Windows Exam Questions and Answers for Exam Success

Preparing for a certification that focuses on computer systems and their management requires a solid understanding of various core concepts. Whether you’re aiming to demonstrate proficiency in system administration, network management, or security practices, it’s essential to familiarize yourself with the topics commonly tested. Success depends not only on theoretical knowledge but also on the ability to apply that knowledge in real-world scenarios.
Efficient preparation involves knowing the specific areas most likely to appear during the assessment. From system configuration to troubleshooting, each topic brings unique challenges. It’s important to grasp not just the definitions but also the practical implications of the concepts involved. This can make all the difference when faced with a practical or theoretical question on the test.
Hands-on experience with the relevant tools and environments is crucial for mastering the required skills. Understanding the relationships between various system components, knowing how to address issues, and being familiar with operational practices will set you up for success. Being well-prepared means you’re not just memorizing facts, but also building a deeper understanding that you can apply during the assessment.
Windows Exam Questions and Answers
To effectively prepare for certification in system administration and management, it is important to focus on the types of tasks and concepts that are commonly tested. The knowledge required spans across various technical areas, with an emphasis on practical application and problem-solving. A well-rounded understanding will help in answering both theoretical and practical inquiries that are part of the assessment process.
Key Topics for Mastery
The content typically covers a range of areas, including system configuration, troubleshooting methods, security practices, and network management. Familiarizing yourself with the specific areas of focus will help you not only understand the material but also improve your ability to apply that knowledge in realistic situations.
Tips for Handling Practical Challenges

During the assessment, you may encounter tasks that require applying technical knowledge to solve real-world problems. For example, understanding how to configure different system components, address connectivity issues, or implement security measures are tasks that can be tested in various formats. Practicing with hands-on exercises is an excellent way to prepare for these challenges.
| Topic | Importance | Typical Test Format |
|---|---|---|
| System Configuration | High | Multiple choice and practical tasks |
| Troubleshooting | High | Scenario-based questions |
| Network Management | Medium | Practical tests |
| Security Practices | High | Multiple choice and real-world scenarios |
Mastering the key concepts in these areas will provide the foundation needed for achieving a high score. By preparing thoroughly and practicing with mock scenarios, you’ll be better equipped to handle the various challenges that may arise during the certification process.
Key Topics to Study for Certification
To ensure thorough preparation for the certification assessment, focusing on critical subject areas is essential. These topics not only cover theoretical knowledge but also require practical understanding. A comprehensive grasp of the core elements will increase your chances of success during the test, allowing you to tackle both practical challenges and conceptual inquiries with confidence.
Core Areas of Focus
The main concepts that are frequently covered include system setup, user management, security configurations, and troubleshooting techniques. Gaining expertise in these areas will equip you with the tools necessary to handle real-world scenarios, which are often a part of the testing process.
- System Setup and Configuration – Understanding how to configure hardware, install software, and manage system resources effectively.
- Security Practices – Knowledge of encryption, firewalls, permissions, and user authentication methods.
- Troubleshooting – Ability to diagnose and fix issues related to both hardware and software failures.
- Networking Fundamentals – Familiarity with IP addressing, DNS, DHCP, and network configuration.
- System Maintenance – Techniques for managing updates, patches, backups, and performance monitoring.
How to Prepare Effectively
Aside from understanding the theoretical aspects of the topics above, hands-on experience is invaluable. Setting up labs, running simulations, and practicing troubleshooting scenarios will deepen your understanding. Many online resources provide practice exercises that replicate the types of challenges you might face during the assessment.
- Review key concepts regularly to reinforce your memory.
- Engage in practical exercises to improve problem-solving skills.
- Use mock assessments to test your readiness.
- Study case studies and real-world examples to understand application.
By focusing on these primary areas and employing effective study techniques, you’ll be better equipped to succeed in the certification process.
Understanding Operating System Basics
To excel in any certification focused on computer management, a strong foundation in the core aspects of system functionality is crucial. This knowledge encompasses how an operating system manages hardware resources, handles user commands, and supports software execution. A deep understanding of these fundamentals is key to troubleshooting, configuring, and maintaining the environment effectively.
