Once the devices are in place, proceed with the configuration. Each device must be set up correctly to communicate within the network. After configuration, verification steps will ensure that the devices are connected and functioning as expected. Troubleshooting techniques may also be applied at this stage if any issues arise.
| Step | Action | Expected Outcome |
|---|---|---|
| Step 1 | Prepare devices and check connections | Devices should be physically connected and powered on |
| Step 2 | Configure IP addressing and protocols | Network devices should have correct IP addresses and protocol settings |
| Step 3 | Verify connectivity with ping tests | Devices should be able to communicate without errors |
| Step 4 | Troubleshoot and resolve any issues | All issues should be resolved, ensuring full network functionality |
By following these steps, you will gain valuable hands-on experience and develop the skills necessary to tackle more complex network setups in the future.
Common Challenges in the Exercise
During the completion of practical networking tasks, several common issues may arise that can hinder progress or cause confusion. These challenges typically involve misconfigurations, connectivity problems, or difficulty in troubleshooting network devices. Understanding these obstacles and how to overcome them is key to successfully completing the exercise and improving networking skills.
Here are some of the most frequently encountered difficulties:
- Incorrect IP Addressing: Assigning the wrong IP address or subnet mask can prevent devices from communicating properly within the network.
- Device Configuration Errors: Misconfiguring network devices such as routers and switches can lead to connectivity failures and performance issues.
- Protocol Mismatches: Using incompatible communication protocols can disrupt data transfer and prevent devices from syncing correctly.
- Connectivity Issues: Physical connection problems, such as loose cables or incorrect port assignments, can lead to network disruptions.
- Misunderstanding Command Syntax: Incorrect or incomplete command entries can cause configuration failures or unexpected results.
To address these challenges, it’s important to follow a systematic troubleshooting process, verify all settings, and test connections step by step. By identifying the root causes and applying solutions, you will gain confidence in network management and enhance your problem-solving abilities.
Tips for Solving Exercise Problems
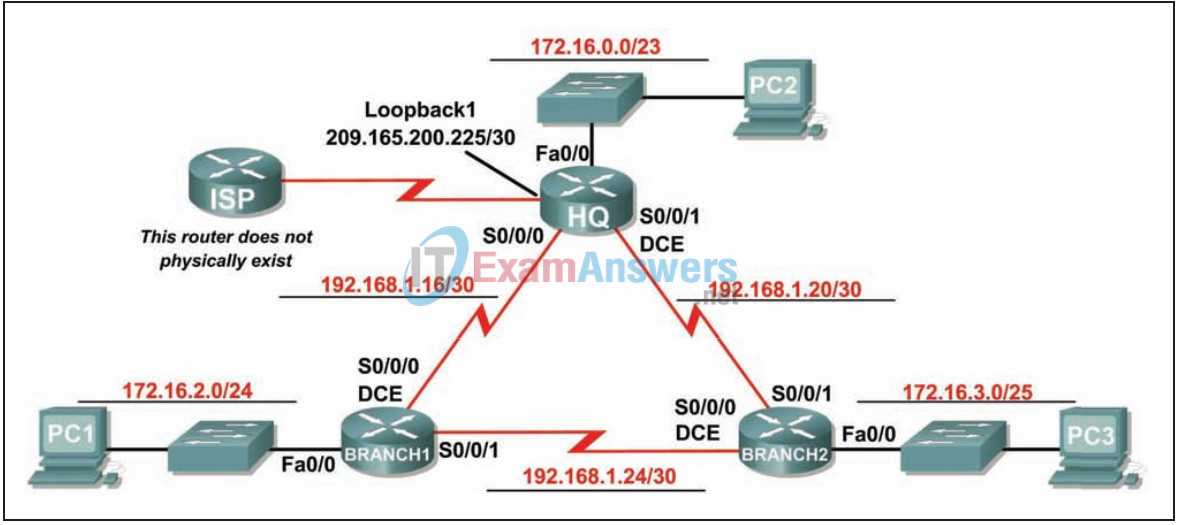
When tackling networking exercises, it is essential to approach the tasks systematically to identify and resolve any issues effectively. Many problems can be traced back to common configuration mistakes or overlooked details. By following a few key tips, you can streamline the process, reduce errors, and improve your troubleshooting skills.
