HIPAA Privacy Test Answers and Key Insights
When working with sensitive information, it is essential to understand the rules and standards that govern the handling of personal data. These guidelines are in place to ensure that individuals’ confidential details are secured and only accessed by authorized personnel. Navigating these principles can be challenging, but mastering them is crucial for maintaining trust and compliance in various industries.
In this section, we will explore the fundamental concepts related to data confidentiality and the measures that need to be taken to protect it. By understanding the core regulations, professionals can avoid common mistakes and ensure they are following the best practices. Being knowledgeable in this area is not just a requirement but a responsibility for anyone involved in managing personal or medical records.
Preparedness is key when aiming to comprehend these complex regulations. With the right approach, anyone can grasp the essential elements needed to comply with these standards and pass assessments designed to test one’s understanding. This section will provide you with valuable insights and helpful tips for success in this area.
HIPAA Privacy Test Answers Overview
In many industries, understanding and applying the rules surrounding the protection of sensitive data is essential for maintaining trust and ensuring legal compliance. For those tasked with managing confidential information, it is important to have a strong grasp of the key regulations that govern its use and storage. This section provides an overview of the critical aspects that individuals must be familiar with when assessing their knowledge of data safeguarding practices.
Core Principles of Data Security
At the heart of these regulations lies the concept of data security, which focuses on the proper handling and safeguarding of personal and health-related information. Compliance with these principles ensures that sensitive data remains protected from unauthorized access, alteration, and disclosure. Understanding these foundational rules is essential for anyone working with private records in healthcare or other related fields.
Evaluating Knowledge and Preparedness
Assessing one’s knowledge of these regulations involves understanding not just the theoretical aspects but also how to implement these rules effectively in real-world scenarios. Professionals must be able to identify the common risks associated with data handling and apply preventive measures. Thorough preparation and familiarity with the critical guidelines will help ensure compliance and avoid costly mistakes that could result in breaches of confidentiality.
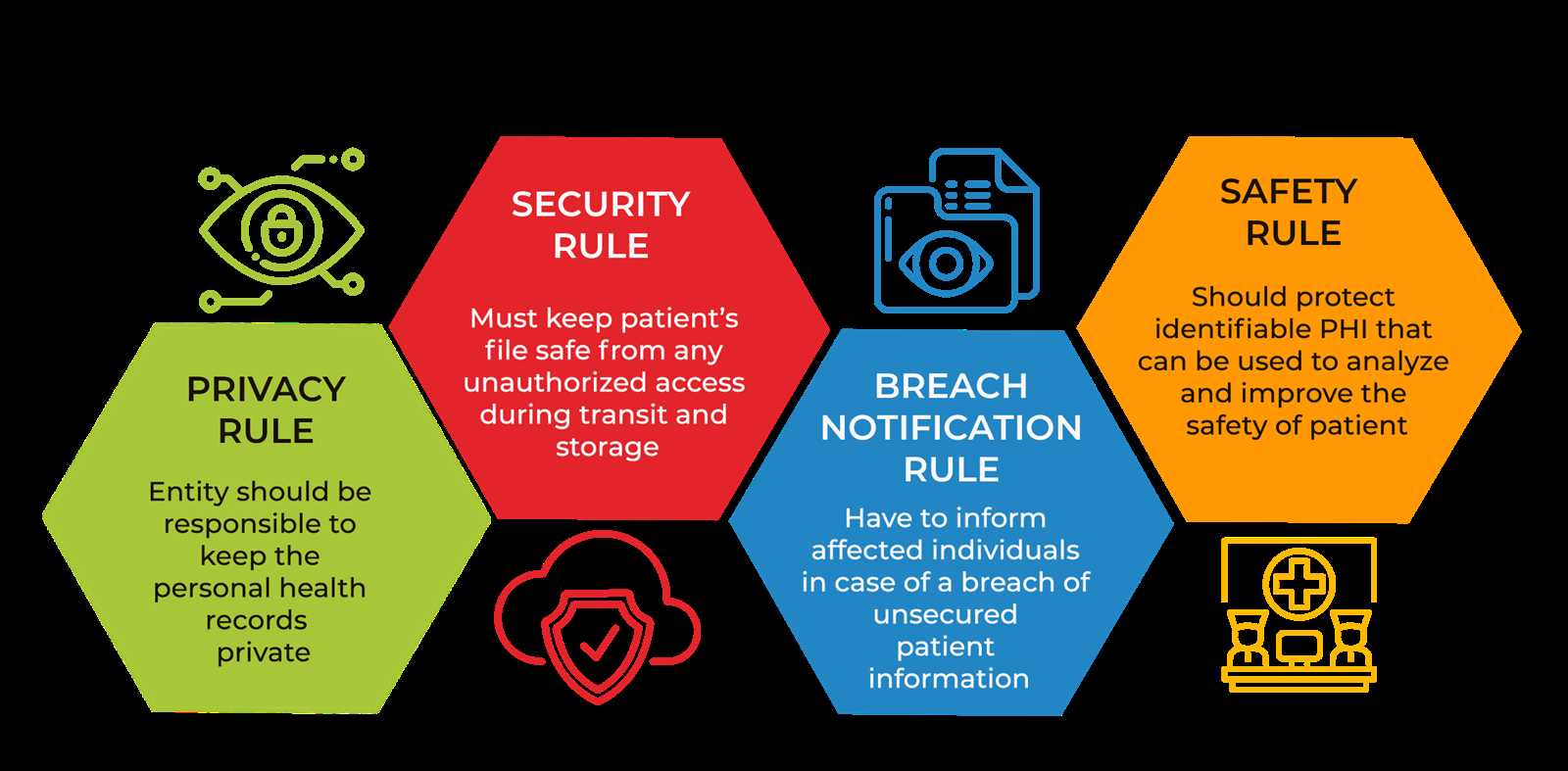