Key Components of a System
Every operating environment relies on a set of core components to function efficiently. These include the kernel, user interface, and system services, which work together to ensure smooth operation. Familiarity with each of these elements will allow you to navigate through administrative tasks with ease.
- Kernel: The central component responsible for managing system resources and communication between hardware and software.
- File System: A method for organizing, storing, and accessing data on storage devices.
- User Interface: The interface through which users interact with the system, including graphical and command-line options.
- System Services: Essential background processes that manage various tasks, such as printing or networking.
How the System Handles Tasks
The efficient execution of programs and user commands relies on the coordination between hardware and software. The system’s job is to allocate resources, schedule tasks, and ensure processes don’t interfere with one another. This coordination ensures that everything runs as intended, from simple file access to complex software operations.
Understanding these processes enhances your ability to troubleshoot performance issues and configure the environment to meet specific requirements. By mastering these basics, you’ll be well-prepared for more advanced tasks and challenges that will come up in real-world situations.
Common Certification Assessment Formats
When preparing for a certification focused on system management, it’s essential to understand the different ways the material is presented. The format of the challenges you’ll face can vary significantly, requiring not only knowledge but also the ability to apply that knowledge under different circumstances. These formats typically test both theoretical understanding and practical problem-solving skills.
One of the most common formats is multiple-choice, where you’re asked to select the best possible answer from a list of options. This format is used to assess a wide range of topics quickly and effectively. Another format includes scenario-based questions, which test your ability to apply theoretical knowledge in real-world situations. These scenarios often simulate troubleshooting or system configuration tasks that a professional might encounter on the job.
There are also practical tasks, which require you to perform specific actions within a simulated environment or through virtual labs. These questions are designed to assess how well you can apply your skills to solve problems and complete tasks efficiently. It’s crucial to gain hands-on experience with these formats during your preparation.
Preparing for the Troubleshooting Section
Effective preparation for troubleshooting tasks involves not only understanding theoretical concepts but also developing the ability to identify and resolve issues in real-world scenarios. This section of the assessment is designed to test your problem-solving skills, requiring you to diagnose system failures, performance issues, or configuration errors quickly and accurately. Success depends on knowing how to approach problems methodically and efficiently.
Begin by familiarizing yourself with common issues that might arise, such as connectivity problems, system crashes, or application malfunctions. It’s essential to learn diagnostic techniques that will help you narrow down the root cause of a problem. These might involve using built-in tools, reviewing error logs, or conducting tests to rule out potential causes.
Hands-on practice is crucial for honing your troubleshooting skills. Simulating real-world issues and working through them step by step will help you gain confidence. The more familiar you become with various problems and their solutions, the better prepared you’ll be for similar challenges during the assessment.
Mastering Security and Privacy Settings
Ensuring a system is secure and protecting personal data is a vital skill in today’s technology-driven environment. This section focuses on understanding the key settings that safeguard both system integrity and user privacy. Whether configuring firewalls, managing user accounts, or setting up encryption, these controls are essential for maintaining a secure operating environment.
A strong security foundation begins with properly configuring user permissions, ensuring that only authorized individuals have access to sensitive information. It’s equally important to understand the role of firewalls, antivirus software, and other protective measures in defending against potential threats. Additionally, privacy settings such as data encryption, tracking prevention, and managing app permissions help protect personal information from unauthorized access.
Mastering these settings requires knowledge of how to configure, monitor, and update them regularly. Being proactive in identifying vulnerabilities and mitigating risks will help maintain a secure environment. Furthermore, understanding the balance between convenience and privacy is key to ensuring optimal protection without compromising system usability.
Essential System Configuration Knowledge
Mastering system configuration is a fundamental skill for anyone looking to excel in system administration. This area involves setting up and managing hardware, software, and network components to ensure optimal performance and stability. A deep understanding of these tasks will allow you to fine-tune a system, configure user settings, and address any issues that may arise.
