Unauthorized Disclosure of Exam Answers and How to Prevent It

In educational environments, the integrity of assessments plays a crucial role in ensuring fairness and maintaining trust. When sensitive information related to tests or evaluations is shared without permission, it undermines the credibility of the entire process. The security of such materials is vital not only for the success of students but also for upholding the standards of academic institutions.
Preventing unauthorized sharing of assessment content is essential to maintain the value of academic achievements. When such breaches occur, they can distort the outcomes of evaluations and lead to unfair advantages for certain individuals. As educational systems become more reliant on digital tools and platforms, safeguarding this information is more challenging yet more important than ever.
To effectively protect academic assessments, it is necessary to adopt a multifaceted approach that includes technological solutions, strict policies, and ongoing awareness efforts among students, faculty, and administrative staff. By addressing these concerns proactively, institutions can reduce the risk of confidential materials being compromised.
Unauthorized Disclosure of Exam Answers
When confidential test content or evaluation results are shared inappropriately, it disrupts the integrity of the assessment process. This type of breach not only compromises the fairness of the process but also creates significant ethical concerns for all parties involved. It is essential for institutions to identify and address any risks associated with the leakage of evaluation materials to preserve the credibility of academic achievements.
Risks of Information Leaks
Leaks of evaluation-related information can have severe consequences. When students or external parties gain access to test materials before the official release, it gives certain individuals an unfair advantage. This undermines the principle of merit-based performance and can result in the invalidation of results, leading to disputes over the accuracy of assessments. Additionally, widespread leaks can diminish public trust in the education system.
Measures to Prevent Information Breaches
Preventing these types of security breaches requires a combination of proactive monitoring, secure handling of sensitive materials, and clear institutional policies. Educators must ensure that all involved parties understand the importance of safeguarding test content, and institutions should implement strict digital security protocols to prevent unauthorized access. Furthermore, promoting a culture of academic integrity among students is key to reducing the likelihood of such incidents occurring.
Understanding Exam Answer Confidentiality
The confidentiality of evaluation materials is a cornerstone of maintaining fairness and trust in educational systems. Safeguarding these materials ensures that all students are assessed based on their own abilities, without the interference of external influences. The protection of such information is essential to prevent unfair advantages and to maintain the integrity of the academic process.
The Importance of Secure Test Content