Understanding HIPAA Privacy Rules
When it comes to handling confidential information, certain guidelines must be followed to ensure the security and integrity of sensitive data. These rules are designed to protect individuals’ personal details and restrict unauthorized access to their records. Understanding the core principles of these standards is essential for anyone involved in managing or working with private data in healthcare and other regulated industries.
The regulations focus on how information should be stored, shared, and protected to prevent misuse or breaches. They emphasize the importance of implementing proper safeguards to ensure that only authorized individuals can access certain data. Professionals in this field must be equipped with the knowledge of these standards to minimize risks and ensure full compliance with legal requirements.
Adherence to these guidelines is not just about preventing violations but also about fostering trust between organizations and their clients. Effective data management practices help maintain confidentiality, transparency, and accountability in everyday operations. Understanding these rules is fundamental for anyone looking to build or sustain a career in data security and compliance.
Key Concepts in HIPAA Compliance
Understanding the fundamental principles that govern the protection of sensitive information is crucial for anyone working with personal data in regulated environments. These key concepts form the foundation for safeguarding private details, ensuring that they are handled with care and only accessible to those with proper authorization. Familiarity with these principles is essential to maintaining both compliance and trust in any industry that handles confidential records.
Access Control and Security Measures
One of the primary concepts involves establishing strict access controls to prevent unauthorized individuals from viewing or modifying sensitive information. Organizations must implement robust security measures such as encryption, secure passwords, and user authentication processes to protect data from potential threats. These practices help ensure that information is only accessible to those with a legitimate need to know.
Data Retention and Disposal Policies
Equally important is the proper retention and secure disposal of personal information. Regulations outline how long data can be retained and the procedures for safely eliminating it when no longer needed. This ensures that information is not exposed to unnecessary risk and is destroyed in a way that prevents it from being recovered or misused. Proper handling of data is vital for maintaining confidentiality and legal compliance.