Key Areas to Focus On
The following components are critical to system configuration and should be thoroughly understood:
- Hardware Configuration: Knowing how to configure devices like storage, printers, and input peripherals.
- Operating System Setup: Installing, updating, and maintaining the core environment for running software and applications.
- Network Configuration: Setting up network interfaces, IP addresses, DNS servers, and other essential components to ensure connectivity.
- User Account Management: Creating and managing user profiles, permissions, and groups to control access and security.
- System Performance Tuning: Optimizing system resources, managing background processes, and configuring memory allocation.
Practical Application of System Configuration
Understanding theoretical concepts is important, but applying them in real-world scenarios is where true expertise is developed. Working with actual systems–whether setting up servers, configuring storage devices, or troubleshooting issues–helps cement this knowledge. Additionally, staying updated with the latest tools and practices ensures that your skills remain relevant and effective.
How to Approach Networking Inquiries

Networking-related inquiries are designed to test your understanding of how systems connect, communicate, and share resources within a network environment. These questions often cover topics like protocols, IP addressing, and troubleshooting network issues. A methodical approach is essential to provide accurate and effective responses, demonstrating both theoretical knowledge and practical expertise.
When addressing networking challenges, it’s important to break down the problem into manageable parts. Start by identifying the network components involved, the potential issues, and any relevant configuration settings. Once you have a clear picture, apply your knowledge of networking principles to propose the most likely solution. This structured approach ensures clarity and precision in your response.
Common Networking Topics to Review
Here’s a breakdown of key concepts that frequently appear in networking-related inquiries:
| Topic | Description |
|---|---|
| IP Addressing | Understanding IPv4 and IPv6, subnetting, and assigning addresses to devices. |
| Routing | Knowledge of how data travels between networks and different routing protocols. |
| Network Security | Configuring firewalls, VPNs, and securing communication channels. |
| DNS and DHCP | Managing domain name resolution and dynamic IP address allocation. |
| Troubleshooting | Diagnosing common connectivity issues and resolving them using tools like ping, tracert, or ipconfig. |
By focusing on these critical areas and practicing problem-solving techniques, you’ll be well-equipped to tackle any networking-related inquiries that arise during the certification process.
Key Features of Command Line Interface

The command line interface (CLI) provides a powerful and efficient way to interact with a computer’s operating system. By entering text-based commands, users can perform a variety of tasks, from file management to system configuration. Mastery of this tool is essential for anyone looking to enhance their ability to troubleshoot, automate tasks, or optimize performance.
One of the main advantages of using the command line is its speed. It allows users to execute commands directly without navigating through graphical interfaces, making it ideal for advanced users and system administrators. Additionally, the command line provides greater control over the operating environment, enabling users to run scripts, batch processes, or complex commands that would otherwise be cumbersome to perform manually.
Common Command Line Features
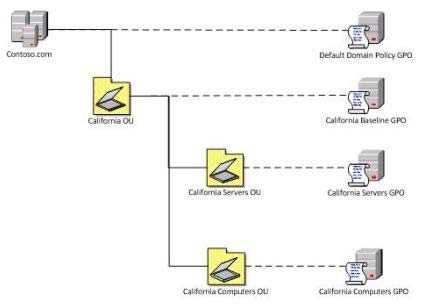
- File Management: Quickly create, delete, move, and modify files and directories using commands like dir, del, move, and copy.
- System Configuration: Adjust system settings, view configurations, or manage network settings using commands such as ipconfig and netstat.
- Scripting and Automation: Write batch files or PowerShell scripts to automate repetitive tasks, saving time and improving efficiency.
- Process Management: Monitor and manage running processes with commands like tasklist and taskkill.
- Network Diagnostics: Troubleshoot connectivity issues using tools such as ping, tracert, and nslookup.
Understanding these features allows users to efficiently navigate and manage their systems, especially in professional environments where time and precision are crucial.
Update and Patch Management Tips
Maintaining up-to-date software is crucial for ensuring system security and stability. Regular updates and patches help protect against vulnerabilities, improve performance, and introduce new features. Proper management of these updates can prevent issues such as software conflicts and system downtime. Understanding how to configure and apply updates effectively is key to maintaining a secure and efficient environment.
