Packet Tracer 7.4.1.2 Answers Complete Guide
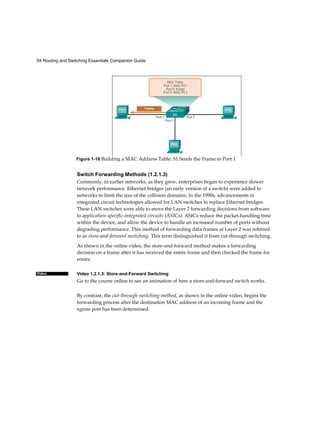
In the world of network configuration and troubleshooting, simulation tools play a vital role in helping users practice and master complex concepts. These tools allow individuals to design and test various network setups without needing physical hardware, making the learning process more accessible and efficient. The ability to simulate real-world networking scenarios can significantly enhance one’s technical skills, especially for those preparing for certifications or looking to deepen their understanding of networking principles.
Working through structured tasks in these environments provides hands-on experience that is invaluable for solving real-life issues. Each task presents unique challenges that require careful thought and a systematic approach to achieve the desired results. Whether it involves configuring devices, optimizing network performance, or troubleshooting connectivity issues, these exercises offer practical insights into how networks operate and how to resolve common problems.
Mastering the fundamentals of network configurations, addressing common pitfalls, and testing solutions through simulated environments are key to building a solid foundation in networking. This approach not only strengthens technical expertise but also builds confidence in tackling more advanced network scenarios in the future.
Packet Tracer 7.4.1.2 Answers Overview
This section provides a comprehensive overview of solutions for a specific set of networking exercises within a simulation environment. The goal is to guide users through the necessary steps to complete network configurations successfully. Each task in this series is designed to reinforce key networking concepts and help users develop troubleshooting skills.
By working through these tasks, individuals can gain a better understanding of the relationships between different network devices, protocols, and configurations. These exercises require attention to detail, a structured approach, and a good grasp of fundamental networking principles. As users progress, they will encounter increasingly complex scenarios that test their ability to solve real-world networking problems effectively.
The solutions provided here aim to break down each challenge step by step, making it easier to follow along and apply the correct configurations. Whether you are just starting or looking to refine your skills, this guide will help ensure that you understand the core concepts and methods for completing the tasks successfully.
Understanding the Task Requirements
Before diving into any network configuration task, it’s essential to fully understand the objectives and specific instructions outlined in the assignment. Each exercise typically comes with a set of goals that must be achieved by applying various network design principles and troubleshooting methods. These goals may range from setting up basic device configurations to more complex tasks involving routing and security protocols.
Identifying Key Objectives
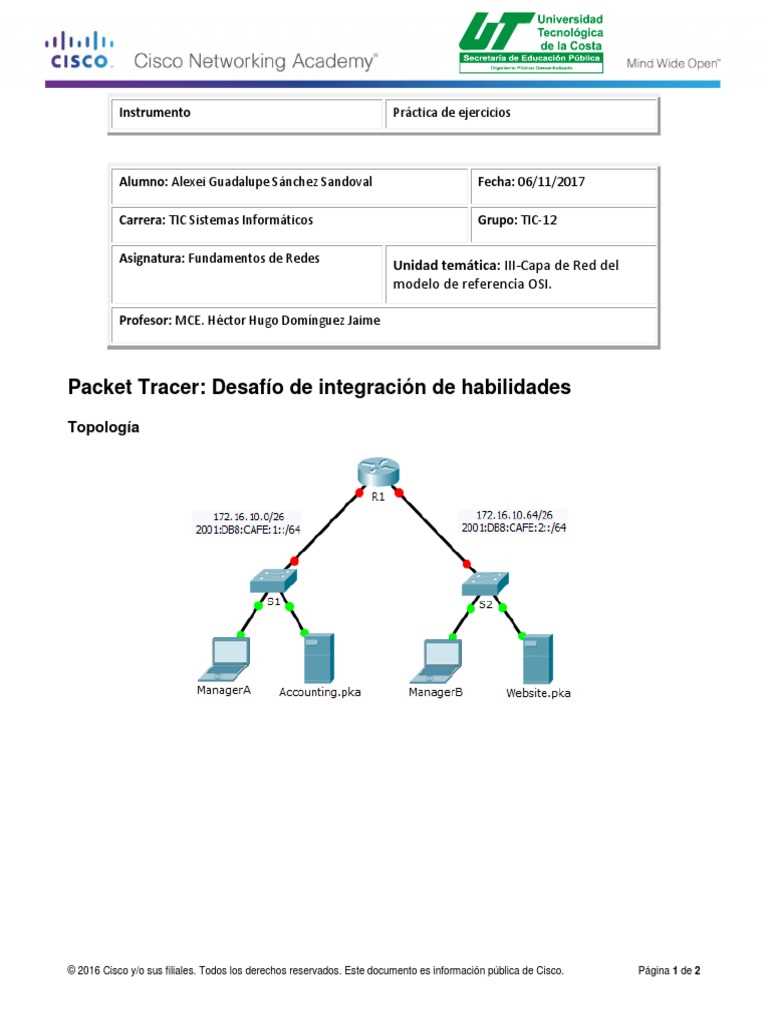
Each task will have certain requirements that must be met, such as configuring routers, switches, or other network devices to communicate properly. Understanding what each device needs and how they should interact with one another is crucial for completing the task correctly. Pay close attention to any details regarding IP addresses, subnetting, routing protocols, and security settings, as these often play a key role in determining the success of the configuration.