When test-related content is kept secure, it guarantees that every individual has an equal opportunity to perform based on their knowledge. This prevents the potential for cheating and upholds the credibility of results. Educational institutions must recognize the critical role that confidentiality plays in shaping public confidence in their assessment processes.
Challenges in Maintaining Confidentiality
With the rise of digital platforms and online assessments, protecting confidential materials has become more complex. However, implementing strong security measures and fostering a culture of academic integrity are key components in reducing the risks of content leakage. Institutions must stay vigilant and continually adapt to evolving technologies to ensure the safety of their evaluation processes.
| Security Measure | Description | Effectiveness |
|---|---|---|
| Digital Encryption | Protects test content with advanced coding systems | Highly effective in preventing unauthorized access |
| Secure Storage | Physical or digital methods to protect test materials | Reduces risk of physical theft or digital breaches |
| Limited Access | Restricting access to materials to authorized personnel only | Essential for reducing potential leaks |
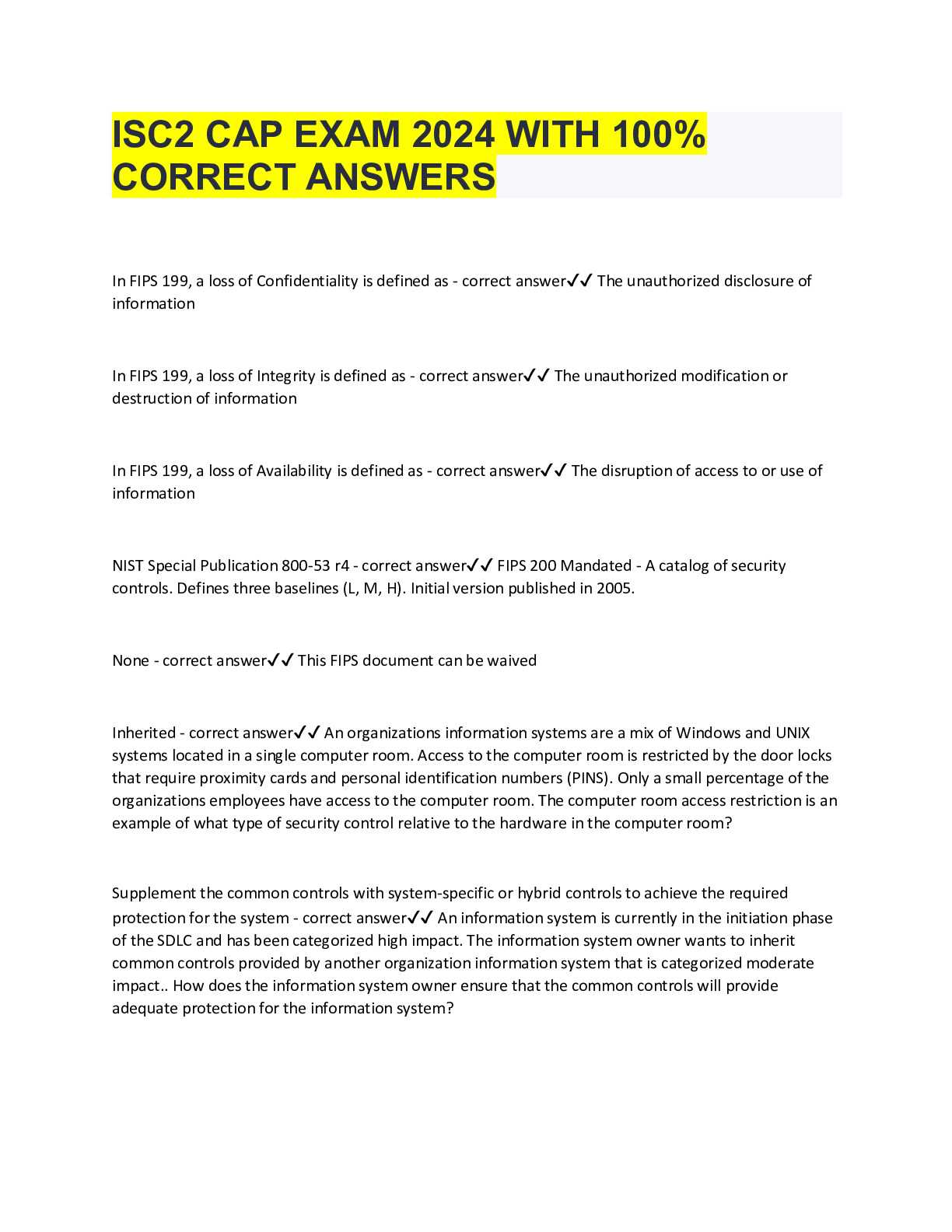
Risks of Unauthorized Answer Disclosure
When sensitive educational materials are shared without permission, it can lead to significant consequences. These breaches can affect not only the individuals involved but also the broader academic community. The risks associated with such leaks can damage the credibility of the institution and create an unfair environment for all students.
Impact on Fairness and Integrity
Leaks of test-related materials disrupt the fairness of the evaluation process. Students who gain access to this information have an unfair advantage over their peers, compromising the integrity of academic assessments. This can lead to the following consequences:
- Unfair Academic Advantages: Those with prior knowledge of test content can perform better than others, distorting the true reflection of their abilities.
- Loss of Credibility: If leaks are widespread, it can undermine the public trust in educational systems and assessments.
- Damaged Student Morale: Honest students may feel demotivated or frustrated when they perceive an unfair advantage given to others.
Legal and Institutional Consequences
In addition to fairness issues, unauthorized sharing of evaluation content can lead to severe legal and institutional consequences. These include:
- Legal Penalties: In some cases, sharing test information can result in criminal charges or legal actions against those responsible.
- Institutional Repercussions: Educational institutions may face reputational damage, loss of accreditation, or financial penalties.
- Academic Consequences: Students involved in such leaks may face expulsion or other disciplinary actions, further harming their academic careers.
Legal Consequences of Answer Leaks
When sensitive evaluation materials are improperly shared, the legal repercussions can be severe for both individuals and institutions involved. Such leaks undermine the integrity of the assessment process and can lead to criminal charges, civil lawsuits, and significant institutional damage. Understanding the potential legal risks is crucial for preventing these breaches and ensuring the continued credibility of academic environments.
