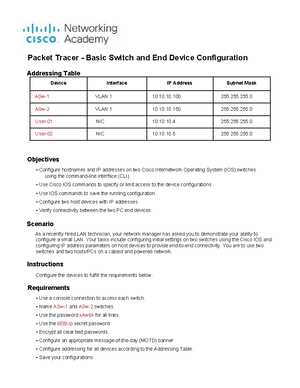
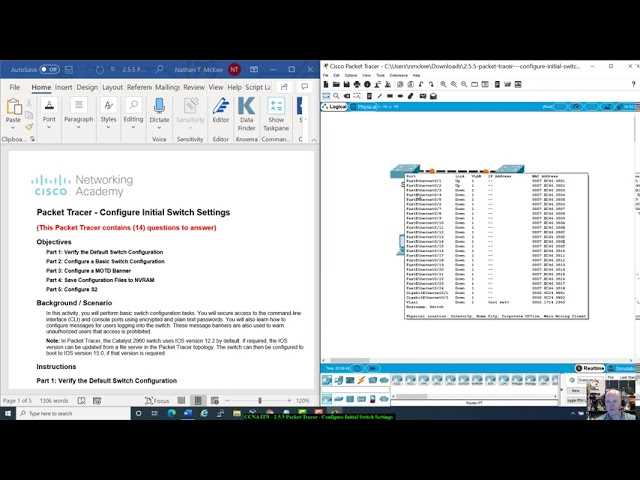
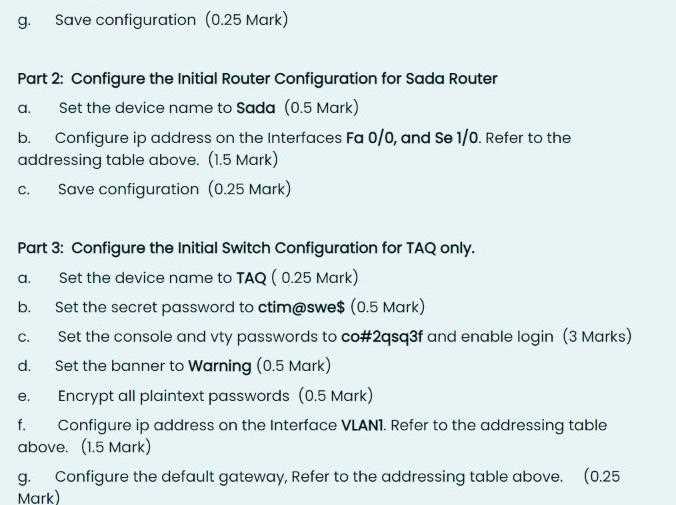
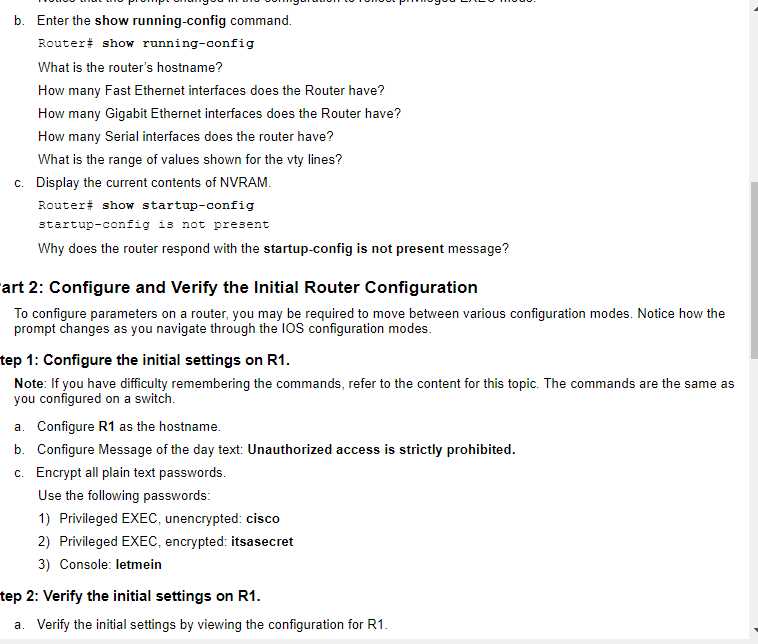
Configuring Initial Switch Settings in Packet Tracer Answers
When setting up a network environment, it’s essential to understand the fundamental steps required to make your devices operational. From establishing basic communication protocols to ensuring proper connections, a well-configured network infrastructure is crucial for smooth operation. This guide explores the core principles of setting up network equipment and optimizing connectivity in a virtual network environment.