Evaluating the Network Setup
Once the objectives are clear, the next step is to analyze the network setup and identify any potential challenges. This could involve troubleshooting connectivity issues, verifying device configurations, or ensuring that the correct routing paths are in place. Properly assessing the initial setup will give you the necessary insights to approach the task systematically and efficiently, helping you achieve the desired outcome with minimal complications.
How to Approach Network Simulations
Approaching network simulations requires a structured and methodical mindset. These exercises are designed to replicate real-world scenarios, allowing you to experiment with configurations, troubleshoot issues, and test your networking knowledge without the need for physical hardware. A systematic approach ensures you address all key components and complete the tasks successfully, avoiding common mistakes that can hinder progress.
Step-by-Step Strategy
The best way to tackle these tasks is to break them down into manageable steps. Follow a logical progression to ensure nothing is overlooked. Here’s a recommended approach:
- Read the instructions carefully: Understand the goals and requirements of the task before making any changes.
- Plan your network: Map out the devices, connections, and configurations you’ll need to implement.
- Configure devices: Start with basic settings like IP addresses and device names, then move on to more complex protocols.
- Test the setup: Verify that everything is working as expected, checking for connectivity issues or misconfigurations.
- Troubleshoot: If something isn’t functioning properly, identify the issue and adjust settings accordingly.
Common Approaches for Troubleshooting
When troubleshooting network simulations, it’s important to stay organized and methodical. Use these steps to resolve issues:
- Check physical connections: Ensure that all devices are properly connected.
- Verify IP addresses: Double-check that all devices have the correct network settings.
- Review routing tables: Confirm that routing protocols are correctly configured and that paths are functioning as expected.
- Test connectivity: Use commands like “ping” or “traceroute” to check if devices are communicating correctly.
By following a clear strategy and troubleshooting method, you can successfully navigate any network simulation and gain valuable hands-on experience.
Key Concepts in Network Simulation
Understanding the core principles of network simulation is essential for successfully completing configuration tasks and troubleshooting common issues. These simulations are built on fundamental networking concepts that allow users to experiment with configurations, connections, and protocols in a controlled virtual environment. Mastering these concepts helps streamline the process and ensures a solid foundation in networking.
Core Networking Principles
Before diving into the simulation tasks, it’s important to grasp the key principles that form the basis of networking. Some of the most important concepts include:
- IP Addressing: Properly assigning IP addresses to devices is essential for enabling communication within a network.
- Subnetting: Understanding how to divide a network into smaller, manageable subnets helps in optimizing performance and security.
- Routing Protocols: Configuring routing protocols like RIP, OSPF, or EIGRP ensures efficient data packet delivery across devices.
- Switching: Proper configuration of switches allows devices on the same network to communicate and ensures efficient data traffic flow.
Simulation Tools and Features
Network simulations provide a variety of tools and features to simplify the configuration and testing process. Familiarizing yourself with these tools is crucial for success:
- Device Configuration: Configuring routers, switches, and other network devices is done through an intuitive interface, where users can set parameters like IP addresses and routing protocols.
- Simulation Mode: This mode allows you to step through network activities, observing the behavior of data as it moves through the network.
- Command-Line Interface (CLI): Many devices are configured through the CLI, providing a more advanced way to control network operations.
- Real-time and Simulation Views: These views allow users to observe the network’s behavior in real time or step through events to better understand packet flow and configurations.
Mastering these core concepts and tools is critical to successfully completing network simulations and configuring devices to work seamlessly in a real-world environment.
Step-by-Step Guide to Completing Tasks
Successfully completing network configuration tasks requires a structured approach, where each step is carefully executed to meet the desired outcome. Following a step-by-step method ensures that you address every aspect of the task, from initial setup to final verification, without missing crucial details. This guide will walk you through the process, making it easier to achieve the correct configuration and troubleshoot any issues along the way.