Best Practices for Update Management
Here are some best practices to consider when managing updates and patches:
- Set Automatic Updates: Enable automatic updates to ensure that critical security patches and system improvements are installed as soon as they are available.
- Review Update History: Regularly check update history to confirm which patches have been applied and to ensure no important updates are missed.
- Test Updates Before Deployment: For enterprise environments, test updates in a controlled environment to identify potential issues before they affect production systems.
- Keep Backups: Always have a current backup of your system before applying significant updates, especially those that change core system files.
- Schedule Updates During Off-Peak Hours: If possible, schedule updates during times when user activity is low to minimize disruptions and system downtime.
Handling Patch Management Challenges

Even with proper update management strategies, there can be challenges. Here are some tips for overcoming common issues:
- Addressing Update Failures: If updates fail to install, check error logs, and use built-in troubleshooting tools to resolve the issue.
- Compatibility Issues: Some updates might conflict with existing software or hardware. In these cases, check vendor compatibility guides or defer updates until solutions are available.
- Managing Large-Scale Updates: For larger environments, consider using software management tools to automate and monitor the update process across multiple devices.
By following these tips and staying proactive about system updates, you can ensure that your systems remain secure, stable, and well-maintained over time.
Important File System Concepts
Understanding how data is stored, organized, and managed on a computer is essential for both basic and advanced system administration tasks. File systems define how information is organized on storage devices and provide mechanisms for accessing, modifying, and protecting that data. Mastery of key concepts within file systems helps ensure efficient data management and troubleshooting, particularly when dealing with storage, permissions, and file integrity issues.
One of the primary functions of a file system is to enable easy access to data by defining how files are named, stored, and indexed. It also includes policies regarding security, access control, and file recovery. Knowledge of these concepts is crucial for optimizing system performance, managing storage resources, and securing data.
Key Concepts in File System Management
- File Allocation: Refers to how data is physically stored on disk, including methods such as contiguous, linked, and indexed allocation.
- Directory Structure: Organizes files into a hierarchical tree structure, enabling efficient file organization and retrieval. Common structures include single-level, two-level, and tree directories.
- File Permissions: Defines access levels for users and groups, determining who can read, write, or execute specific files or directories.
- Data Recovery: Involves methods and tools for recovering corrupted or deleted files, such as backup software or file system repair utilities.
- File Compression: Techniques used to reduce the size of files to save disk space and optimize storage, often through algorithms like ZIP or NTFS compression.
- File System Types: Different file systems (e.g., NTFS, FAT32, exFAT) offer distinct features and performance characteristics, which impact how data is managed and accessed.
File System Maintenance and Optimization
- Disk Defragmentation: The process of reorganizing fragmented data to improve access speeds and overall performance, particularly important for mechanical hard drives.
- Volume Shadow Copy: A feature that allows for taking backups of files even when they are in use, ensuring data consistency.
- File System Errors: Regularly checking and repairing file system errors helps prevent data loss and maintain integrity using utilities like chkdsk or fsck.
By understanding these key concepts, users can enhance their ability to manage data effectively, troubleshoot storage issues, and maintain a high-performing system.
Memory and Performance Management
Efficient management of system resources is crucial for maintaining optimal performance. Memory allocation and resource distribution directly impact how well a system operates under various workloads. Effective memory management ensures that applications run smoothly, and the system remains responsive even during high-demand tasks. Understanding how resources are allocated, optimized, and reclaimed is key to troubleshooting performance issues and maximizing the overall efficiency of a system.
Key Concepts in Memory Management
Memory management involves several core processes that help ensure a system operates efficiently. These include:
- Virtual Memory: A technique that allows systems to compensate for physical memory shortages by using disk space to simulate extra RAM.
- Page File: A portion of the disk set aside to hold parts of active programs and data that do not fit into physical memory.
- Memory Compression: A process that reduces the amount of data stored in physical memory to free up space for active processes, improving overall system performance.
- Memory Leaks: A situation where an application consumes more memory over time without releasing it, eventually slowing down the system.