- Double-Check Configurations: Ensure all network settings, such as IP addresses, subnet masks, and gateway configurations, are entered correctly. Small mistakes can prevent devices from communicating properly.
- Use Command-Line Tools: Leverage tools like
ping,tracert, andipconfigto verify connectivity and troubleshoot issues efficiently. - Verify Physical Connections: Sometimes, the issue lies with cables or ports. Ensure all devices are properly connected and powered on.
- Work Step-by-Step: Break down the task into smaller steps. Test each configuration change to verify its impact before moving on to the next.
- Consult Documentation: Review device manuals, protocol specifications, or any related resources to ensure the correct commands and settings are used.
By staying methodical and focused on each task, you can solve problems efficiently and gain a deeper understanding of the networking concepts involved.
How to Configure Network Devices
Configuring network devices is a crucial step in establishing a functional network. Whether you are setting up routers, switches, or other devices, proper configuration ensures that the network runs efficiently and securely. This process typically involves setting up IP addressing, configuring routing protocols, and testing the network connections to ensure everything is functioning as expected.
Below is a general process for configuring network devices:
| Step | Action | Expected Outcome |
|---|---|---|
| Step 1 | Power on and connect the devices | Devices should be powered up and connected via appropriate cables. |
| Step 2 | Assign IP addresses and subnet masks | Each device should have a unique IP address and appropriate subnet mask configured. |
| Step 3 | Configure routing protocols (if applicable) | Routing protocols such as RIP, OSPF, or EIGRP should be set up to allow for proper network routing. |
| Step 4 | Test connectivity using ping and traceroute | Devices should be able to communicate with each other, and the network should show no connectivity issues. |
| Step 5 | Troubleshoot if necessary | Any issues found during testing should be identified and resolved (e.g., incorrect configuration or physical connection issues). |
By following these steps and verifying each stage, you ensure that your network devices are configured correctly, allowing for seamless communication and network functionality.
Networking Protocols and Their Use
Networking protocols are essential for enabling communication between devices within a network. These protocols define the rules and conventions for data transmission, ensuring that devices can exchange information accurately and efficiently. Different protocols serve different purposes depending on the type of communication and the requirements of the network.
Common Networking Protocols
Several networking protocols are widely used to manage various aspects of communication. Here are some of the most important ones:
- Transmission Control Protocol (TCP): Ensures reliable, ordered data transmission between devices, making it ideal for applications like web browsing and email.
- User Datagram Protocol (UDP): A faster but less reliable protocol compared to TCP. It is used for applications that require speed, such as video streaming or online gaming.
- Internet Protocol (IP): Handles the addressing and routing of data packets across the network, allowing devices to locate each other and communicate.
- Hypertext Transfer Protocol (HTTP): Governs the communication between web browsers and web servers, facilitating the retrieval of web pages.
- Simple Mail Transfer Protocol (SMTP): Used for sending and receiving email messages between mail servers.
- Dynamic Host Configuration Protocol (DHCP): Automatically assigns IP addresses to devices on a network, ensuring proper addressing without manual configuration.
Choosing the Right Protocol
The choice of protocol depends on the specific needs of the application and the network. For example, if data integrity and reliable communication are critical, TCP is preferred. On the other hand, for applications that prioritize speed over reliability, such as live video or voice calls, UDP is often the better option. Understanding the strengths and limitations of each protocol helps network administrators configure their systems for optimal performance and reliability.
Troubleshooting Network Configuration Issues

Network configuration issues are common and can arise for various reasons, such as incorrect settings, connectivity problems, or miscommunication between devices. Identifying and resolving these issues is crucial for maintaining a stable and functional network. This section will cover common troubleshooting techniques and approaches to help diagnose and fix common network configuration errors.
Common Network Configuration Problems
Several common issues can prevent network devices from functioning as expected. Here are some typical problems to look out for:
- Incorrect IP Addressing: Devices may not be able to communicate if IP addresses are misconfigured or fall outside the correct subnet range.
- Subnet Mask Misconfiguration: An incorrect subnet mask can cause routing issues, preventing devices on the same network from recognizing each other.
- Gateway Configuration Errors: If the default gateway is set incorrectly, devices may be unable to reach other networks, such as the internet.
- DNS Resolution Failures: Incorrect DNS settings can lead to the inability to resolve domain names, making it difficult to access websites or services by name.