Start by reviewing the instructions thoroughly to understand what the task requires. This helps set a clear direction for your work. Once you know the objectives, proceed with the following steps to configure the network efficiently:
- Analyze the Network Requirements: Begin by reading through the task description to identify the devices, configurations, and goals required. Determine the network topology and what each device will do.
- Set Up Devices: Start by adding routers, switches, and other network devices to the workspace. Configure basic settings such as device names and IP addresses for each device.
- Configure Routing and Switching: Set up routing protocols (e.g., RIP, OSPF) or static routes, depending on the task requirements. Make sure that switches are properly configured for device communication.
- Implement Security Features: Apply security protocols such as access control lists (ACLs), VLANs, or port security to ensure a safe network environment.
- Verify the Configuration: Once all devices are configured, check for connectivity using ping tests, checking routing tables, and ensuring all devices can communicate properly.
- Troubleshoot Issues: If any part of the network isn’t functioning as expected, identify and resolve problems by reviewing configurations, checking device connections, and verifying IP settings.
- Test the Network: Run tests to ensure that the network is working as planned. This includes testing specific features like routing, DNS, or DHCP, depending on the task.
By following this methodical approach, you will be able to configure networks with precision and confidence. Each step builds upon the last, ensuring that the final setup meets the requirements and operates as expected.
Common Challenges in Network Simulations
During the process of simulating network environments, several issues can arise that hinder smooth operation and accurate results. These challenges often stem from improper configurations, network topology errors, or misunderstandings of how certain network components interact. Identifying and resolving these problems effectively is key to achieving success in network testing and configuration.
The table below outlines some common obstacles encountered during simulations, along with practical solutions for troubleshooting and resolving these issues:
| Challenge | Description | Solution |
|---|---|---|
| Incorrect Device Configuration | Devices may fail to communicate or malfunction if their settings, such as IP addresses or subnet masks, are configured incorrectly. | Ensure that all device configurations are accurate, including IP settings, interfaces, and routing protocols. |
| Connection Failures | Network devices may not connect due to issues like disabled interfaces or faulty cables. | Check all physical connections, ensure interfaces are enabled, and verify cable integrity. |
| Routing Problems | Improper routing configurations can prevent data from reaching its destination across the network. | Review routing tables, confirm routing protocols are functioning correctly, and ensure routes are being properly advertised. |
| VLAN Misconfigurations | Devices in different VLANs might be unable to communicate if VLAN settings are incorrectly applied. | Verify VLAN configurations, ensure correct trunking, and confirm that VLANs are properly assigned to ports. |
| Access Control List (ACL) Issues | Improper ACL rules can block legitimate traffic or allow unauthorized access, causing security or connectivity issues. | Carefully review ACL settings to ensure they permit the correct types of traffic while maintaining security restrictions. |
By recognizing these common challenges and applying the appropriate solutions, users can troubleshoot effectively, ensuring their simulations are accurate and their network configurations function as intended.
Troubleshooting Tips for Success
When working with network simulations, troubleshooting is a vital skill that helps to quickly identify and resolve issues. The process involves systematically narrowing down the possible causes of a problem and applying effective solutions to ensure the network functions as intended. Here are some valuable tips to follow when faced with challenges during simulations:
- Start with the Basics: Always begin by verifying the fundamental settings such as device configurations, IP addresses, and interface statuses. A simple mistake in these areas can often be the root cause of more complex issues.
- Check Connectivity: Test connections between devices to identify where communication breaks down. Use basic tools like ping or traceroute to determine which devices are reachable and where the issue lies.
- Review Routing Tables: Make sure routing tables are populated correctly and that devices know the best paths to reach one another. Misconfigured routes or missing routes can cause packets to fail to reach their destination.
- Inspect VLAN Configurations: If devices are unable to communicate across VLANs, review VLAN settings and ensure that proper trunking and VLAN assignments are made.
- Examine Access Control Lists (ACLs): If there is restricted traffic flow, double-check ACL configurations to confirm that they are not unintentionally blocking essential traffic.
By applying these troubleshooting tips, users can efficiently diagnose and fix problems, ensuring smooth operation and successful simulation outcomes. These methods not only help resolve issues quickly but also improve overall network understanding and skills.
Useful Tools for Task Completion
Completing tasks in network simulations requires not only a good understanding of concepts but also effective tools that can aid in both configuration and troubleshooting. These tools simplify the process, making it easier to identify issues, verify settings, and optimize network performance. Here are some of the most useful tools available for completing tasks in network environments:
- Ping: A simple yet powerful tool to test connectivity between devices. It helps verify that a device is reachable on the network and can pinpoint potential connectivity issues.