By mastering the basics of device management, users can avoid common pitfalls that may hinder performance. Properly assigning IP addresses, configuring user access, and managing traffic flow are some of the key components that contribute to an efficient and secure network. Through detailed instructions and troubleshooting tips, this guide will help you navigate the most critical aspects of preparing network devices for use.
Initial Network Device Setup
When setting up a network device for the first time, it’s essential to perform a few basic tasks to ensure it functions correctly within your network. These early steps involve making sure the device is properly accessible, assigning it a management address, and preparing it for communication with other devices. This process establishes the foundation for effective network management and troubleshooting.
Establishing Device Communication
The first thing to do is connect the device to your network and ensure it can communicate with other components. This involves setting up basic connectivity options, such as assigning a static IP address that will allow the device to be accessed remotely for future changes and monitoring. Without this crucial step, the device won’t be able to interact with the network as intended.
Basic User Access and Security
Once communication is established, securing the device is the next important task. This includes setting up access credentials to protect the device from unauthorized use. By implementing a simple password system, you can control who can access the device’s configuration. These security measures are essential to maintaining the integrity of your network.
Understanding Basic Device Configuration
When working with network equipment, understanding the fundamental setup process is crucial for ensuring that the device functions as intended. The process of preparing a device for use involves several key steps, each designed to enable proper communication, security, and management. Once the device is set up correctly, it will be ready to support the overall network infrastructure.
The core steps in preparing a network device typically include:
- Assigning a unique identifier for management purposes
- Setting up access control to prevent unauthorized changes
- Enabling communication between network components
- Testing and verifying that the device is functioning as expected
By carefully following these steps, you ensure that the device is properly integrated into the larger network ecosystem, supporting both data flow and security. This process can vary depending on the specific role the device will play in the network, but the principles remain the same across different configurations.
Step-by-Step Device Setup Guide

Setting up a network device involves a series of methodical steps that ensure it operates efficiently within the network. By following a structured approach, users can easily configure the device to meet their specific requirements. This guide will walk you through the essential stages of the setup process, from basic configuration to securing access.
Preparation and Initial Access
The first step in setting up a network device is to establish communication with it. This can be done by accessing the device’s console interface or management panel. Once connected, you can begin by assigning a unique management IP address to facilitate future remote access.
- Connect the device to your network using a console cable.
- Open the console or terminal interface on your PC.
- Log in to the device using default login credentials.
- Assign an IP address for remote management.
Security and Access Control
After establishing communication, the next task is securing the device to prevent unauthorized access. This includes setting up strong passwords and creating user accounts with specific privileges. By implementing these security measures, you ensure that only authorized personnel can make changes to the device.
- Set a password for console access.
- Create usernames and assign appropriate access levels.
- Configure additional security features such as SSH for encrypted remote access.
With these steps, the device will be ready to integrate into the network, offering secure and reliable performance.
How to Access Device Command-Line Interface
To properly manage and configure a network device, accessing its command-line interface (CLI) is essential. The CLI provides a text-based interface where you can enter commands to modify the device’s configuration and settings. This section will guide you through the process of connecting to the CLI of a network device and beginning your configuration tasks.
Connecting to the Device

Before you can interact with the CLI, you need to connect to the device. This can be done through a console cable, typically using a virtual terminal on your computer. The following steps will help you establish a connection:
- Place the device into the workspace and connect it using a console cable.
- Open your terminal or simulation software on the computer.
- Select the device in the workspace and click on the console icon to initiate a connection.
- A terminal window will appear where you can begin typing commands.
Entering the Command Mode
Once connected, the next step is entering the command mode. This mode allows you to access all configuration options for the device. If you see a prompt asking for a login, enter the default credentials or any previously configured username and password. After logging in, you will be in user exec mode and can enter privileged exec mode for advanced commands.
- After the terminal window opens, type the appropriate username and password (if required).
- Type “enable” to enter privileged exec mode for higher-level commands.
- Once in this mode, you can begin making changes to the device’s configuration.
With these steps completed, you are ready to manage the device via the command-line interface and perform necessary configurations or troubleshooting tasks.
Setting Up Management IP on Device
To ensure effective remote management and monitoring of a network device, assigning a static IP address is a crucial step. This address allows administrators to access the device from any location within the network, facilitating configuration changes, troubleshooting, and routine maintenance. By setting up a management IP, you enable a reliable communication path between the device and network management tools.
To set up the management address, follow these steps:
- Access the device’s command-line interface (CLI) using a console or terminal connection.