Common HIPAA Privacy Test Questions
In order to evaluate one’s knowledge of essential data protection practices, certain questions are frequently posed to assess understanding of the core principles. These questions typically cover a range of topics related to the security of personal information, its proper handling, and the associated legal requirements. Preparing for such inquiries can help ensure compliance and a deeper understanding of the best practices for safeguarding sensitive data.
| Question | Focus Area |
|---|---|
| What is considered confidential information under these regulations? | Definition of Sensitive Data |
| Who is authorized to access sensitive records? | Access Control |
| What are the best practices for disposing of confidential records? | Data Disposal |
| What security measures are required to protect sensitive data? | Data Security Measures |
| How can compliance be verified within an organization? | Compliance Auditing |
Importance of Patient Data Protection
The protection of sensitive personal information is a cornerstone of healthcare and other industries where private data is collected and processed. Ensuring that this information remains secure not only builds trust between individuals and organizations but also safeguards against potential harm that could arise from unauthorized access. Failing to properly protect this data can have severe legal, financial, and reputational consequences.
Why Data Protection Matters
When confidential information is compromised, the risks extend beyond the immediate breach. Individuals may suffer from identity theft, fraud, or exposure of sensitive health details, which could affect their personal and professional lives. For organizations, mishandling or failing to protect this data can lead to significant fines, lawsuits, and damage to reputation.
Key Risks of Inadequate Data Protection
- Identity Theft: Unauthorized access to personal details can result in individuals’ identities being stolen and misused.
- Financial Loss: Leaked financial information can lead to theft or fraudulent activity, costing both individuals and organizations.
- Legal Repercussions: Failing to protect patient information could result in legal action and hefty penalties.
- Reputation Damage: A breach of confidential data can severely damage the trust an organization has built with its clients and patients.
Therefore, it is crucial for organizations to implement robust data security measures to minimize the likelihood of such breaches and protect their clients’ sensitive information from harm.
How to Prepare for the Test
Preparing for an assessment on data protection standards requires a clear understanding of the regulations and how they apply in various scenarios. Success in this type of evaluation comes from both theoretical knowledge and practical application of the rules governing the security and confidentiality of sensitive information. Effective preparation involves studying key principles, recognizing common risks, and learning how to implement proper safeguards.
The first step in preparation is familiarizing yourself with the core concepts, including access control, data storage, and disposal protocols. It’s also important to understand the specific responsibilities individuals have in maintaining data integrity and privacy. Once these fundamental areas are understood, practicing with sample questions can help reinforce knowledge and build confidence for the assessment.
Additionally, reviewing case studies and real-life examples of data breaches can help highlight areas that need more attention. By focusing on both the theory and practical applications of data protection, individuals can ensure they are fully prepared to demonstrate their knowledge and compliance with the relevant regulations.
Critical HIPAA Privacy Violations Explained
Violations of data protection regulations can lead to significant consequences for both individuals and organizations. These breaches often involve unauthorized access, improper sharing, or mishandling of sensitive personal or health-related information. Understanding the most critical violations is essential for preventing them and ensuring compliance with legal and ethical standards.
Unauthorized Access: One of the most severe violations occurs when individuals access information they are not authorized to view. This could be intentional or accidental, but either way, it compromises the confidentiality of sensitive data. It is vital for organizations to establish clear access control policies and monitor user activity to prevent such breaches.
Improper Data Sharing: Another common violation involves the unauthorized sharing of confidential information, either internally or externally. This can happen when data is sent without proper encryption, or when it is disclosed to individuals who do not have a legitimate need to know. Such actions not only jeopardize the security of the information but also erode trust between patients and organizations.
Lack of Safeguards: Failing to implement adequate physical, technical, and administrative safeguards is a critical violation. These safeguards are necessary to protect data from unauthorized access, theft, or loss. Without proper security measures, even the most secure systems can be vulnerable to attacks or accidental breaches.
Inadequate Training: Employees who are not properly trained in data security best practices can unknowingly contribute to violations. Regular training is essential to ensure that all individuals understand the importance of protecting sensitive information and are aware of the potential consequences of mishandling it.