- Traceroute: This tool is used to trace the path packets take from one device to another. It helps identify where delays or packet losses are occurring along the route.
- IP Configuration: Reviewing the IP configurations of devices is crucial in ensuring that all settings, including IP addresses, subnet masks, and gateways, are correctly configured for proper communication.
- Topology View: A visual representation of the network layout that helps to quickly identify how devices are connected and where any physical or logical issues may arise.
- Device Simulation: Using simulation modes to test the behavior of devices under different conditions can help anticipate issues and fine-tune settings before implementing them in real-world environments.
- Routing Tables: These tables display the paths that devices will take to reach different networks. Reviewing routing tables ensures that correct routes are being used and helps troubleshoot routing issues.
- Access Control Lists (ACLs): When managing traffic flow and security, ACLs provide detailed access control configurations that can help prevent unauthorized access and allow desired traffic.
By effectively using these tools, users can streamline the task completion process, quickly identify problems, and ensure that the network environment is functioning optimally. These tools not only aid in completing tasks but also enhance learning by providing deeper insights into network behavior.
How to Verify Your Configuration
Once you’ve configured your network devices, it’s essential to verify that everything is set up correctly and functioning as expected. Verification ensures that the network configuration is accurate, allowing devices to communicate and perform tasks without errors. It helps identify any misconfigurations or issues that may be causing connectivity problems. Here are several steps you can take to verify your setup:
Step 1: Check IP Addresses and Subnets
Ensure that each device has the correct IP address, subnet mask, and gateway. Incorrect IP configurations are a common cause of connectivity issues. You can use the “show ip interface brief” command on routers or switches to check the status and configuration of interfaces. Verify that each device is in the correct network and has a valid subnet mask.
Step 2: Test Connectivity
Ping is an essential tool for verifying network connectivity. Test the ability of devices to reach each other by using the “ping” command. Start by pinging the local router or switch and then expand the tests to other devices in the network. Successful pings confirm that the devices are able to communicate over the network. If there are failures, it indicates a potential issue with the configuration or network setup.
Step 3: Verify Routing and Access Control
Check routing tables to ensure that correct routes are set up between devices, particularly when dealing with multiple networks. Use the “show ip route” command on routers to review the routing table and verify that routes to all required destinations exist. Also, check any access control lists (ACLs) that may be applied to verify that traffic is being allowed or blocked as intended.
By carefully following these steps, you can confirm that your configuration is correct and troubleshoot any issues before they become larger problems. Regular verification also ensures the network remains secure and optimized for performance.
Testing Network Connectivity Efficiently
Testing network connectivity is a critical step in ensuring that devices within a network can communicate properly and that the infrastructure is functioning as intended. Efficient testing allows for quick identification of issues, saving time and resources in troubleshooting. There are several tools and techniques that can be used to verify connectivity, identify problems, and ensure smooth network operation. Here are the most effective methods to test network connectivity:
Ping Tests for Basic Connectivity
One of the simplest and most widely used methods to test connectivity is the ping command. By sending packets to a specific IP address, the ping command verifies if a device is reachable over the network. A successful reply confirms that the device is online and the basic network path is functional. If the ping fails, it indicates a connectivity issue that requires further investigation.
Traceroute for Path Analysis
When troubleshooting connectivity issues, especially those related to slow or intermittent connections, the traceroute command is invaluable. It provides a path analysis by showing the route taken by packets from the source device to the destination. Traceroute can help pinpoint where packets are being delayed or dropped, which is essential for identifying bottlenecks or misconfigurations in the network.
Using Telnet and SSH for Remote Access Verification
For remote device management, using Telnet or SSH can verify if devices are accessible from remote locations. These tools test whether the remote management ports are open and whether access is possible. Successful connections via these protocols ensure that network devices can be managed remotely and are responsive to configuration changes.
Checking Interface Status and Configuration
Another efficient way to test network connectivity is by checking the status and configuration of interfaces on network devices. Using commands like “show ip interface brief” or “show interface” on routers and switches can provide insights into the health of the interfaces. These commands indicate whether the interfaces are administratively up or down and can reveal errors or misconfigurations that might affect connectivity.
Bandwidth and Latency Testing
Bandwidth and latency are two key factors that impact network performance. Tools such as speed tests and latency measuring tools allow network engineers to test the maximum throughput and delay between devices. Regular tests of these metrics ensure that the network is performing optimally and that there are no underlying issues affecting performance.