- Heap and Stack Management: The ways in which memory is allocated and deallocated for programs, with stacks being used for function calls and heaps for dynamic memory allocation.
Improving System Performance
To maintain or improve system performance, several strategies and tools can be utilized:
- Task Manager: A built-in tool that allows users to monitor system resources, identify high-resource processes, and optimize performance by terminating unnecessary tasks.
- Performance Troubleshooter: A tool that automatically diagnoses and provides solutions for performance-related issues, such as high CPU usage or memory bottlenecks.
- Disk Cleanup and Defragmentation: Regularly clearing out temporary files and defragmenting the disk can improve read/write speeds and overall responsiveness.
- Adjusting Startup Programs: Limiting the number of programs that launch during system startup can significantly improve boot times and resource usage.
- Resource Allocation Settings: Tweaking virtual memory settings and optimizing the allocation of system resources can ensure a smoother user experience under heavy load.
By understanding and applying these memory management techniques and performance optimization strategies, users can enhance the overall speed and responsiveness of their systems, even under challenging conditions.
Understanding User Account Management
Proper management of user accounts is vital for ensuring security and efficient operation of any system. By controlling user access, administrators can ensure that only authorized individuals can access certain resources or perform specific tasks. The ability to configure permissions, manage groups, and set appropriate restrictions is crucial for maintaining a well-organized and secure environment.
Types of User Accounts
Different types of accounts provide varying levels of access and control. These include:
- Administrator Accounts: These accounts have full control over system settings and resources, allowing users to make changes that affect the entire system.
- Standard User Accounts: These accounts are limited to using applications and performing tasks that do not require administrative privileges, offering a more secure environment.
- Guest Accounts: These are temporary accounts with very limited access, typically used for people who need basic access without any customization or system changes.
- Service Accounts: These accounts are used by system processes and applications, often running in the background with specific permissions to perform necessary tasks.
Account Permissions and Control
Managing permissions is crucial to ensuring the right users have access to the right resources. Key concepts include:
- User Groups: Groups help to simplify permission management by assigning specific rights to a group of users rather than to individuals. Common groups include Administrators, Users, and Guests.
- Access Control Lists (ACLs): ACLs define the permissions granted to users or groups for specific resources, such as files, folders, or network devices.
- File and Folder Permissions: Permissions control who can read, write, or execute files and directories. These can be set to apply to individual users or groups.
- Account Lockout Policies: These policies determine how many failed login attempts will trigger a lockout, preventing unauthorized access attempts and protecting the system.
By understanding these key elements of account management, system administrators can ensure a balance of security, efficiency, and usability, ensuring that users have appropriate access while minimizing security risks.
Tips for Passing the Certification Exam
Achieving certification can be a crucial step in advancing your career. Proper preparation is key to successfully navigating the various sections of the assessment. Understanding the material, practicing problem-solving, and familiarizing yourself with the exam format are essential components of an effective study strategy.
Effective Study Strategies
Adopting the right approach to your preparation can make a significant difference in your performance. Consider these tips:
- Understand the Exam Structure: Familiarize yourself with the types of topics covered and the format of the questions. Knowing the areas that are most likely to appear will help you allocate time more efficiently.
- Practice with Real-Life Scenarios: Engage in hands-on practice by setting up virtual labs or environments that mimic real-world situations. This will help solidify your understanding of the concepts.
- Review Official Study Guides: Use study materials provided by the certification organization. These resources are designed to cover all necessary topics in detail and often include sample questions.
- Join Study Groups or Forums: Discussing with peers can help clarify difficult concepts and provide different perspectives. Many online forums offer insights into common pitfalls and study strategies.
Time Management Tips
Effective time management can enhance your exam readiness:
- Create a Study Schedule: Break down the topics into manageable sections and allocate time for each. Stick to a consistent study routine to avoid cramming.
- Practice Time Management During the Exam: During practice sessions, set time limits to simulate the real exam environment. This will help you pace yourself and avoid spending too much time on any one question.