- Incorrect VLAN or Port Configuration: Network switches may not route traffic correctly if VLANs or ports are misconfigured, causing communication failures.
Troubleshooting Steps
To effectively troubleshoot network configuration issues, follow these steps:
- Verify Basic Connectivity: Use commands like
pingandtracertto test the network connection and identify any immediate issues. - Check IP and Subnet Settings: Ensure that the IP addresses, subnet masks, and gateways are properly assigned and match the network’s configuration.
- Inspect Network Cables and Connections: Physical connectivity problems, such as loose cables or incorrect ports, are often the root cause of connectivity issues.
- Review Device Configurations: Double-check the configurations on all involved devices, ensuring they are set up correctly and aligned with network requirements.
- Check for Firewall or Security Software Interference: Firewalls or security settings may block network traffic, preventing proper communication. Temporarily disable them to see if they are causing issues.
By systematically following these troubleshooting steps, most network configuration problems can be identified and resolved efficiently, ensuring smooth communication across the network.
Testing and Verifying Solutions
Once network configurations or system setups have been implemented, it is essential to test and verify that everything is functioning correctly. Verifying solutions ensures that all settings are applied correctly and that the devices communicate as expected. The process of testing also helps identify potential issues and address them before they cause disruptions.
Methods for Testing Solutions
There are several tools and techniques available for testing network setups and configurations. Here are the most commonly used methods:
- Ping: This tool is used to check connectivity between devices. By sending ICMP Echo Requests, it confirms whether a device is reachable on the network.
- Traceroute: Traceroute helps to trace the path that packets take through the network, identifying any delays or bottlenecks in the communication route.
- IP Configuration Verification: Tools like
ipconfigon Windows orifconfigon Linux can be used to check that IP addresses, subnet masks, and gateways are set correctly. - Connectivity Tests: Manually testing network services such as DNS resolution and HTTP requests can help ensure that specific services are functioning properly.
Verifying Device and Network Settings
It is crucial to verify all settings on network devices to confirm they align with the intended configuration. This includes checking:
- Device IPs: Ensure that the devices have the correct IP addresses assigned and are in the proper subnet.
- Routing Protocols: Verify that any routing protocols (e.g., RIP, OSPF, EIGRP) are configured correctly and functioning as expected.
- Firewall Settings: Check that firewalls are not blocking essential traffic between devices or subnets.
- VLAN Configurations: Verify that Virtual LANs are set up correctly, ensuring proper segmentation of network traffic.
By thoroughly testing and verifying all aspects of the setup, administrators can ensure a reliable and stable network environment.
Key Commands and Syntax
In network configuration and troubleshooting tasks, understanding and using the correct commands is crucial for managing devices effectively. The commands allow administrators to test, configure, and verify network settings, ensuring smooth communication between devices. This section highlights some of the essential commands and syntax used in networking tasks, focusing on their purpose and practical applications.
Here are some key commands commonly used in network management:
- Ping: This command is used to test the reachability of a device on the network. It sends ICMP Echo Requests and waits for a response, confirming if the device is online and responsive.
- Traceroute: Traceroute helps to identify the path that data packets take across the network. It provides a hop-by-hop breakdown, showing where delays may occur in the communication route.
- IPConfig: On Windows systems,
ipconfigdisplays the current configuration of the network interface, including IP addresses, subnet masks, and default gateways. - Netstat: This command shows network connections, routing tables, and network statistics. It’s useful for checking the status of connections and open ports on a device.
- Show Commands: On Cisco devices,
showcommands, such asshow ip interface brieforshow running-config, display important device configurations and statuses. - Configure Terminal: In Cisco IOS,
configure terminalenters global configuration mode, allowing changes to be made to the device’s configuration.
By mastering these commands, network administrators can efficiently configure and troubleshoot network devices, ensuring optimal performance and resolving issues swiftly. The proper syntax and command structure are essential to avoid errors and achieve the desired network behavior.
Understanding IP Addressing
IP addressing is fundamental to the functioning of any network, as it allows devices to communicate with each other. By assigning unique identifiers to devices, networks ensure that data can be routed correctly to its destination. In this section, we will explore the key concepts of IP addressing, including the structure, classes, and subnetting techniques commonly used in networking.
IP Address Structure
An IP address consists of two main components: the network portion and the host portion. The network portion identifies the specific network, while the host portion specifies the individual device within that network. These components are separated by a subnet mask, which helps determine the boundaries of the network.