Criminal Charges for Breaching Confidentiality
In many jurisdictions, the unauthorized sharing of test content is a serious offense, often classified under laws related to fraud, intellectual property theft, or data protection violations. Individuals found guilty of leaking such materials can face legal penalties, including:
- Fines: Significant monetary penalties can be imposed on those who distribute test content without authorization.
- Imprisonment: In extreme cases, individuals may face jail time depending on the severity of the breach and local laws.
- Criminal Records: A conviction can result in a permanent criminal record, affecting future opportunities for employment and education.
Institutional Liability and Consequences
Educational institutions can also face legal consequences if test-related content is leaked under their watch. They may be held liable for failing to adequately protect sensitive materials. Possible consequences include:
- Loss of Accreditation: Repeated security breaches can lead to the loss of accreditation from educational boards or government bodies.
- Lawsuits: Students or third parties may file civil lawsuits against institutions for failing to secure test materials properly.
- Damage to Reputation: Public perception of the institution may suffer, leading to a decline in enrollment and loss of public trust.
How Cheating Affects Academic Integrity
Cheating undermines the core values of education by distorting the true reflection of a student’s abilities. When individuals resort to dishonest practices to gain an advantage, it compromises the fairness of the entire academic system. This leads to a breakdown in trust between students, educators, and institutions, ultimately affecting the credibility of the educational process.
Consequences for Students and Institutions
Cheating not only affects the individual’s reputation but also damages the integrity of the institution that allows such practices to persist. The consequences can be far-reaching:
- Loss of Academic Reputation: Students involved in cheating may face long-term damage to their credibility, impacting future career opportunities and academic pursuits.
- Decline in Institutional Trust: Institutions that fail to prevent cheating risk losing the trust of both students and the public, potentially leading to a drop in enrollment and funding.
- Legal and Ethical Ramifications: In some cases, educational institutions may face legal actions if they do not address widespread dishonesty, leading to sanctions or financial penalties.
The Broader Impact on Educational Systems
Widespread cheating can create a toxic environment where hard work is devalued, and dishonest behavior is normalized. This sets a dangerous precedent for future generations of students who may feel that success can be achieved without integrity.
| Effect | Description |
|---|---|
| Decreased Motivation | Students who follow ethical standards may feel demotivated when they see others gaining unfair advantages. |
| Lower Academic Standards | Cheating can lead to a reduction in the quality of education, as dishonest practices are more likely to go unchecked. |
| Negative Reputation | Both students and institutions that tolerate cheating may develop a negative public image, impacting future opportunities. |
Common Ways Test Information Is Leaked
There are several methods through which confidential assessment materials or content may be improperly shared. These leaks can occur at various stages of the evaluation process, from preparation to distribution, and can involve different parties, including students, staff, or external individuals. Identifying common leakage points is essential for implementing better security measures.
Digital and Online Leaks
In today’s digital age, online platforms have become a primary source for unauthorized sharing of test-related materials. Some of the most common digital methods include:
- Social Media Sharing: Students or outsiders may use platforms like social media to post or distribute test content during or before the assessment.
- File Sharing Platforms: Leaked documents can be uploaded to file-sharing sites, making it easy for others to access sensitive materials.
- Hacking into School Systems: Unauthorized individuals may breach school networks or databases to obtain and release test content.
Physical Leaks and Insider Sharing
While digital leaks are common, physical sharing of test information remains a significant concern. These methods often involve insiders with direct access to sensitive materials. Some common physical leakage methods include:
- Printed Materials Distribution: Physical copies of tests may be stolen or copied and distributed to others who are not authorized to see them.
- Sharing via Word of Mouth: Students or staff members may verbally share content or questions from the test, particularly when the material is not secured properly.
- Leaked through Collaboration: Students may collaborate by sharing information during or after the test, leading to unfair advantages.
Preventing Unauthorized Disclosure in Schools
Educational institutions must take proactive steps to ensure that sensitive materials remain secure throughout the assessment process. Establishing clear policies and implementing robust security measures can significantly reduce the risk of leaks. By addressing potential vulnerabilities and fostering a culture of academic integrity, schools can safeguard their evaluation processes and maintain trust within the community.
Implementing Robust Security Protocols
One of the most effective ways to prevent leaks is through the implementation of strict security measures at every stage of the testing process. These protocols should include:
- Digital Protection: Utilizing encryption and secure file-sharing systems to protect materials stored or transmitted electronically.