- Focus on Weak Areas: Identify your weak points early in the preparation process and dedicate extra time to those topics. Strengthening these areas will increase your confidence.
On the Day of the Test
When it’s time to take the test, staying calm and prepared is crucial:
- Get a Good Night’s Sleep: Resting well the night before will help you stay alert and focused during the exam.
- Read Each Question Carefully: Take your time to fully understand each prompt before selecting your answer. Avoid rushing through questions, as this may lead to mistakes.
- Use Process of Elimination: If you’re unsure of an answer, try to eliminate obviously incorrect choices. This increases your chances of selecting the correct answer even if you’re unsure.
Sample Study Resources
| Resource | Type | Description |
|---|---|---|
| Official Study Guides | Textbook | Comprehensive materials covering all topics included in the assessment. |
| Practice Tests | Online | Simulated tests to help you familiarize yourself with the format and timing. |
| Discussion Forums | Online | Communities where you can ask questions, share knowledge, and get advice. |
By following these strategies, you’ll be better equipped to approach the assessment with confidence and increase your chances of success.
Hardware Compatibility and Drivers
Ensuring that hardware components are compatible with an operating system is essential for system stability and performance. Compatibility issues can lead to crashes, performance degradation, or hardware malfunctions. Properly installed and updated drivers are crucial for seamless interaction between hardware devices and software, enabling smooth functionality.
Key Considerations for Hardware Compatibility
Before installing new hardware or upgrading existing components, it’s important to understand several key factors that can affect compatibility:
- System Architecture: Ensure that the hardware is designed to work with the system’s architecture, whether it is 32-bit or 64-bit. Incompatible hardware may not function correctly or may require additional software configurations.
- Driver Availability: Verify that the necessary drivers for your hardware are available and compatible with your current operating system version. Manufacturers often release driver updates to support newer systems or fix bugs.
- Hardware Specifications: Check that the hardware meets the minimum or recommended system requirements. Using components that are not supported by the system can lead to a suboptimal experience.
- Firmware and BIOS Compatibility: Ensure that the system firmware and BIOS are up to date to avoid conflicts with newly installed hardware components.
Managing and Installing Drivers
Proper driver management is crucial for ensuring that hardware devices function correctly and efficiently. Here’s how to handle drivers:
- Automatic Installation: Many modern operating systems can automatically detect and install compatible drivers for most hardware. This process simplifies the setup, but it’s important to check if the most recent driver version is being used.
- Manual Installation: In some cases, you may need to manually install drivers, especially for specialized hardware. Visit the manufacturer’s website to download the latest drivers and follow the installation instructions.
- Driver Updates: Regularly check for driver updates to ensure optimal performance. New drivers can provide enhancements, fix bugs, and improve compatibility with other software.
- Device Manager: Use the built-in device management tools to troubleshoot and update drivers. If a device is not working properly, the Device Manager can provide useful information on whether the driver is missing or needs an update.
By understanding the importance of hardware compatibility and properly managing drivers, users can ensure that their systems run smoothly and efficiently, avoiding many of the common issues related to incompatible devices or outdated software.
Backup and Recovery Essentials
Protecting your data through regular backups and having a recovery plan in place is essential for safeguarding against hardware failures, software corruption, or accidental data loss. Understanding the core concepts and tools available for backing up data and restoring it to a working state is critical for system reliability and peace of mind.
Key Concepts in Data Protection
When setting up a backup and recovery plan, there are several key principles and methods to consider:
- Regular Backups: Backing up data regularly ensures that recent changes are preserved. It’s essential to choose a backup schedule that fits your needs, whether it’s daily, weekly, or monthly.
- Storage Locations: Choose secure storage locations for backups. Options include external drives, cloud storage, and network-attached storage (NAS) solutions. Each has its advantages and limitations based on your specific requirements.
- Backup Types: Understand the different backup types available:
- Full Backup: Copies all selected data in its entirety. This is the most comprehensive backup type but can take longer to complete.
- Incremental Backup: Backs up only the data that has changed since the last backup, making it faster and more storage-efficient.
- Differential Backup: Backs up changes since the last full backup, offering a balance between speed and data coverage.