What to Expect in HIPAA Exams

When preparing for an evaluation on data protection standards, it’s important to understand what topics will be covered and the types of questions you may encounter. These assessments typically test knowledge of the rules and regulations that ensure sensitive information is handled securely and ethically. The goal is to assess your understanding of key concepts and how they apply to real-world situations.
The questions you’ll face will focus on a range of topics, including the principles of confidentiality, access control, data security measures, and the legal responsibilities of organizations and employees. Expect scenarios that require you to identify risks and implement proper safeguards to protect data from unauthorized access or misuse.
Multiple Choice Questions: These questions will assess your theoretical knowledge of the regulations, often requiring you to choose the best answer based on established guidelines. You may be asked to identify correct procedures, define terms, or describe responsibilities under the law.
Scenario-Based Questions: These questions simulate real-world situations, where you must apply your knowledge to solve problems. They test how well you can analyze a situation and make decisions that align with regulatory standards.
To succeed in these assessments, it is essential to be familiar with both the regulations themselves and the practical steps required to ensure compliance. Regular study, practical application, and understanding the consequences of non-compliance will help you perform well and demonstrate your readiness to safeguard sensitive data.
Top Resources for Test Preparation
Preparing for an evaluation on data protection standards requires access to comprehensive resources that cover the essential concepts and practical applications of the regulations. Whether you are a beginner or looking to refresh your knowledge, the right materials can make a significant difference in your readiness. Below are some of the best resources to help you prepare effectively.
Study Guides and Books
- Official Training Manuals: Many organizations offer official study guides and manuals, which provide a detailed overview of the key principles and regulations.
- Books by Experts: Books written by professionals in the field often break down complex concepts into easy-to-understand language, with practical examples and scenarios.
- Comprehensive Handbooks: Look for handbooks that outline policies, procedures, and real-world case studies to help solidify your understanding.
Online Courses and Webinars
- Online Training Platforms: Websites like Coursera, Udemy, or LinkedIn Learning offer specialized courses tailored to regulations and compliance topics, with interactive modules and quizzes.
- Live Webinars: Participating in live webinars hosted by experts in data protection can provide the opportunity to ask questions and gain deeper insights into specific topics.
- Recorded Lectures: Many institutions offer recorded lectures and tutorials that you can watch at your own pace, providing flexibility in your preparation.
Practice Quizzes and Mock Exams
- Sample Questions: Many websites and training programs provide sample questions that mimic the format and difficulty of actual assessments, helping you practice and identify areas for improvement.
- Mock Exams: Taking full-length practice exams under timed conditions can simulate the real testing experience and help you improve your test-taking skills.
- Review Platforms: Some platforms offer detailed explanations for answers, helping you understand why certain answers are correct or incorrect, which aids in long-term retention.
Using a combination of these resources will ensure a well-rounded and thorough preparation process, equipping you with the knowledge and confidence to succeed.
HIPAA Privacy Test Answer Tips
When preparing for an evaluation on data protection practices, it’s essential to adopt a strategic approach to answering questions effectively. Success is not just about memorizing facts; it’s about applying your knowledge to real-world scenarios. The following tips can help guide you through the process and ensure that you approach the evaluation with confidence and accuracy.
Understand the Key Concepts
Before attempting any questions, make sure you have a clear understanding of the core concepts. Familiarize yourself with the regulations surrounding data protection, access control, confidentiality, and the responsibilities of various parties. Understanding these foundational principles will help you quickly identify the correct answers when presented with specific situations.
Read Each Question Carefully
Pay close attention to the wording: Often, questions are designed to test your ability to interpret scenarios. Misreading a question can lead to incorrect responses. Ensure you understand the context and focus on keywords like “confidential,” “authorization,” and “safeguards” to guide your choice.
Eliminate Clearly Wrong Answers: If you’re unsure about a question, start by eliminating options that are clearly incorrect. This will increase your chances of selecting the right answer even if you’re uncertain.