- IPv4: The most commonly used version of IP addresses, consisting of four octets (32 bits) written in decimal format, separated by periods (e.g., 192.168.1.1).
- IPv6: The newer version of IP addresses, using 128 bits and hexadecimal notation, designed to accommodate the growing number of devices on the internet.
Subnetting and Subnet Masks
Subnetting is a method used to divide a larger network into smaller subnets. This helps optimize network performance and security. A subnet mask is used in conjunction with an IP address to determine which portion of the address identifies the network and which part identifies the host.
- Subnet Mask: A 32-bit number that distinguishes the network and host portions of an IP address. For example, in the subnet mask 255.255.255.0, the first three octets (255) represent the network portion, and the last octet (0) identifies the host portion.
- Private vs. Public IP Addresses: Private IP addresses are used within local networks and cannot be routed over the internet, whereas public IP addresses are globally unique and are assigned by the Internet Assigned Numbers Authority (IANA).
Understanding the structure and allocation of IP addresses is critical for network configuration and troubleshooting. Properly assigned IP addresses and subnetting help ensure efficient data flow, minimize network congestion, and enhance overall security.
Analyzing Network Traffic in the Lab

Understanding and analyzing network traffic is crucial for diagnosing issues, optimizing performance, and ensuring the security of a network. By capturing and inspecting the data packets flowing through the network, administrators can gain valuable insights into the network’s behavior. This process involves monitoring various protocols, traffic patterns, and key metrics to identify potential problems and areas for improvement.
Traffic analysis typically involves using specialized tools that allow for real-time monitoring and packet inspection. These tools help identify unusual traffic, such as bottlenecks or unauthorized access, and provide the data needed to optimize network performance. Wireshark, tcpdump, and other network analyzers are commonly used for this purpose.
Key Metrics to Monitor
When analyzing network traffic, it is essential to track several key metrics to understand the overall health of the network. These metrics can reveal underlying issues and help troubleshoot performance problems:
- Bandwidth Utilization: Measures the amount of data transmitted across the network over a specific period. High utilization may indicate network congestion.
- Packet Loss: Indicates how many data packets were lost during transmission. Even small amounts of packet loss can cause significant performance degradation.
- Latency: The time delay between sending a packet and receiving a response. High latency can affect real-time applications like VoIP or video conferencing.