- Enter privileged exec mode by typing enable and pressing Enter.
- Enter global configuration mode by typing configure terminal.
- Select the interface you want to assign the IP to (typically the VLAN interface) by typing interface vlan 1.
- Assign an IP address and subnet mask using the command ip address [IP address] [subnet mask].
- Enable the interface with the command no shutdown to activate the IP address.
- Save the configuration by typing write memory or copy running-config startup-config.
Once the management IP is configured, the device will be accessible via the specified address, allowing administrators to connect remotely and make necessary adjustments as required.
Configuring VLANs for Network Segmentation
Network segmentation is a fundamental practice that helps improve performance, security, and management in large networks. By dividing a network into smaller, isolated segments, traffic can be better controlled, and security risks can be minimized. One of the most effective ways to achieve this segmentation is through the use of Virtual Local Area Networks (VLANs). Each VLAN acts as an independent network, allowing devices within the same VLAN to communicate with one another while being isolated from devices in other VLANs.
Creating and Assigning VLANs
To start segmenting a network using VLANs, the first step is to create the VLANs themselves. Once created, you can assign specific ports on the device to the VLANs, ensuring that each port belongs to a particular group. Here’s how you can create and assign VLANs:
- Access the device’s command-line interface (CLI).
- Enter global configuration mode by typing configure terminal.
- Create a VLAN by typing vlan [VLAN number] (e.g., vlan 10).
- Optionally, name the VLAN for easier identification using the command name VLAN [name].
- Assign ports to the VLAN using the interface range command, such as interface range fa0/1 – 24, followed by switchport access vlan [VLAN number].
Verifying VLAN Configuration
Once the VLANs are configured and assigned, it’s important to verify that everything is functioning as expected. This can be done using simple commands that show the VLAN details and ensure all configurations are correctly applied.
- Check the VLANs created by typing show vlan brief to display all VLANs and their assigned ports.
- To confirm that the ports are assigned correctly, use the show interfaces switchport command to see port-specific VLAN assignments.
By configuring VLANs effectively, you can enhance both the security and performance of your network, ensuring that each segment operates independently while maintaining seamless communication when needed.
Assigning Ports to VLANs
To segment a network efficiently, it’s crucial to assign specific ports to the correct VLANs. This ensures that devices connected to these ports are grouped together logically, even if they are physically located in different parts of the network. By assigning ports to the right VLANs, you can control traffic flow, improve security, and reduce congestion between devices on separate networks. This section explains how to assign ports to VLANs effectively.
Steps to Assign Ports to VLANs
The process of assigning ports to VLANs involves configuring each port on the device to be part of a specific VLAN. Follow these steps to complete the assignment:
- Access the device’s command-line interface (CLI).
- Enter global configuration mode by typing configure terminal.
- Select the interface or range of interfaces you wish to assign to a VLAN. For example, interface range fa0/1 – 24 selects ports 1 through 24.
- Assign the interface to a VLAN using the command switchport access vlan [VLAN number] (e.g., switchport access vlan 10).
- Exit the interface configuration by typing exit.
Verifying the Configuration
Once the ports have been assigned to their respective VLANs, it’s important to verify the configuration to ensure everything is set up correctly. Use the following commands to confirm the assignments:
- show vlan brief – Displays a list of all VLANs and their associated ports.
- show interfaces switchport – Shows detailed information about the VLAN assignment for each interface.
By correctly assigning ports to VLANs, you ensure proper network segmentation and optimized traffic management across the network.
Enabling DHCP on Device Ports
Dynamic Host Configuration Protocol (DHCP) is an essential service that allows devices to automatically obtain IP addresses and network configuration details from a server. Enabling DHCP on device ports helps simplify network management by eliminating the need for manual IP address configuration on each connected device. When DHCP is enabled, each device connected to a specific port will be assigned an IP address dynamically, ensuring a more efficient and error-free network setup.
Steps to Enable DHCP
Follow these steps to enable DHCP on device ports:
- Access the command-line interface (CLI) of the device.
- Enter global configuration mode by typing configure terminal.
- Select the port or range of ports you wish to enable DHCP for. For example, to select port 1: interface fa0/1.
- Enable DHCP by typing ip address dhcp.
- Exit the interface configuration mode by typing exit.
- Save the configuration with write memory or copy running-config startup-config.
Verifying DHCP Configuration
After enabling DHCP, it’s important to verify the configuration to ensure that devices connected to the ports will automatically receive IP addresses. Use the following command to check the status:
| Command | Description |
|---|---|
| show ip interface brief | Displays a summary of the interface status and whether an IP address has been assigned by DHCP. |
| show running-config | Displays the current configuration, including DHCP settings for each interface. |
Once DHCP is enabled and verified, devices connected to the specified ports will automatically receive an IP address, ensuring they can communicate seamlessly within the network.