By leveraging these efficient testing methods, you can quickly diagnose and resolve connectivity issues, ensuring that the network remains operational and optimized for performance. Regular testing is an essential part of network management and can help prevent minor issues from escalating into major disruptions.
Setting Up Routers and Switches
Configuring routers and switches is a fundamental task in building and managing a network. Proper setup ensures that data can be efficiently routed between devices, and that communication across different segments of the network remains smooth. Whether you’re setting up basic configurations or advanced network features, the process generally involves configuring interfaces, IP addresses, routing protocols, and security settings.
Initial Configuration of Routers
When setting up a router, the first step is to perform a basic configuration to enable communication with other devices in the network. This includes assigning IP addresses to the interfaces, enabling routing protocols, and securing access to the device.
- Assign IP Addresses: Each interface on the router should be assigned a unique IP address that corresponds to the network segment it connects to. This is necessary for routing packets between different network segments.
- Enable Routing: Enable dynamic or static routing protocols to ensure that the router can forward data to the appropriate destination. Common routing protocols include OSPF, EIGRP, and RIP.
- Secure Device Access: Set up passwords for console, VTY, and enable mode to protect the device from unauthorized access.
- Configure NAT (Network Address Translation): If the router connects a private network to the internet, configure NAT to translate private IP addresses into public ones for internet access.
Configuring Switches for Network Segmentation
Switches operate at the data link layer and are used to segment networks into smaller collision domains. Proper configuration of switches ensures efficient data forwarding within the same network segment and proper VLAN segmentation.
- Set Up VLANs: Virtual Local Area Networks (VLANs) are used to segment a network into different logical groups. Configure VLANs on a switch to keep traffic within specific groups.
- Enable Trunking: If connecting multiple switches, configure trunk links to allow VLAN traffic to pass between switches. The trunking protocol (such as IEEE 802.1Q) ensures proper VLAN tagging.
- Configure Spanning Tree Protocol (STP): Enable STP to prevent network loops in a switched environment. This protocol ensures redundancy while avoiding broadcast storms.
- Set Up Port Security: Secure switch ports by limiting access to specific devices based on MAC addresses. This helps prevent unauthorized devices from connecting to the network.
Once both routers and switches are properly configured, ensure that they are connected correctly and verify that the network is functioning as expected by testing connectivity between devices. Regular updates and security configurations will also help maintain the network’s integrity and performance.
Understanding IP Addressing and Subnetting
IP addressing and subnetting are key concepts in networking that enable devices to communicate over a network. Properly configuring IP addresses ensures that data can reach its intended destination, while subnetting divides a network into smaller, more manageable segments, improving performance and security. A solid understanding of these principles is essential for network design, troubleshooting, and optimizing network traffic.
IP Addressing Basics
Each device on a network is assigned a unique identifier known as an IP address. This address serves as a label that allows the device to send and receive data within the network. An IP address is made up of two main components: the network portion and the host portion. The network portion identifies the network the device belongs to, while the host portion identifies the specific device within that network.
- IPv4 vs IPv6: There are two types of IP addresses: IPv4 (Internet Protocol version 4) and IPv6 (Internet Protocol version 6). IPv4 addresses are 32-bit, while IPv6 addresses are 128-bit, providing a much larger address space.
- Classful Addressing: In classful addressing, IP addresses are divided into five classes (A, B, C, D, E). Classes A, B, and C are used for unicast communication, while D and E are reserved for multicast and experimental purposes.
- Private vs Public Addresses: Public IP addresses are globally routable and used across the internet, while private IP addresses are used within local networks and are not routable on the internet.
Subnetting Explained
Subnetting is the practice of dividing a larger network into smaller subnetworks, or subnets. This allows for more efficient use of IP addresses and improves network performance by limiting the scope of broadcast traffic. Subnetting also helps enhance security by isolating different network segments.
- Subnet Masks: A subnet mask is used to determine the network and host portions of an IP address. It is paired with the IP address to enable routing between different subnets.
- CIDR Notation: Classless Inter-Domain Routing (CIDR) notation is a more flexible way of representing subnet masks. It is written as an IP address followed by a slash and the number of bits in the network portion (e.g., 192.168.1.0/24).
- Subnetting Formula: To calculate the number of subnets or hosts per subnet, you need to determine how many bits are borrowed from the host portion of the IP address to create additional subnets.
Mastering IP addressing and subnetting will significantly enhance your ability to design and manage efficient, secure networks. With these skills, network engineers can create optimized IP schemes, troubleshoot network connectivity issues, and ensure that data flows smoothly across network boundaries.