- Throughput: The actual rate of successful data transmission. It’s often lower than the maximum capacity due to network congestion or interference.
Common Traffic Patterns
By observing network traffic, administrators can identify various patterns that may indicate performance issues or potential security threats. Some of the most common patterns to watch for include:
- Unusual Traffic Spikes: Unexpected surges in traffic might be a sign of a DoS attack or an application malfunction.
- Protocol-Specific Traffic: Abnormal traffic from protocols like HTTP, FTP, or DNS could indicate misconfigurations or unauthorized use.
- Broadcast Storms: Excessive broadcast traffic can overwhelm the network, leading to slowdowns and instability.
Using Traffic Analysis for Troubleshooting
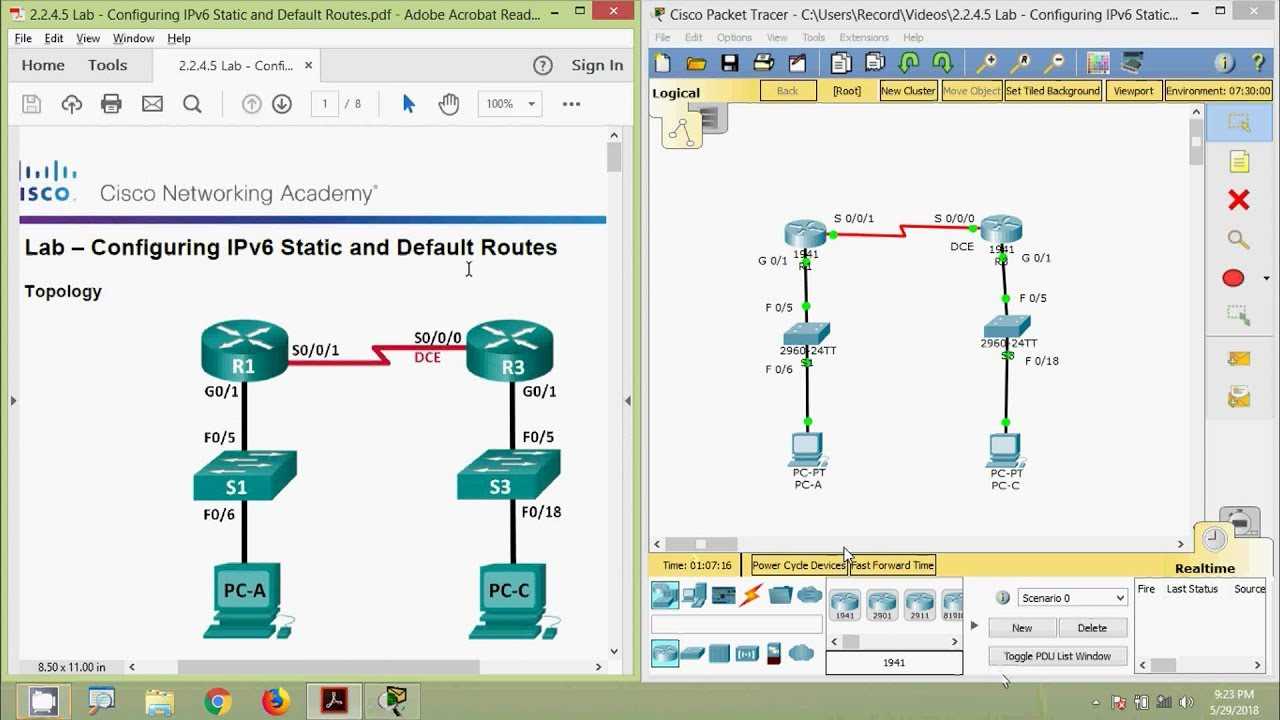
Analyzing network traffic is a vital step in troubleshooting network issues. By examining packet captures, administrators can pinpoint the source of problems, such as network congestion, hardware failures, or misconfigurations. This approach allows for a more targeted troubleshooting process, ensuring faster resolution and minimal disruption to the network.
| Metric | What It Measures | Tools for Analysis |
|---|---|---|
| Bandwidth Utilization | Rate of data transmission | Wireshark, NetFlow |
| Packet Loss | Percentage of lost packets | Ping, Traceroute |
| Latency | Time delay in data transmission | Ping, Wireshark |
| Throughput | Effective data rate | iperf, NetFlow |
Regular traffic analysis not only helps in identifying problems but also provides insights for network optimization. By understanding traffic flow and addressing issues as they arise, network administrators can maintain a stable, efficient, and secure network environment.
Effective Use of Simulation Tools
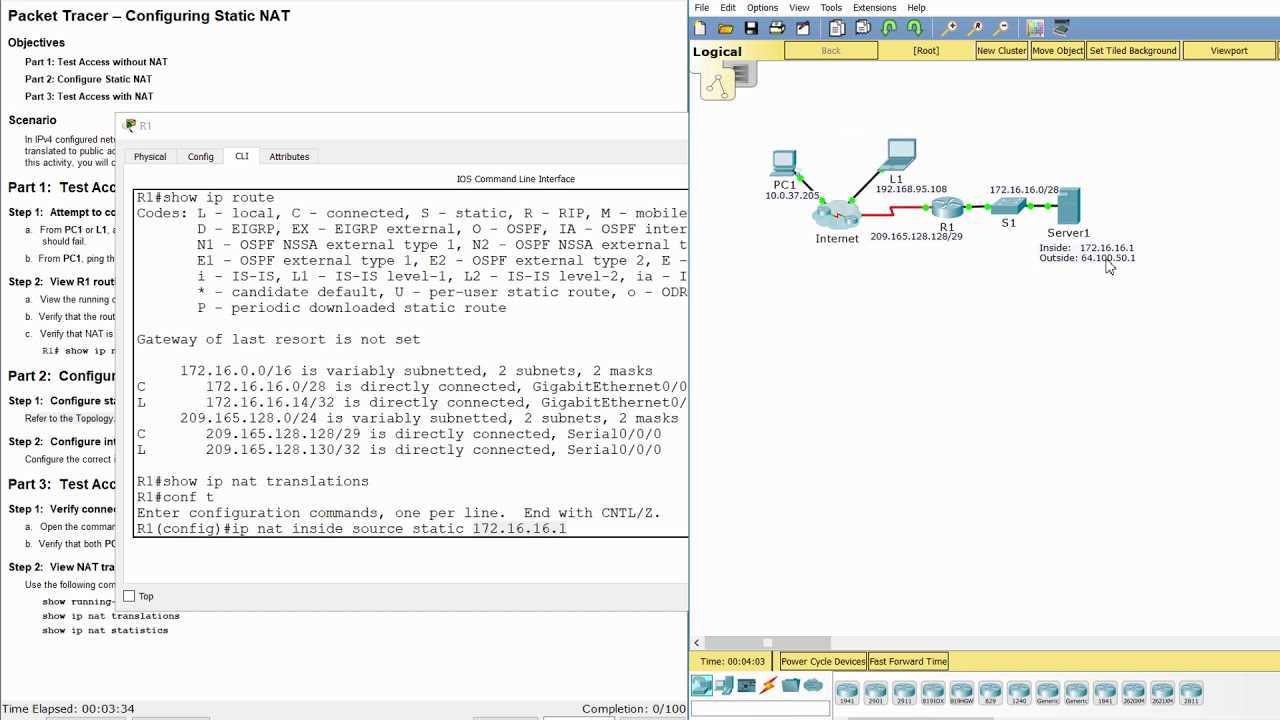
Simulation tools play a crucial role in network design and troubleshooting by enabling users to replicate real-world scenarios in a controlled environment. These tools help network administrators, engineers, and students to model, test, and experiment with different network configurations, protocols, and topologies without the need for physical hardware. The ability to simulate complex networks offers invaluable insights, allowing users to anticipate issues, optimize performance, and ensure network reliability before deployment in a live environment.
By utilizing simulation software, network professionals can visualize how data flows through various devices and components. These tools allow for the simulation of both simple and complex network setups, including routers, switches, firewalls, and end devices. Additionally, simulation tools enable troubleshooting of potential problems in a virtual environment, saving time and resources.
Benefits of Using Simulation Tools
- Cost-Effective: Simulation tools provide an affordable alternative to building and maintaining physical networks, making them an excellent choice for both educational and professional purposes.