Securing Device Access with Passwords
Securing access to network devices is a crucial part of maintaining a secure and reliable infrastructure. One of the most effective ways to protect devices from unauthorized access is by setting up strong passwords. These passwords ensure that only authorized users can modify configurations, perform maintenance, or access sensitive information. In this section, we’ll look at how to secure device access by setting up passwords for various modes of operation.
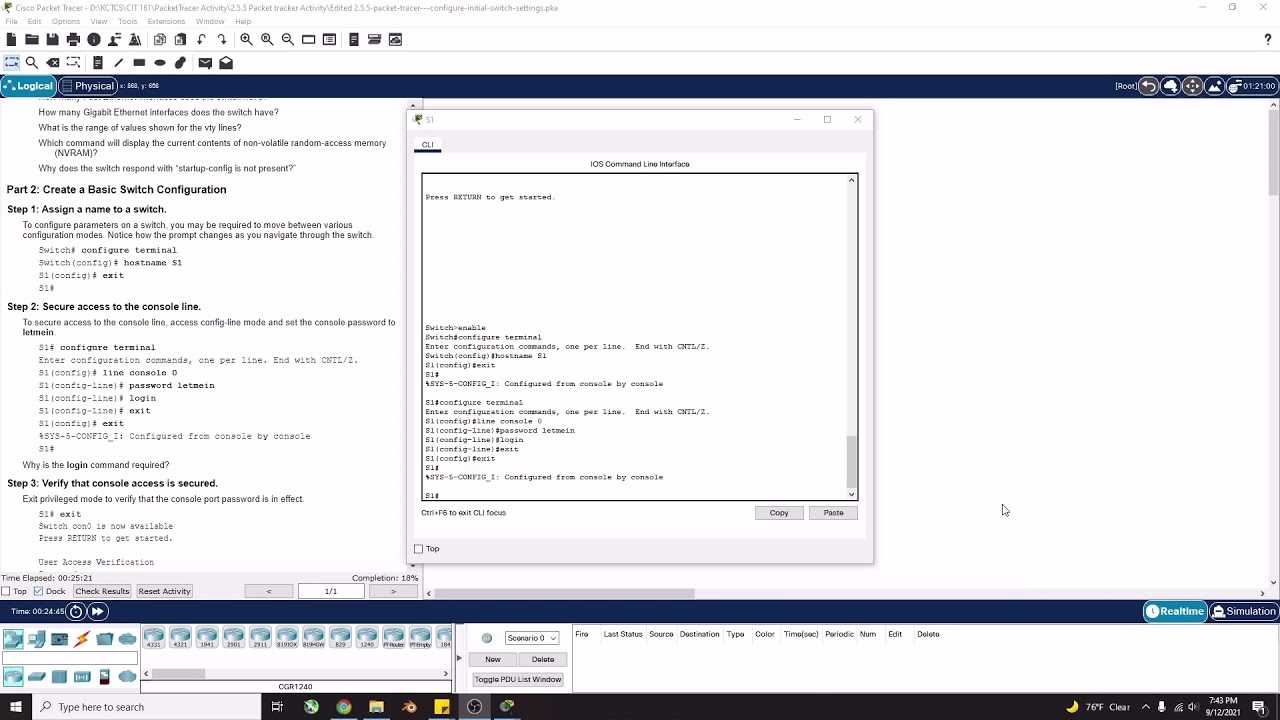
Configuring Console Password
One of the first steps in securing access is configuring a password for the console port. This ensures that anyone trying to access the device locally will be required to authenticate first. Here’s how to set it up:
- Access the device’s command-line interface (CLI).
- Enter global configuration mode by typing configure terminal.
- Select the console line by typing line con 0.
- Set the password by typing password [your password].
- Enable login for console access with login.
- Exit the line configuration mode with exit.
Enabling Enable Password for Privileged Mode
Another important security step is to set a password for privileged EXEC mode, often referred to as “enable” mode. This mode allows full access to the device configuration and should be protected to prevent unauthorized changes. To configure this password:
- Enter global configuration mode by typing configure terminal.
- Set the enable password with the command enable password [your password].
- If you want to use an encrypted password for added security, use the command enable secret [your encrypted password] instead.
- Exit the global configuration mode with exit.
By securing device access with passwords, you help safeguard your network infrastructure from unauthorized users and protect the integrity of your configurations.