Configuring Routing Protocols in Network Simulations
Routing protocols are essential for enabling communication between different networks in a simulated environment. They allow routers to share information about network topology, ensuring data packets are directed to their correct destinations. Configuring routing protocols correctly is crucial for creating efficient and scalable networks. This section covers the basics of setting up routing protocols, such as RIP, OSPF, and EIGRP, in network simulations.
Understanding Routing Protocols
Routing protocols determine how routers discover and maintain routes to other networks. They help routers communicate with each other, ensuring that the best path is selected for data transmission. Each routing protocol uses different algorithms and metrics to evaluate and choose routes. The choice of protocol depends on network size, speed requirements, and network topology.
- RIP (Routing Information Protocol): A distance-vector protocol that uses hop count as its metric. It is simple to configure and suitable for small networks but lacks scalability and efficiency in larger environments.
- OSPF (Open Shortest Path First): A link-state protocol that provides faster convergence and better scalability. OSPF is ideal for larger networks and supports hierarchical routing with areas to optimize performance.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid protocol that combines the benefits of both distance-vector and link-state protocols. EIGRP provides faster convergence and more efficient use of bandwidth.
Configuring Routing Protocols
To configure routing protocols, network devices must be properly set up with appropriate commands. Here’s an overview of how to configure RIP, OSPF, and EIGRP on routers in a network simulation environment:
- RIP Configuration:
- Enable RIP by entering router configuration mode.
- Use the command
router ripto start the RIP process. - Specify the networks to be advertised with the
network [network address]command. - Verify the configuration using
show ip routeto check routing tables.
- OSPF Configuration:
- Enter router configuration mode and use the command
router ospf [process ID]. - Define the OSPF network using the
network [network address] [wildcard mask] area [area ID]command. - Verify OSPF operation with
show ip ospf neighbor.
- Enter router configuration mode and use the command
- EIGRP Configuration:
- Activate EIGRP by entering
router eigrp [AS number]. - Advertise networks with the
network [network address]command. - Check EIGRP status using
show ip eigrp neighbors.
- Activate EIGRP by entering
Once the routing protocols are configured, it’s essential to monitor and troubleshoot the network to ensure proper data routing and convergence. Proper configuration helps maintain optimal network performance and reliability across different segments of the network.
How to Secure Your Network
Securing a network is essential to protect it from unauthorized access, data breaches, and other cyber threats. A well-secured network ensures the integrity, confidentiality, and availability of data, allowing smooth communication and operations without the risk of external attacks. This section provides guidelines on how to effectively secure your network infrastructure and safeguard it from potential vulnerabilities.
The security of a network involves several layers of defense, each targeting different aspects of potential risks. From configuring devices to monitoring traffic, each step plays a crucial role in maintaining a robust security posture. Below are some fundamental strategies and techniques to secure your network:
1. Implement Strong Access Control
Access control is vital for ensuring that only authorized individuals or devices can access your network. This can be achieved through:
- Password Management: Use complex, unique passwords for each device and service. Implement multi-factor authentication where possible to enhance security.
- Role-based Access: Restrict access to sensitive information based on the user’s role in the organization.
- Network Segmentation: Divide your network into segments to limit access to critical resources and reduce potential attack surfaces.
2. Keep Software and Firmware Updated
Regularly update the software and firmware of network devices, servers, and endpoints. This ensures that the latest security patches are applied, reducing the risk of exploitation by attackers using known vulnerabilities.
- Automated Updates: Where possible, enable automatic updates to ensure that patches are applied without delay.
- Vulnerability Scanning: Use tools to regularly scan your network for vulnerabilities and apply fixes promptly.
3. Utilize Firewalls and Intrusion Detection Systems
Firewalls act as a barrier between trusted and untrusted networks, filtering traffic based on security rules. Intrusion Detection Systems (IDS) help monitor network traffic for unusual activity and potential threats. Together, these tools enhance network security by:
- Traffic Filtering: Blocking harmful or unauthorized traffic before it can access your network.
- Real-time Alerts: Notifying administrators of any suspicious activity that may indicate an attack or breach.
4. Encrypt Sensitive Data
Encryption ensures that sensitive data is unreadable to unauthorized users. This is particularly important for data transmitted over public or unsecured networks. Implement encryption protocols such as:
- SSL/TLS: Use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols for encrypting web traffic.
- IPSec: Use Internet Protocol Security (IPSec) to encrypt data at the network layer, ensuring private communication over unsecured channels.
5. Regularly Monitor Network Activity
Continuous monitoring of your network is essential for detecting any suspicious activity or potential breaches. Use network monitoring tools to track traffic patterns, device health, and security logs. This helps identify vulnerabilities early and take action before any damage occurs.
- Network Monitoring Tools: Use tools like Wireshark or Nagios to analyze traffic and monitor network performance.