- Physical Security: Ensuring that printed test papers are locked away in secure locations before and after the assessment period.
- Restricted Access: Limiting access to test materials to only authorized personnel, reducing the chances of accidental or intentional leaks.
Fostering a Culture of Integrity
In addition to technical security measures, it’s essential to create an environment where students and staff understand the importance of academic honesty. This can be achieved by:
- Clear Communication: Informing all stakeholders about the consequences of leaking confidential materials, both academically and legally.
- Training and Awareness: Regularly educating both students and staff about the importance of confidentiality and the potential repercussions of dishonest actions.
- Promoting Accountability: Encouraging a system of self-regulation where individuals are aware of their responsibility to uphold academic standards.
Technology and Its Role in Answer Protection
In today’s digital age, technology plays a crucial role in securing confidential test materials and maintaining the integrity of assessments. From encryption tools to advanced monitoring systems, technological solutions help protect sensitive information from being compromised. By integrating these innovations, educational institutions can create a more secure and controlled environment, reducing the risks of unauthorized access or sharing.
One of the key benefits of technology is its ability to secure both physical and digital test content. Schools and universities can implement secure online platforms, monitor test environments with surveillance tools, and use encryption to safeguard documents, ensuring that unauthorized parties are unable to access or leak test-related materials.
Moreover, technology provides real-time monitoring capabilities, allowing educators to track and respond quickly to any suspicious activity. Automated systems can flag irregularities during testing, such as unusual access patterns or attempts to share content, providing an added layer of protection against potential breaches.
How to Identify Exam Answer Leaks
Detecting when confidential testing materials have been compromised is crucial for maintaining the integrity of academic assessments. Early identification of leaks can help mitigate damage and prevent further unauthorized access. By understanding the common signs of information breaches, institutions can take swift action to address the issue and protect the interests of all stakeholders involved.
Indicators of Potential Leaks
There are several warning signs that may suggest test materials have been leaked. These include:
- Unexpected Patterns in Performance: A sudden increase in high scores, particularly when they don’t align with previous performance trends, can indicate that some students may have gained unfair access to the content.
- Widespread Similarities in Responses: When a large number of students provide identical or near-identical responses, it may suggest that test content has been shared inappropriately.
- Irregular Access to Materials: If there are reports of students or staff members accessing test materials from unauthorized sources or locations, it could point to a leak.
- Social Media Activity: Unexplained mentions of test details or questions on social media platforms before the assessment can indicate that information has been prematurely released.
Methods for Investigation
To confirm a potential leak, institutions can use various investigative methods:
- Examining Digital Footprints: Monitoring digital platforms and communication channels for any signs of unauthorized sharing, including file uploads, links, or discussion forums.
- Conducting Randomized Testing: Using randomized questions and secure environments can help identify if certain students are consistently outperforming their peers in a way that is inconsistent with their typical abilities.
- Tracking Document Changes: Reviewing file access logs and document revisions can help determine if test materials were accessed or altered without authorization.
Building Trust Between Students and Teachers
Establishing a strong, respectful relationship between educators and students is essential for creating an environment where academic integrity thrives. When students trust their teachers, they are more likely to follow rules and engage honestly in their learning process. A transparent and supportive atmosphere helps prevent dishonest behaviors and encourages a culture of mutual respect and responsibility.
Open Communication and Transparency
One of the most effective ways to build trust is through consistent, open communication. Educators should make an effort to explain expectations clearly and address any concerns students may have. Creating a space where students feel comfortable asking questions or discussing challenges fosters an environment of understanding and collaboration. Teachers who are transparent about the assessment process and its importance are more likely to gain the trust and cooperation of their students.
Encouraging Positive Academic Values
Trust is further strengthened when teachers actively promote ethical behavior and highlight the importance of fairness and honesty in academics. Emphasizing these values through classroom discussions, rewards for integrity, and by setting examples through their own actions, teachers can encourage students to uphold the same principles. A positive academic culture where students feel valued and respected reduces the temptation to engage in dishonest practices.
The Importance of Secure Exam Systems
Implementing robust and secure systems for assessments is essential for preserving the integrity of the testing process. When sensitive materials are protected from unauthorized access, the fairness of the evaluation is maintained, and trust in the institution’s academic standards is reinforced. Secure systems help safeguard against fraudulent activities and ensure that results are a true reflection of students’ abilities.