Creating User Accounts for Device Access
Managing user access to network devices is an essential part of maintaining control over who can modify configurations and access sensitive data. By creating user accounts, you can ensure that only authorized individuals have access to the device. This allows for better tracking of changes and reduces the risk of unauthorized access. In this section, we will explore how to create user accounts and assign appropriate privileges to secure your network infrastructure.
Steps to Create User Accounts
To create a new user account, follow these steps:
- Access the device’s command-line interface (CLI).
- Enter global configuration mode by typing configure terminal.
- Use the command username [username] password [password] to create a new user account. For example, username admin password admin123.
- If you wish to assign the user a higher level of access, use username [username] privilege [level] (where the level ranges from 0 to 15, with 15 being the highest level of access).
- To enable the user to access privileged EXEC mode, you can add the secret keyword for more secure authentication. For example, username admin secret admin123.
- Exit global configuration mode by typing exit.
Assigning User Roles and Privileges
Once a user account is created, it is important to assign the appropriate level of access to that account. By doing so, you can control what actions a user can perform on the device:
- Privilege level 0: Basic access, usually only to view the system status.
- Privilege level 1: Standard access with limited capabilities, such as viewing configuration but not editing it.
- Privilege level 15: Full administrative access, including configuration changes, system updates, and other critical actions.
By assigning proper user accounts and defining access levels, you can ensure that only authorized individuals have the appropriate privileges to manage and configure network devices, improving both security and accountability.
Understanding Ports and Types on Network Devices
Network devices, such as routers and hubs, have various types of ports that serve different functions. Each port type allows specific devices to connect to the network, and understanding these ports is crucial for proper configuration and network segmentation. In this section, we’ll explore the different types of ports typically found on network devices and their roles in connecting and managing network traffic.
Common Port Types
Network devices support different types of ports, each serving a distinct purpose. Below is a summary of the most common port types:
| Port Type | Description |
|---|---|
| Ethernet | Used for wired network connections, typically for LAN connectivity between devices. |
| Fast Ethernet | Supports speeds up to 100 Mbps for high-speed network connections. |
| Gigabit Ethernet | Offers higher speeds (up to 1 Gbps) for high-performance network requirements. |
| Console | Used for device management and troubleshooting by providing a direct CLI connection. |
| Trunk | Carries multiple VLANs between devices, allowing traffic from different segments to pass through a single connection. |
| Auxiliary | Provides an alternate method of device management, often used for remote access. |
Role of Ports in Network Configuration
Each port plays a vital role in how data flows within a network. For instance, Ethernet and Gigabit Ethernet ports are often used to connect workstations, servers, or other devices, while trunk ports facilitate communication between switches, allowing multiple virtual networks to be transmitted over a single link. Understanding these different port types and their functions helps ensure that the network is configured properly for optimal performance and security.
Testing Connectivity Between Network Devices
Ensuring that network devices are properly connected and can communicate with each other is a crucial step in setting up any network. Connectivity tests help verify whether devices can reach one another, whether they are configured correctly, and if there are any underlying issues preventing communication. In this section, we will cover how to perform basic connectivity tests to ensure that your devices are functioning as expected.
Methods for Testing Connectivity
There are several methods used to check if network devices are connected correctly and communicating properly:
- Ping: This is the most commonly used tool to test the basic connectivity between devices. The ping command sends small data packets to a destination device and waits for a response. If the destination device is reachable, a reply will be returned, indicating successful communication.
- Traceroute: This tool tracks the path that data packets take to reach their destination. It provides valuable information about the intermediate devices that data travels through, which can help identify where connectivity issues may be occurring.
- Telnet/SSH: For testing access to a device’s command-line interface (CLI), Telnet or SSH can be used. These tools help confirm that the device is reachable and that you can interact with it remotely.
Verifying Physical and Logical Connections
In addition to using software tools, it’s also important to ensure that the physical connections between devices are correct. Check cables, ports, and LEDs on devices to ensure proper link status. If devices are connected through a network hub, switch, or router, verify that each device has been assigned the correct IP addresses and is in the right subnet.
By testing connectivity, you can quickly identify any issues with the network’s configuration, hardware, or cabling, ensuring that all devices can communicate properly within the infrastructure.