- Log Management: Regularly review logs from routers, firewalls, and other devices to detect any anomalies or unauthorized access attempts.
By following these guidelines and implementing a multi-layered security strategy, you can significantly reduce the risk of network breaches and maintain the integrity of your network. Security is an ongoing process, and staying proactive is key to safeguarding your network from evolving threats.
Improving Network Performance in Simulations
Optimizing network performance during simulations is essential for creating efficient, realistic models that accurately reflect real-world conditions. By addressing key factors that influence speed, stability, and resource utilization, you can enhance the performance of your network setup and improve the results of your simulations. This section highlights strategies for optimizing network performance in a virtual environment.
Network simulations often involve multiple devices and configurations, which can lead to issues such as latency, packet loss, and resource contention. To overcome these challenges and ensure smooth operation, you can adopt several practices aimed at improving both the speed and accuracy of the simulation. Below are some key strategies to consider:
1. Optimize Device Configurations
Ensuring that each network device is configured efficiently can greatly improve the overall performance of the simulation. Consider the following steps:
- Disable Unnecessary Features: Turn off features or services that are not required for the specific simulation, such as unused interfaces or protocols.
- Minimize Device Complexity: Use simpler configurations where possible to reduce processing overhead. Avoid overcomplicating the network setup unless necessary.
- Adjust Device Resources: Increase the allocated resources (e.g., RAM, CPU) for virtualized devices to improve their responsiveness during the simulation.
2. Efficiently Manage Network Traffic
Excessive traffic or poorly optimized routing can hinder simulation performance. To avoid congestion and improve throughput, try these tips:
- Use Static Routes: When applicable, use static routing instead of dynamic protocols to reduce the amount of processing required to determine the best path.
- Limit Broadcast Traffic: Minimize the use of broadcast-based communication and reduce unnecessary multicast traffic, which can consume resources.
- Implement Quality of Service (QoS): Use QoS settings to prioritize critical traffic and reduce the impact of non-essential communications.
3. Monitor and Analyze Performance
Continuous monitoring of network performance allows you to identify bottlenecks and areas for improvement. Use performance analysis tools to gather insights into simulation behavior:
- Utilize Built-in Monitoring Tools: Many simulation platforms offer performance monitoring features, such as bandwidth usage graphs and packet loss statistics, to help identify issues.
- Analyze Network Traffic: Use network analysis tools to monitor traffic patterns and detect abnormal spikes or congestion points that could impact simulation performance.
- Adjust Simulation Settings: Reduce the complexity of simulations by adjusting parameters such as the number of devices or traffic load to make the process more manageable.
4. Optimize Simulation Hardware
The hardware on which the simulation is run can significantly affect performance. Ensure that your system is capable of handling the demands of your network model:
- Increase RAM and CPU Power: More memory and processing power can improve the performance of larger or more complex simulations.
- Use SSDs for Faster Load Times: If running simulations from a hard drive, consider switching to a solid-state drive (SSD) to speed up loading and simulation processing times.
- Adjust Virtual Machine Settings: If using virtual environments, adjust the settings to allocate more resources to the simulation environment for optimal performance.
5. Simplify Network Topology
While detailed and complex network designs can provide more realistic simulations, they can also introduce performance challenges. To streamline the simulation:
- Limit the Number of Devices: Reducing the number of devices in the network can help improve simulation speed and reduce processing requirements.
- Consolidate Network Layers: Simplify the network topology by consolidating switches, routers, and other devices where possible to minimize the complexity of the design.
- Reduce the Distance Between Devices: Virtual devices that are closer together tend to have faster response times, so reduce unnecessary distance in network layouts.
By applying these strategies, you can significantly improve the performance of your network simulations, making them more efficient and effective for testing and analysis. These steps ensure that your network models function optimally and reflect realistic behaviors, helping you achieve better results in less time.
Advanced Techniques for Network Simulation
In network simulation, applying advanced techniques is essential for creating sophisticated, high-performance systems that mimic real-world environments. These methods help in configuring complex setups, optimizing performance, and diagnosing network issues more efficiently. By mastering these strategies, network professionals can improve network reliability, scalability, and manageability in their simulations.
1. Configuring Advanced Routing Protocols
Routing protocols play a crucial role in directing data traffic across the network. Advanced configurations allow for better management of network traffic, reducing congestion and improving response times. Key protocols such as OSPF, EIGRP, and BGP each offer distinct advantages depending on the network’s size and complexity.
- OSPF: This link-state protocol is ideal for larger networks, providing fast convergence and better scalability.