- Risk-Free Experimentation: Users can safely test various configurations and protocols without the risk of damaging physical equipment or disrupting a live network.
- Immediate Feedback: Simulation tools provide real-time analysis, helping users quickly identify issues and understand the impact of configuration changes.
- Versatile Testing Environments: These tools allow for the creation of multiple test environments with varying network conditions, making them ideal for simulating different traffic scenarios or troubleshooting network failures.
Best Practices for Using Simulation Tools
- Start Simple: Begin with basic network topologies and configurations before moving on to more complex simulations. This approach helps build a strong understanding of how different devices interact within the network.
- Recreate Real-World Scenarios: When testing network setups or troubleshooting, try to replicate actual network conditions as closely as possible. This will help identify potential issues that might occur in a live environment.
- Analyze Results Thoroughly: Simulation tools often provide detailed performance metrics and logs. Take the time to thoroughly analyze these results to identify the root causes of issues or performance bottlenecks.
- Document Configurations: Save configurations and simulation results for future reference. This documentation can be helpful when troubleshooting similar issues in the future or when presenting findings to colleagues or stakeholders.
In summary, the effective use of simulation tools is essential for testing, designing, and optimizing network setups. By leveraging these tools, network professionals can gain a deeper understanding of network behavior, reduce the risk of errors, and improve network performance before implementation in real-world environments.
Common Mistakes in Network Configuration Tasks
When configuring network systems or performing related tasks, errors are inevitable, especially when working with complex setups or unfamiliar tools. These mistakes can lead to misconfigurations, network inefficiencies, or even complete failures. Recognizing common pitfalls can help users troubleshoot effectively, avoid rework, and improve overall performance. Below are some frequent errors encountered during network configuration exercises.
Frequent Errors in Configuration
- Incorrect IP Addressing: One of the most common mistakes is misassigning IP addresses or subnet masks, leading to communication failures between devices. It’s crucial to ensure that all devices in a network segment are within the same IP range and subnet.
- Improper VLAN Configuration: Misconfiguring VLANs can cause network traffic to be misdirected, leading to communication issues or traffic congestion. Always verify that the VLAN tags are correctly assigned to the right interfaces.