A secure assessment system minimizes the risk of cheating and data breaches. By employing modern technological solutions, institutions can prevent unauthorized parties from accessing or manipulating test content. This creates an environment where both students and educators feel confident in the integrity of the process.
Key Features of Secure Systems
Several important features contribute to the security of assessment systems. These include:
- Data Encryption: Encrypting digital files ensures that sensitive information remains protected during transmission and storage.
- Access Control: Restricting access to authorized personnel only helps prevent leaks or unauthorized alterations to the test materials.
- Secure Platforms: Utilizing trusted online assessment platforms with secure logins and monitoring capabilities reduces the chances of fraudulent activity.
Benefits of Secure Systems
By adopting secure testing systems, educational institutions enjoy a variety of benefits:
- Maintaining Fairness: Secure systems level the playing field, ensuring that all students are assessed under the same conditions.
- Building Credibility: A secure environment enhances the credibility of the institution, assuring students, staff, and the public that academic standards are upheld.
- Reducing Risks: Effective security measures significantly reduce the risk of cheating, fraud, and other dishonest practices.
Training Staff to Prevent Answer Disclosure
Effective training of staff members is crucial for maintaining the integrity of the academic process. Educators, administrators, and other staff involved in assessments should be equipped with the knowledge and skills to identify potential risks and prevent any unauthorized sharing of materials. Training should focus on recognizing security vulnerabilities, understanding ethical responsibilities, and implementing proper procedures to ensure confidentiality is upheld throughout the assessment process.
Key Areas of Staff Training
Staff training should cover several important areas to ensure the secure handling of assessment content:
| Area | Description |
|---|---|
| Confidentiality Protocols | Staff should be familiar with the strict confidentiality protocols that govern the handling of test materials, including storage, distribution, and disposal of documents. |
| Ethical Guidelines | Training should emphasize the importance of maintaining high ethical standards and discourage any behavior that could compromise the fairness of assessments. |
| Monitoring and Supervision | Staff should be trained to effectively monitor test-taking environments, ensuring that students do not have the opportunity to access or share materials inappropriately. |
| Incident Reporting | Staff members should know how to report any suspicious activity or breaches in protocol promptly to ensure immediate action is taken. |
Benefits of Proper Training
Proper training helps create a secure testing environment where both staff and students feel confident in the integrity of the process. The benefits of well-trained staff include:
- Improved Security: Trained staff are more capable of spotting and preventing potential leaks, reducing the risk of compromising test materials.
- Fostering a Culture of Integrity: When staff understand the importance of their role in maintaining fairness, it encourages a culture of honesty and accountability among students.
- Quick Response to Issues: Staff can respond more effectively and swiftly to any security concerns or incidents, minimizing the potential impact.
Student Responsibility in Preventing Cheating
Students play a critical role in ensuring that the integrity of the academic environment is maintained. While institutions and staff can implement security measures, it is ultimately the responsibility of the students to act ethically and avoid engaging in dishonest behavior. Understanding the consequences of cheating and the importance of personal accountability can help foster a culture of integrity and fairness within educational settings.
Students must be aware of the potential consequences of participating in dishonest practices, not just for themselves but for their peers and the institution as a whole. By following established guidelines and respecting the integrity of the assessment process, they help uphold a system that values hard work and genuine achievement.
How Students Can Contribute to Integrity
There are several ways students can actively contribute to preventing unethical behavior during assessments:
- Respecting Confidentiality: Students should not share test materials or discuss content inappropriately with others before, during, or after assessments.
- Avoiding Plagiarism: Students should ensure that all their work is original and properly credited, avoiding any form of copying or using others’ work without permission.
- Following the Rules: Abiding by all rules regarding the use of electronic devices, written materials, and other resources during assessments is essential to maintaining fairness.
Benefits of Upholding Academic Integrity
When students take responsibility for their actions and contribute to the maintenance of academic integrity, several positive outcomes follow:
- Personal Growth: Students who maintain honesty in their work develop a stronger sense of self-respect and personal achievement.
- Fairness for All: By avoiding dishonest behavior, students help ensure that their grades accurately reflect their own abilities and efforts.
- Stronger Reputation: Students who uphold academic integrity contribute to a positive reputation for both themselves and the institution.