Common Network Device Configuration Mistakes
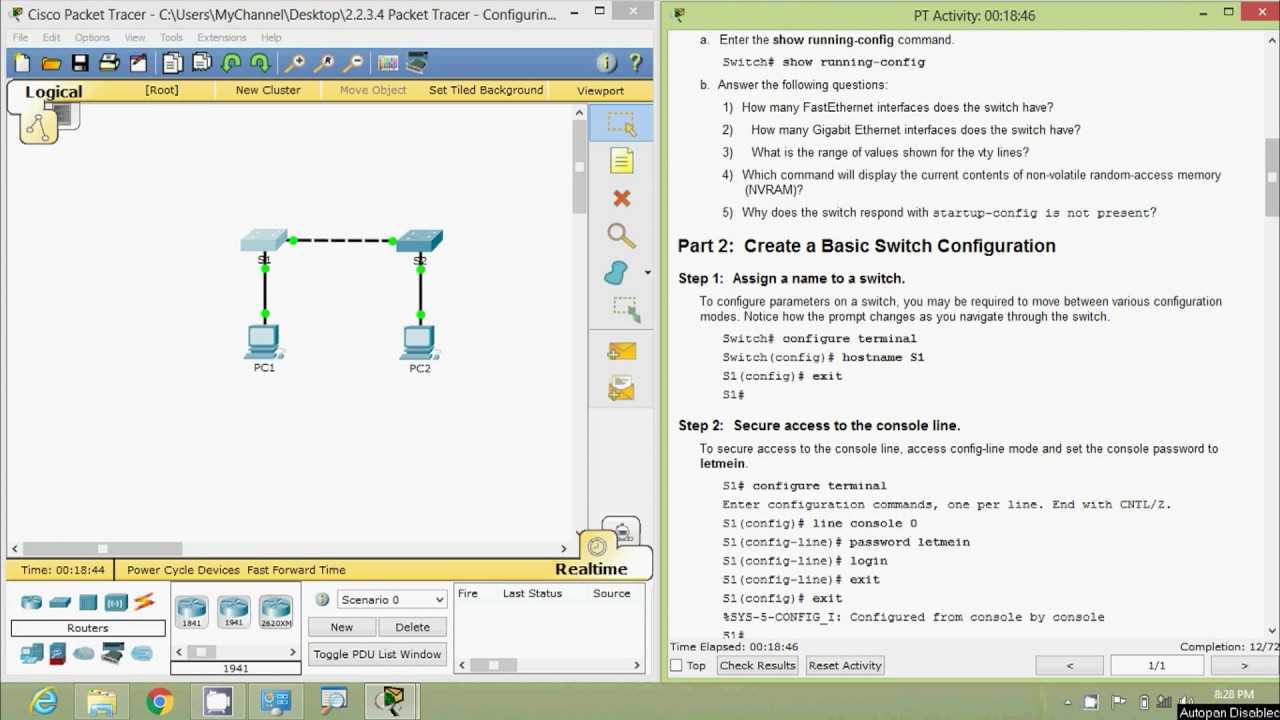
When setting up network devices, even small errors can lead to significant issues in performance or connectivity. Understanding and avoiding common mistakes during the setup process can save time and prevent network disruptions. In this section, we will explore some of the most frequent misconfigurations and offer tips for avoiding them.
Incorrect IP Addressing
One of the most common mistakes made during network configuration is assigning incorrect IP addresses or using an incompatible subnet. Devices in the same network segment must have IP addresses within the same range. Failing to correctly configure this can lead to devices being unable to communicate. It’s crucial to ensure that IP addresses are unique, and subnets are correctly assigned to prevent address conflicts and routing issues.
Failure to Assign VLANs
Virtual Local Area Networks (VLANs) are used to segment network traffic and improve security. However, not assigning VLANs properly can cause devices to be isolated or unable to access the network. Ensure that all ports on the device are correctly assigned to the appropriate VLAN to allow seamless communication across different network segments. Failing to assign VLANs or misconfiguring them can lead to unexpected communication breakdowns between devices.
These are just a few examples of common mistakes. Addressing these early during the configuration process can help maintain a smooth-running network with minimal issues. By double-checking each step and using proper configurations, network administrators can avoid these pitfalls and ensure that their devices operate efficiently.
Using Static IP vs Dynamic IP Settings
When setting up devices within a network, one of the fundamental choices is whether to assign IP addresses manually or allow them to be dynamically assigned. Both methods have their advantages and disadvantages, depending on the specific needs of the network and its devices. Understanding the differences between these two approaches can help determine the most appropriate configuration for your setup.
Static IP Addresses
Static IP addresses are manually assigned and remain the same over time. This method is ideal for devices that require a consistent, unchanging address, such as servers, network printers, or other critical infrastructure. By using a static IP, network administrators can ensure that devices are always reachable at the same address, which is essential for certain applications and services.