- Missing or Incorrect Routing Entries: Inadequate routing configurations can prevent data from reaching its intended destination. Missing static routes or incorrect dynamic routing settings are common problems that can disrupt network flow.
- Overlooking Default Gateway Settings: Failing to configure the correct default gateway on network devices can prevent them from communicating with external networks, such as the internet. This step is often overlooked during initial setup.
- Unmatched Cable Types: Using the wrong type of cable for connections, such as connecting a straight-through cable where a crossover cable is required, can lead to network failures. Always double-check cable types based on device requirements.
How to Avoid These Mistakes
- Double-Check IP Addresses and Subnets: Verify that all IP addresses, subnet masks, and default gateways are assigned correctly and consistently. Utilize subnet calculators to avoid errors.
- Ensure Correct VLAN Setup: Always verify VLAN configurations before deploying them. Use network simulation tools to visualize VLAN assignments and test communication between devices.
- Review Routing Tables: Carefully review all routing entries and ensure that the proper paths are set for internal and external communication. Pay attention to both static and dynamic routing protocols.
- Test Connectivity: Regularly test network connectivity with commands like ping and traceroute to ensure proper communication across devices. This helps identify issues early in the configuration process.
- Use the Right Cables: Make sure to match the correct cable type to the specific devices being connected, whether it’s a straight-through or crossover cable.
By understanding these common mistakes and adopting best practices to avoid them, network administrators can ensure smoother deployments, more reliable networks, and faster problem resolution when issues arise.
Best Practices for Networking Tasks
When working on networking configurations and tasks, it’s crucial to follow established practices that ensure efficiency, reliability, and security. Whether setting up a simple home network or a complex enterprise infrastructure, adopting best practices can prevent errors, reduce downtime, and enhance overall system performance. The following guidelines will help achieve optimal results in any networking task.
Planning and Documentation
Thorough Planning: Before starting any configuration, take the time to plan the network setup. This includes choosing IP address schemes, assigning devices to appropriate subnets, and selecting necessary hardware. Proper planning prevents costly mistakes and simplifies troubleshooting later on.
Documenting Configurations: Always document the configurations you implement. This includes IP addresses, VLAN assignments, routing protocols, and any specific changes made to devices. Having a comprehensive record makes it easier to revisit configurations in the future and ensures consistency across team members.
Network Security and Optimization
Implementing Security Measures: Security should be a priority in every networking task. Use strong passwords, enable firewalls, and apply encryption where possible. Regularly update device firmware and software to protect against vulnerabilities.
Optimizing Network Performance: Monitor traffic regularly and optimize settings like Quality of Service (QoS) to prioritize critical applications. Implementing redundancy measures such as link aggregation and load balancing ensures network reliability and enhances performance.
Testing and Verification
Testing Connectivity: Always test network connectivity after completing configurations. Tools like ping and traceroute help verify that devices are communicating properly and that routing is functioning as expected. Perform tests from multiple points in the network to ensure comprehensive coverage.
Verify Configurations: Before finalizing any changes, double-check configurations to ensure that all settings are correct. It’s better to spot mistakes during testing rather than during full deployment, as small errors can lead to large network issues.
By incorporating these best practices into your networking tasks, you can ensure smoother operation, reduce troubleshooting time, and build more secure and resilient network infrastructures.
How Practical Exercises Prepare for Real-World Scenarios
Hands-on practice is essential for building the skills needed to address real-world network challenges. By simulating actual networking tasks, learners are able to develop a deeper understanding of how different network configurations, protocols, and troubleshooting methods come into play in everyday scenarios. The exercises help build confidence, ensure a comprehensive grasp of concepts, and improve problem-solving abilities under realistic conditions.
Through practical exercises, participants are exposed to common network setup issues, configuration errors, and connectivity problems that occur in real environments. By troubleshooting these issues in a controlled setting, learners gain the experience necessary to resolve similar problems efficiently in the workplace. Additionally, these activities foster critical thinking and allow participants to experiment with different solutions in a risk-free manner.
Ultimately, these exercises simulate the complexity and unpredictability of real-world networks, ensuring that individuals are well-prepared to handle a variety of scenarios. Whether it’s configuring routers and switches, setting up secure connections, or diagnosing performance bottlenecks, hands-on practice sharpens the technical expertise needed for professional success in networking fields.