Practice with Scenarios
Many questions will present realistic situations where you need to apply your knowledge. Practice by reviewing case studies or simulated situations where you need to identify the best course of action. This will help you improve your decision-making skills and prepare for scenario-based questions.
Review Regulations Regularly
Consistent review of the regulations and guidelines is essential to reinforce your understanding. Regularly revisiting key concepts will ensure they are fresh in your mind during the evaluation, allowing you to confidently answer questions when required.
By following these tips, you can approach the evaluation process with a solid foundation of knowledge and increase your chances of achieving a successful result.
Effective Study Strategies for HIPAA
When preparing for an evaluation on data protection regulations, developing a structured and effective study plan is crucial to mastering the material. Instead of simply reviewing content, focusing on understanding the core principles and applying them to real-world scenarios will help reinforce your knowledge. Below are some key strategies to maximize your study sessions and ensure you’re well-prepared.
Break Down the Material
Rather than trying to absorb everything at once, break the study material into smaller, manageable sections. Focus on one specific topic at a time, such as confidentiality requirements, data security measures, and the responsibilities of covered entities. This will allow you to focus your efforts and absorb information more effectively.
Utilize Practice Scenarios
One of the best ways to reinforce your understanding is by applying your knowledge to hypothetical situations. Practice scenarios help you understand how the rules apply in real-world settings, enhancing your ability to make informed decisions. This type of active learning will strengthen your problem-solving skills and improve retention.
Create Study Aids
Creating your own study aids can significantly improve memory retention. Consider making flashcards, summaries, or mind maps that highlight key concepts. Visual aids, such as diagrams or charts, can also help make complex material easier to understand and recall.
Set Regular Review Sessions
Consistent review is key to long-term retention. Schedule regular sessions to revisit the material, even after you feel confident in your understanding. This will help solidify the information in your memory and ensure you’re ready for the evaluation.
Join a Study Group
Studying with others can provide different perspectives on the material and help clarify any areas of confusion. Group study sessions also promote active discussion, which is a great way to reinforce concepts and test your knowledge.
By implementing these strategies into your study routine, you’ll be able to approach your preparation with confidence and achieve a deeper understanding of the material, ultimately enhancing your performance in the evaluation process.
Common Misconceptions About HIPAA
There are several myths surrounding the regulations that govern the protection of sensitive health information. These misconceptions can lead to confusion about compliance requirements, potentially resulting in unintentional violations. It’s important to clarify these misunderstandings to ensure proper handling of personal data and avoid legal complications. Below are some common misconceptions that often arise regarding these regulations.
Misconception 1: Only Healthcare Providers Need to Comply
One of the most prevalent misconceptions is that only healthcare providers need to follow these regulations. In reality, any organization that handles protected health information (PHI), including insurers, business associates, and even contractors, is required to comply with these rules. If your organization has access to health data, it is likely subject to the regulations, regardless of your direct involvement in patient care.
Misconception 2: All Health Data is Protected

Not all health-related data is covered by these protections. For instance, information that does not identify an individual, or is anonymized, is not subject to these rules. Understanding which data falls under protection is crucial for ensuring that only the appropriate data is safeguarded according to the regulations.
Misconception 3: Compliance is Only Necessary for Breaches
Many believe that these regulations are only relevant when a data breach occurs. However, compliance is required at all stages of data handling, from collection to storage and sharing. Proactive measures, such as training employees and implementing security protocols, are essential to prevent incidents before they occur.
Misconception 4: Regulations Only Apply to Electronic Health Records
While electronic records are certainly a focal point, these protections also apply to paper records, verbal communications, and other forms of data transmission. If health information is shared or stored in any format, it must be protected in accordance with the law.
Misconception 5: Compliance Is a One-Time Task
Compliance is not a one-time effort. Ongoing training, auditing, and updates to policies and procedures are necessary to ensure that organizations remain compliant as regulations evolve and new threats emerge. Regular review and adjustments are vital to maintaining a secure environment for sensitive data.