- EIGRP: A hybrid protocol that combines the benefits of both distance-vector and link-state methods, commonly used in enterprise networks.
- BGP: Primarily used for inter-network routing, BGP allows the management of large-scale networks, offering advanced features like route aggregation and policy-based routing.
Mastering these protocols ensures efficient routing decisions, faster recovery from network failures, and better resource utilization across the network.
2. Network Automation for Efficiency
Automation in network simulation saves time, reduces human error, and improves consistency in network configurations. By automating tasks such as device setup, monitoring, and troubleshooting, network administrators can streamline operations and focus on higher-level tasks.
- Configuration Templates: Use preconfigured templates for rapid deployment of network devices with consistent settings across the entire network.
- Scripting: Automate complex configurations using command-line scripts to quickly deploy settings, test changes, or implement bulk updates across multiple devices.
- Automated Testing: Run scripts to simulate different network conditions and validate network resilience, fault tolerance, and overall performance.
Automation not only speeds up network management but also ensures that network configurations are consistent and reliable throughout the simulation.
3. Troubleshooting Network Issues
Effective troubleshooting is critical to maintaining a smooth and functional network. Advanced diagnostic techniques allow for faster identification and resolution of issues, ensuring minimal downtime and uninterrupted operations. Common troubleshooting tools include:
- Packet Capture: Use packet analyzers to inspect network traffic for issues such as latency, dropped packets, or misconfigured devices.
- Device Logs: Analyze logs from network devices to identify configuration errors, hardware issues, or traffic bottlenecks.
- Simulated Link Failures: Disable network links or devices to test network resilience and automatic failover processes in a controlled environment.
By incorporating these troubleshooting methods, network professionals can ensure that their networks are optimized for performance and reliability under various conditions.
| Technique | Purpose | Benefits |
|---|---|---|
| Routing Protocol Configuration | Manage the flow of data through the network efficiently. | Improved traffic management, faster network convergence, and better fault tolerance. |
| Network Automation | Automate repetitive network tasks and configurations. | Increased efficiency, consistency, and reduced error rates. |
| Troubleshooting Tools | Identify and resolve network problems quickly. | Minimized downtime, faster issue resolution, and enhanced network stability. |
| Performance Optimization | Enhance the efficiency of network traffic and resource usage. | Reduced congestion, improved throughput, and better user experience. |
Applying these advanced techniques to network simulations can lead to more realistic, scalable, and efficient network environments, allowing users to create and test complex configurations while ensuring optimal performance.
Best Practices for Successful Networking
To achieve efficient, scalable, and reliable network configurations, it’s essential to follow certain guidelines that ensure optimal performance and security. These best practices help in minimizing errors, reducing downtime, and maintaining a network that can handle growing demands and unforeseen issues. Whether you’re working on a small local area network (LAN) or a large enterprise network, adhering to these principles will lead to smoother operations and a more robust network infrastructure.
First and foremost, proper planning is key. This includes designing the network with future scalability in mind, choosing the appropriate technologies, and ensuring redundancy for fault tolerance. Here are some best practices for achieving success in network design and management:
- Network Segmentation: Break the network into smaller, manageable segments to improve performance and security. Using VLANs (Virtual Local Area Networks) can help isolate traffic, reducing congestion and minimizing the risk of security breaches.
- Redundancy and Failover: Ensure high availability by implementing redundant devices and network paths. This guarantees that if one path fails, traffic can still be routed through another, minimizing network downtime.
- Security Measures: Apply the principle of least privilege and use strong encryption methods for data in transit. Firewalls, VPNs, and intrusion detection systems (IDS) are essential components for protecting the network from external threats.
- Effective IP Addressing: Implement a clear and logical IP addressing scheme that is easy to manage and scale. Utilize subnets effectively to segment traffic and ensure optimal network performance.
Another key area is network monitoring and documentation. Regular monitoring helps identify potential issues before they escalate, while documentation ensures that all configurations are well-documented and easily accessible for troubleshooting. The following practices should be considered:
- Continuous Monitoring: Use network monitoring tools to continuously check the health of the network, identifying performance bottlenecks or security threats before they impact operations.
- Automated Alerts: Set up alerts for critical network events, such as device failures or security breaches, to enable quick response and remediation.
- Documentation: Keep a detailed log of network configurations, topology changes, and troubleshooting steps taken. This makes it easier to manage the network and ensure consistency.
Lastly, regular training and keeping up with industry best practices is essential. The networking field is constantly evolving, so staying up-to-date with the latest technologies and methodologies ensures that the network infrastructure remains effective and secure in the long term. Network administrators should also collaborate with other IT departments to ensure that security, performance, and scalability goals are aligned across the entire organization.