Final Tips for Successful Networking Exercises
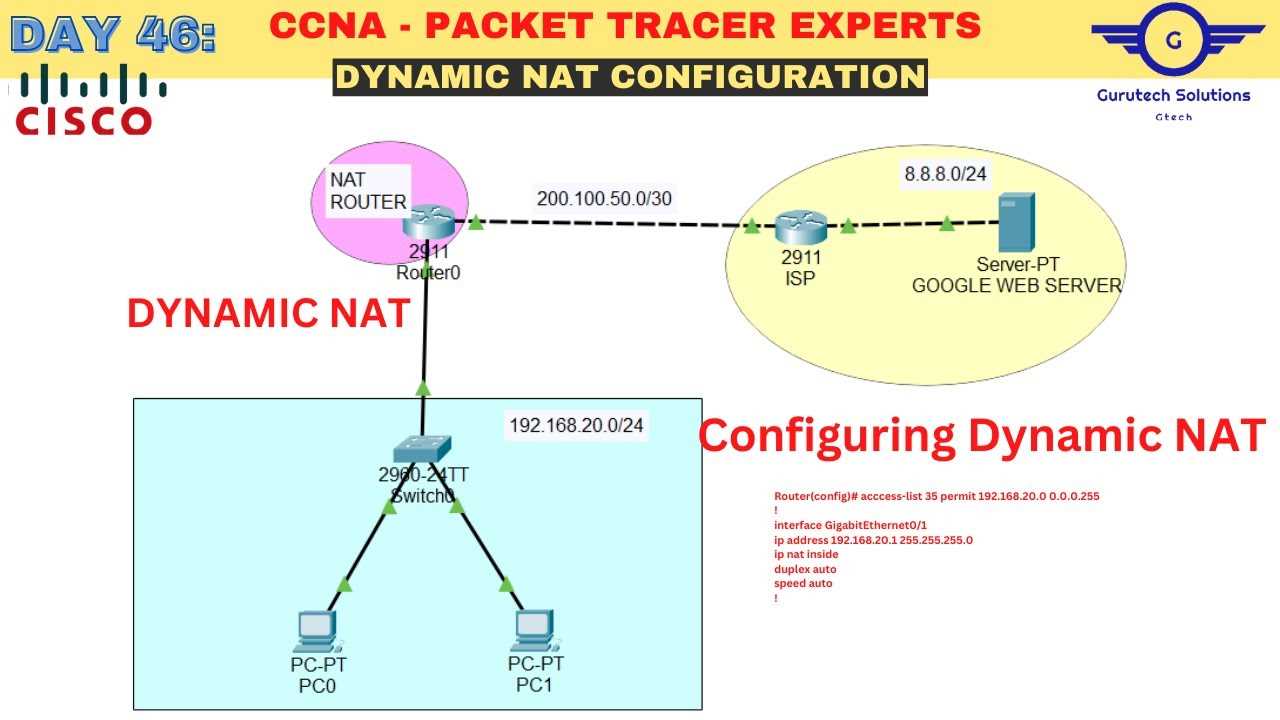
To excel in practical networking exercises, it’s important to approach each task with a clear plan and focused attention to detail. Whether you’re configuring devices, troubleshooting issues, or analyzing network traffic, mastering the basics and staying organized are key to success. Below are some final tips that can help you navigate through tasks more effectively and achieve better results.
- Stay organized: Keep a detailed record of each step you take. Documenting configurations and changes helps track progress and troubleshoot more effectively if something goes wrong.
- Double-check your work: Before moving on to the next step, ensure that all configurations are correct. Small mistakes can lead to larger issues later on, so it’s essential to verify your setup at each stage.
- Understand the concepts: Rather than just memorizing commands, focus on understanding the underlying principles behind them. This deeper understanding will help you apply solutions to a broader range of scenarios.
- Practice problem-solving: Don’t just follow instructions–actively troubleshoot and experiment with different solutions. The more you practice solving problems on your own, the more confident you’ll be when encountering new challenges.
- Utilize available resources: If you get stuck, use manuals, online forums, or seek help from peers or instructors. Understanding that it’s okay to ask for help when needed can accelerate learning and improve performance.
By following these guidelines and continuously practicing your skills, you’ll be better equipped to handle more advanced networking tasks and challenges in real-world environments. Consistency, patience, and attention to detail will ultimately lead to success in mastering networking techniques and concepts.