By addressing these misconceptions and understanding the true scope of the rules, organizations can better protect sensitive information and ensure they meet the required standards for security and confidentiality.
Key Regulations in Privacy and Security
In order to safeguard sensitive health data, certain standards and rules are put in place to protect both the confidentiality and the integrity of this information. These regulations are designed to ensure that health information is handled securely and appropriately throughout its lifecycle. Below, we will explore the key provisions that outline how organizations must approach the protection of data.
Confidentiality and Access Control
One of the most critical aspects of data protection is controlling who has access to sensitive information. The regulations set clear guidelines for who may view or receive personal health details. Access is typically granted based on necessity and role, ensuring that only authorized personnel can handle protected data. Unauthorized access, whether accidental or intentional, can lead to severe penalties. Strong access controls and authentication procedures are vital to maintain confidentiality.
Data Security and Encryption

Data security is a cornerstone of these regulations. Organizations must implement robust measures to protect health data from unauthorized access, alteration, or destruction. Encryption, both for data at rest and in transit, is required to safeguard sensitive information. This ensures that even if the data is intercepted or compromised, it remains unreadable and unusable. Regular security assessments and updates to systems help mitigate emerging threats and vulnerabilities.
Incident Response and Reporting
In the event of a data breach or security incident, there are strict requirements for how such events should be handled. Organizations are required to notify affected individuals promptly, outlining the nature of the breach and the steps taken to remedy the situation. Reporting breaches to the appropriate authorities within a set time frame is also necessary to ensure transparency and compliance. Timely and thorough responses help to minimize the damage and prevent further incidents.
Training and Awareness Programs
Continuous training and education are necessary to ensure that all employees understand their responsibilities regarding data protection. Regular training programs should cover key regulations, the proper handling of sensitive information, and how to recognize potential security threats. By maintaining a workforce that is well-versed in the latest security protocols, organizations can better prevent breaches and ensure compliance.
By adhering to these key regulations, organizations can safeguard sensitive health information, foster trust with patients, and maintain a secure and compliant environment for handling confidential data.
Test Answer Review Process
After completing an assessment related to compliance with data protection standards, it is essential to review the responses to ensure accuracy and a deep understanding of the material. This process not only helps verify knowledge but also identifies areas that may need further study. A comprehensive review provides valuable feedback, enhancing one’s grasp of important concepts and regulatory requirements.
Step 1: Identifying Correct Responses
In this initial phase, the focus is on confirming that the provided answers align with the best practices and official standards set forth by governing authorities. Each question should be carefully compared with the regulations to ensure consistency. Correct responses will demonstrate a solid understanding of key principles such as data security, confidentiality, and breach notification protocols.
Step 2: Analyzing Incorrect Responses
If certain responses are incorrect, it’s crucial to analyze why they were chosen. Were there misunderstandings of the guidelines? Were any critical aspects of the regulations overlooked? This step helps clarify any confusion and allows the participant to correct misconceptions. It’s an opportunity to refine knowledge and ensure that all areas are fully understood before applying the concepts in real-world scenarios.
Step 3: Reviewing Feedback and Resources
Most assessments will include feedback or reference materials to help participants understand why certain answers are correct or incorrect. Reviewing this feedback is key to improving comprehension. Additionally, supplementary resources, such as case studies or updated documentation, can further strengthen the participant’s ability to apply the knowledge effectively. This ongoing learning process is essential for staying current with changing regulations and best practices in the field.
Step 4: Continuous Improvement
The review process is not just about identifying mistakes but also about improving overall understanding and performance. It is important to continue practicing and reinforcing the learned concepts to ensure long-term retention. By actively engaging with the material and seeking clarification on any uncertainties, individuals can develop a deeper proficiency in handling sensitive information and maintaining compliance with legal and ethical standards.
Ultimately, the test review process is an invaluable tool in achieving mastery of compliance regulations, helping individuals become more effective in their roles and confident in their ability to uphold security and confidentiality standards.