Ethical Implications of Answer Sharing
Sharing test materials or results without permission can have significant ethical consequences, affecting not only those directly involved but also the broader academic community. While it may seem harmless or even helpful in some cases, the act of passing on sensitive academic content undermines the values of fairness and personal effort that are central to any learning environment.
When students share information about evaluations or assignments, it creates an uneven playing field. This action disrupts the level of competition among peers, as it allows some individuals to benefit from others’ hard work without putting in the same effort themselves. Moreover, such behavior can erode trust between students and educators, diminishing the credibility of the entire educational system.
The ethical implications go beyond the immediate consequences for the individuals involved. When academic integrity is compromised, it devalues the accomplishments of others who follow the rules and rely on their own efforts. This can also have a ripple effect, influencing the behavior of future generations of students who may view dishonest practices as acceptable.
How Schools Handle Answer Leaks
Educational institutions take the protection of sensitive materials very seriously, and when there is an incident involving the unauthorized circulation of test content, schools have established procedures to address the situation. The response typically involves a combination of immediate action, investigation, and preventative measures to minimize the impact and prevent future occurrences.
Once an incident is detected, the first step is often to assess the scale of the breach and identify the individuals involved. Schools may work with technology teams to trace the source of the leak and determine how the information was shared. Depending on the severity of the situation, disciplinary actions may be taken, which could range from warnings to more severe consequences such as expulsion or academic penalties.
In addition to immediate responses, schools often take proactive steps to strengthen their systems. This can involve enhancing security measures, providing additional training for staff and students, and reviewing protocols for handling sensitive materials. By doing so, institutions aim to reduce the risk of similar breaches in the future and reinforce the importance of academic integrity within the learning environment.
Tips for Maintaining Exam Answer Security
Ensuring the confidentiality of assessment content is crucial to maintaining the integrity of the academic process. There are several strategies that both institutions and students can employ to prevent leaks and preserve the fairness of evaluations. By following some key practices, the risk of sensitive information being compromised can be significantly reduced.
One important step is to limit access to assessment materials. This includes controlling who has permission to view or handle such content, as well as using secure platforms for digital submissions. In addition, physical security measures like locked storage or restricted areas can help safeguard paper-based materials.
For those involved in the creation and management of evaluations, it is essential to regularly update security protocols. Using encrypted files, password-protected documents, and multi-factor authentication for online platforms can prevent unauthorized access. Furthermore, clear guidelines and training for staff regarding the handling and distribution of test-related materials are key to ensuring everyone understands their responsibilities.
Finally, fostering a culture of integrity among students is vital. Schools should educate students about the importance of maintaining confidentiality and the potential consequences of breaches. Encouraging open communication and creating an environment where students feel responsible for upholding academic standards can go a long way in preventing security issues.
The Future of Exam Answer Protection
As educational institutions continue to evolve, so too does the need for advanced methods to protect sensitive assessment materials. With increasing reliance on digital platforms and technology, new strategies and tools are emerging to safeguard the integrity of evaluations. The future of securing test-related content will likely involve a combination of technological innovation, stricter protocols, and greater awareness across educational communities.
One area of development is the use of artificial intelligence (AI) and machine learning to detect suspicious activity or breaches in security. AI can help analyze patterns of behavior and identify potential threats before they escalate. This could include spotting anomalies in how test materials are accessed or flagged interactions between individuals who should not be communicating during an assessment.
Additionally, blockchain technology is gaining attention for its ability to provide tamper-proof records. By using blockchain, assessment materials could be securely stored and tracked, ensuring that no unauthorized modifications or leaks occur. This system would also make it easier to trace the origin of any security breach, helping to prevent future incidents.
In the coming years, institutions may also prioritize multi-layered security systems. These could combine biometric verification, such as fingerprint scanning or facial recognition, with other advanced security measures like encrypted communications and secure cloud storage. Such systems would create multiple barriers against unauthorized access, offering a higher level of protection for sensitive materials.
Furthermore, as schools and universities place greater emphasis on academic integrity, collaboration between educators, administrators, and students will become even more essential. Building a culture of respect for assessment confidentiality, supported by clear policies and effective enforcement mechanisms, will remain a key factor in preventing breaches.
Overall, the future of safeguarding test-related materials lies in a proactive approach that integrates cutting-edge technology with a strong commitment to academic values and security. By embracing new tools and fostering a community of integrity, educational institutions can continue to protect their assessments in a rapidly changing world.