Recovery Options and Tools
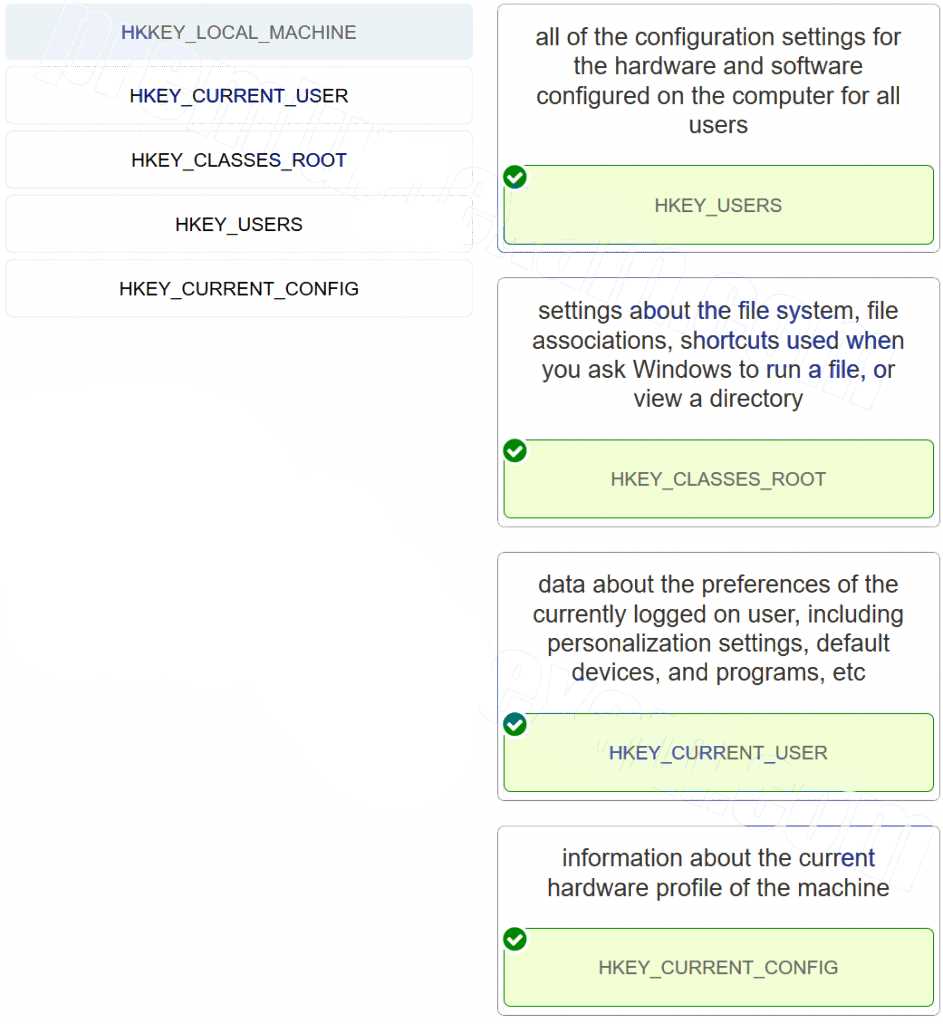
Having a reliable recovery strategy is just as important as backing up data. Here are some of the most commonly used tools and methods:
- System Restore: A built-in recovery tool that allows you to restore your system to a previous state. This is useful for undoing changes that may have caused system instability.
- Recovery Drive: Creating a recovery drive can help restore the system to its factory settings or troubleshoot problems when the operating system fails to boot.
- Backup Image: A system image is a complete snapshot of your system, including the operating system, applications, and settings. It allows for a full restoration of the system to a working state after a major failure.
- Cloud Backup: Cloud-based solutions offer the benefit of remote access and off-site storage, ensuring that your data is protected in case of a local disaster, such as fire or theft.
By understanding and implementing effective backup strategies and having recovery solutions in place, users can minimize the risks of data loss and ensure they can restore their systems to a functional state when needed.