Dynamic IP Addresses
Dynamic IP addressing, on the other hand, involves assigning IP addresses automatically through a system like DHCP (Dynamic Host Configuration Protocol). This method is more flexible and efficient for devices that do not require a permanent address. It allows for better use of available IP addresses, especially in large networks, where devices are constantly joining and leaving the network.
| Feature | Static IP | Dynamic IP |
|---|---|---|
| Address Assignment | Manual | Automatic (via DHCP) |
| Consistency | Fixed | Variable |
| Configuration Complexity | Higher | Lower |
| Best For | Servers, Printers, Critical Devices | Client Devices, Temporary Devices |
Choosing between static and dynamic addressing depends on the specific requirements of the network. For most consumer devices and temporary connections, dynamic IPs are often sufficient. However, for infrastructure that requires consistent communication, static IPs are typically the best choice.
Configuring Link Aggregation on Switches
Link aggregation is a technique used to combine multiple network connections into a single logical connection, improving bandwidth and providing redundancy. This approach is commonly used in environments where high availability and high throughput are essential, such as in enterprise networks or data centers. By grouping multiple links together, network devices can distribute the traffic load evenly, minimizing the risk of bottlenecks.
The primary goal of link aggregation is to increase the total capacity between two network devices. Instead of relying on a single connection, multiple physical interfaces are bundled into one logical unit, allowing for faster data transmission. Additionally, if one link fails, the remaining links in the group can continue to handle the traffic, ensuring minimal disruption to the network.
There are two common methods of implementing link aggregation:
- Static Link Aggregation – Manual configuration without negotiation between devices. This method requires both ends of the connection to be configured identically.
- Dynamic Link Aggregation – Uses protocols such as LACP (Link Aggregation Control Protocol) to automatically negotiate and manage the aggregation of links between devices.
When configuring link aggregation, it is crucial to ensure that the devices on both ends support the feature and are properly configured to use either static or dynamic methods. For dynamic aggregation, LACP is widely supported and helps simplify the process by automating the negotiation of the aggregated links.
Here is a basic outline of the steps to configure link aggregation:
- Ensure that both network devices support link aggregation.
- Choose between static or dynamic aggregation based on your requirements.
- If using LACP, enable the protocol on both ends.
- Bundle the physical links into a single logical connection using the appropriate commands or interface settings.
- Test the configuration by sending traffic and ensuring that the aggregate link is utilized efficiently.
By utilizing link aggregation, you can significantly enhance network performance, ensure better fault tolerance, and achieve a more resilient network architecture.
Setting Up Trunking Between Switches
Trunking is a method used to allow multiple virtual networks to pass through a single physical connection between two network devices. This approach is commonly used when there is a need to carry traffic from multiple virtual local area networks (VLANs) across a network. By setting up trunking, network administrators can efficiently use available physical connections to transport traffic for multiple VLANs without needing separate links for each one.
The process of establishing trunking involves configuring specific ports on the devices to handle traffic for more than one VLAN. These ports will be able to distinguish between the different VLANs by tagging the traffic with unique identifiers, known as VLAN tags. This allows the devices at both ends of the trunk to properly route the data to the correct virtual networks, ensuring that the traffic for each VLAN remains separate.
There are two primary trunking protocols that can be used:
- IEEE 802.1Q – This is the most commonly used standard for trunking. It inserts a tag into the Ethernet frame header to identify the VLAN to which the data belongs.
- ISL (Inter-Switch Link) – A Cisco proprietary protocol, though it is less commonly used today. It encapsulates the Ethernet frame to include the VLAN information.
To set up trunking between devices, the following steps should be followed:
- Identify the ports on both devices that will be used for the trunk connection.
- Configure the trunking protocol (usually IEEE 802.1Q) on both ends of the connection.
- Enable trunking on the appropriate ports, ensuring that they are set to allow traffic from all relevant VLANs.
- Verify that the trunk is functioning properly by checking for correct VLAN tagging and ensuring that traffic for different VLANs is properly separated and routed.
Trunking simplifies network management by reducing the number of physical connections required while still allowing efficient traffic management for multiple VLANs. With proper configuration, it can help create a more scalable and flexible network design.
Saving and Verifying Switch Configuration
After completing the setup of network devices, it’s essential to save the configuration to ensure that all changes made to the device are retained even after a reboot. Without saving, any modifications made will be lost when the device restarts, potentially leading to interruptions in network service. Verifying the configuration is also crucial to ensure that the device is operating as expected and all changes have been implemented correctly.