Challenges in Passing the Compliance Exam
Achieving success in assessments related to regulatory compliance can be a challenging endeavor, particularly when it comes to understanding complex rules and the nuances of legal requirements. Many individuals face difficulties not only in memorizing facts but also in applying them accurately to real-world scenarios. This section explores some of the key challenges that often arise during such evaluations and offers insights on how to overcome them.
Complexity of Regulatory Guidelines
One of the most significant challenges is the complexity of the rules and guidelines that must be understood and adhered to. Regulations related to data security and patient confidentiality can be intricate and detailed, requiring individuals to absorb a vast amount of information. In some cases, the phrasing of these regulations can be difficult to interpret, leading to confusion and errors during assessments.
Practical Application of Knowledge
Another common hurdle is the ability to apply theoretical knowledge to practical situations. Many exams are designed to test not just recall but also the capacity to understand and apply principles in various contexts. The transition from abstract knowledge to practical application can be a significant challenge, especially for those who have not had hands-on experience in compliance-related roles.
Table: Common Areas of Difficulty
| Challenge | Description | Possible Solutions |
|---|---|---|
| Understanding Regulations | Regulations may be difficult to interpret and remember due to their technical nature. | Break down key concepts into simpler terms, use visual aids, and practice with scenarios. |
| Application to Real Scenarios | Difficulty in relating abstract concepts to real-world situations. | Use case studies, practice exercises, and role-playing to enhance understanding. |
| Time Management | Exams often come with time constraints, adding pressure to the process. | Develop time management skills by taking timed practice exams. |
| Retention of Information | Difficulty in retaining vast amounts of information over time. | Reinforce learning through regular review, flashcards, and spaced repetition techniques. |
In conclusion, passing an exam related to regulatory compliance requires more than just memorization. It demands a deep understanding of complex rules, the ability to apply them effectively in various contexts, and strong time-management and study skills. By recognizing and addressing these challenges, candidates can improve their chances of success and ensure they are well-prepared for their roles in maintaining security and confidentiality standards.
Practical Applications of Compliance Knowledge
Understanding the regulations surrounding data protection and confidentiality is not just an academic exercise–it’s essential for ensuring the security of sensitive information in a variety of professional environments. Knowledge of these regulations has far-reaching applications in day-to-day operations, impacting everything from patient care to organizational policies. In this section, we will explore how this knowledge is put into practice and why it is crucial for maintaining ethical standards and legal compliance in healthcare and related fields.
Ensuring Data Security in Healthcare
One of the primary applications of regulatory knowledge is ensuring the security of confidential patient information. Healthcare professionals must be well-versed in the principles of data protection to safeguard against unauthorized access or breaches. This includes:
- Proper handling of electronic health records (EHRs)
- Enforcing strong password policies and encryption protocols
- Monitoring access to sensitive data to prevent unauthorized use
- Training staff to recognize potential security threats, such as phishing attacks or data theft
Improving Organizational Compliance
Beyond individual knowledge, understanding regulations plays a critical role in shaping organizational policies and procedures. Compliance teams within healthcare organizations and related fields are responsible for ensuring that all employees adhere to strict data protection standards. This can involve:
- Developing internal audit procedures to assess data security measures
- Establishing training programs to keep staff updated on new regulations
- Creating incident response protocols to handle potential breaches effectively
- Documenting and reporting compliance efforts for regulatory bodies
Fostering Trust with Patients and Clients
Beyond legal and operational aspects, applying knowledge of these regulations fosters trust with patients and clients. When individuals know their sensitive information is being handled securely, it increases their confidence in healthcare providers and organizations. By maintaining compliance, professionals can:
- Enhance patient trust in the safety of their personal data
- Improve client relationships by demonstrating a commitment to confidentiality
- Minimize the risk of legal liabilities and financial penalties
Ultimately, applying regulatory knowledge ensures a healthcare environment where privacy is protected, security is prioritized, and ethical standards are upheld. These practical applications are essential for building a compliant, trustworthy, and secure system for handling sensitive information.