Saving the Configuration
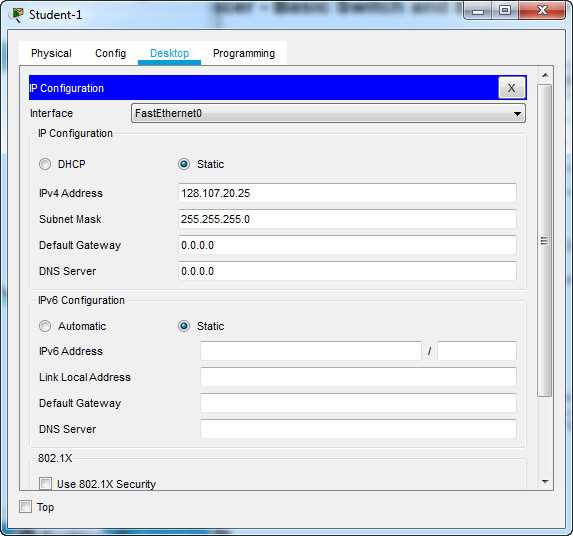
Once the desired changes have been made, the configuration must be saved to both the running configuration and the startup configuration. The running configuration is temporary and exists in the device’s memory, whereas the startup configuration is stored in non-volatile memory and is used when the device restarts. To save the configuration, the following commands are commonly used:
- Copy running-config startup-config: This command saves the current running configuration to the startup configuration file, ensuring that changes are retained after a reboot.
- Write memory: An alternative command used to save the current configuration to memory.
It’s important to remember to save the configuration after making changes to avoid losing important settings or configurations due to power loss or device restart.
Verifying the Configuration
After saving the configuration, it’s necessary to verify that all the settings are applied correctly and the device is functioning as expected. Verification involves checking the current state of the device and confirming that the intended changes are in effect. Several commands can help in this process:
- Show running-config: Displays the active configuration currently running on the device, allowing administrators to review all the applied settings.
- Show startup-config: Displays the configuration that will be loaded upon reboot. This helps verify that the saved configuration matches the active configuration.
- Show interfaces: Provides information about the interfaces and their status, useful for verifying connectivity settings.
- Ping: Used to test connectivity between devices, ensuring that the network setup is functioning as expected.
By saving and verifying configurations, network administrators can ensure the stability and reliability of the network infrastructure, preventing unexpected issues and minimizing downtime.
Troubleshooting Common Switch Issues
Network devices play a critical role in ensuring smooth communication between systems. However, misconfigurations, hardware failures, or network disruptions can lead to connectivity issues. Troubleshooting these problems involves systematically checking configurations, verifying connections, and identifying the root cause of any disruptions. Understanding common issues that arise with networking devices is essential for efficiently diagnosing and resolving problems.
Common Problems and Their Causes
Several issues can affect network devices, from connectivity disruptions to configuration errors. Below are some frequent problems and potential causes:
- Loss of Connectivity: This can be due to incorrect cable connections, interface status issues (e.g., interfaces being administratively down), or improper IP address assignments.
- Slow Network Performance: Often caused by bandwidth congestion, incorrect quality of service (QoS) settings, or issues with network interfaces (e.g., duplex mismatches).
- Looping Problems: Network loops can occur when devices are improperly connected, leading to broadcast storms and network congestion. Misconfigured spanning tree protocol (STP) settings are usually the cause.
- Unresponsive Device: This can be caused by hardware failures, excessive CPU utilization, or memory exhaustion. Checking the device’s resource utilization can help identify the issue.
- VLAN Misconfigurations: When VLANs are not configured properly, devices may be unable to communicate within the expected segments. This could be due to incorrect VLAN assignments, trunking misconfigurations, or a missing VLAN on certain ports.
Steps for Troubleshooting
To resolve issues, it is crucial to follow a structured approach to identify and fix the problem. Here are some essential steps:
- Check Physical Connections: Ensure that cables are properly connected and undamaged. Verify the port LEDs to check for any hardware-related issues.
- Verify Interface Status: Use commands like show interfaces to confirm that the interfaces are up and running. Check for administratively down interfaces and enable them if necessary.
- Check IP Configuration: Use show ip interface brief to verify that the IP address configuration is correct. Misconfigured IP addresses can cause communication failures.
- Inspect VLAN Configurations: Review VLAN assignments and ensure that each device is part of the correct VLAN. Use commands like show vlan brief to check VLAN membership.
- Test Connectivity: Use the ping command to test basic connectivity between devices. If the ping fails, it could point to network misconfigurations or physical connectivity issues.
By following these troubleshooting steps and understanding the common causes of issues, network administrators can quickly identify and resolve problems, ensuring that network devices operate smoothly and reliably.