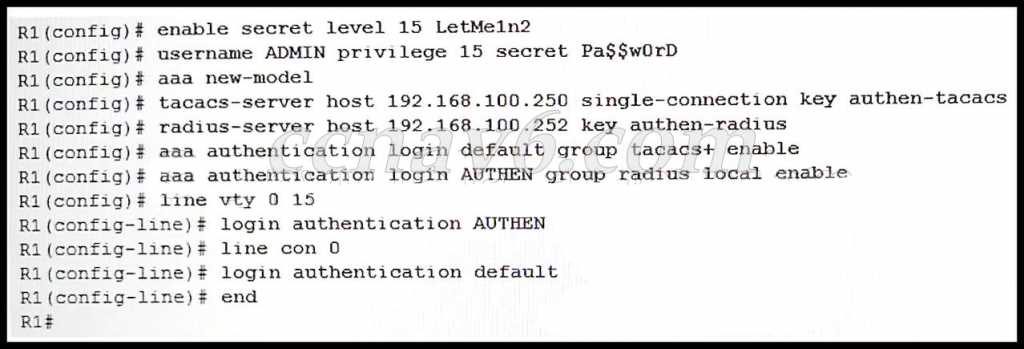
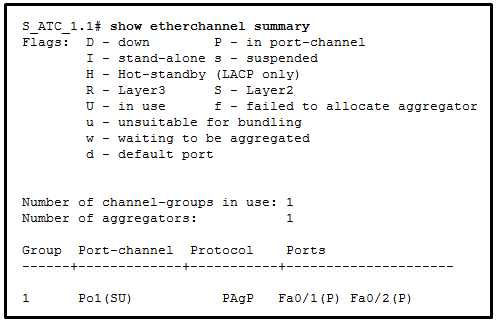
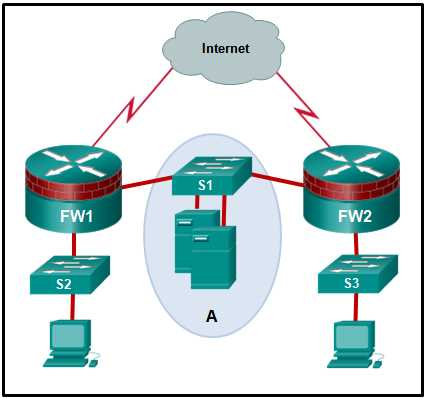
CCNA Security Chapter 5 Exam Answers

In this section, we dive into crucial concepts and strategies for safeguarding network infrastructures. Understanding how to implement and manage security measures is essential for maintaining a robust and secure environment. This knowledge serves as the foundation for effective defense against potential threats and vulnerabilities.
By exploring key methods for monitoring, controlling, and protecting data flow, you’ll learn how to enhance security policies and ensure comprehensive protection. The skills covered here will be vital for anyone looking to advance in the field of network administration and cyber defense.
Preparation involves both theoretical insights and practical application, equipping you to tackle a wide range of security challenges. As you progress, you’ll gain a deeper understanding of how various tools and protocols interact to form a resilient defense system.
CCNA Security Chapter 5 Exam Answers
This section focuses on the essential techniques and strategies used to protect network infrastructures from various threats. By understanding the core concepts and applying the right methodologies, individuals can ensure their systems are secure and resilient against cyberattacks. A solid grasp of these principles is key for anyone working with networks and striving for excellence in the field of digital security.
Effective preparation for this material requires both theoretical knowledge and practical application, allowing you to navigate through complex scenarios. By reviewing typical questions and solutions, you can better understand how to protect and monitor your network environment. Below is a summary of the most critical topics and their corresponding solutions, helping you build a strong foundation for any upcoming assessment.
| Topic | Description | Key Solution |
|---|---|---|
| Firewall Configuration | Managing and setting up firewalls to filter incoming and outgoing traffic | Ensure proper rule sets are applied based on network requirements |
| Access Control | Implementing access control lists (ACLs) to restrict unauthorized network access | Properly configure ACLs to allow only legitimate traffic |
| Intrusion Detection | Utilizing systems to detect and respond to potential breaches | Implement IDS to monitor and alert on suspicious activity |
| VPN Setup | Creating secure tunnels for remote access | Configure VPN protocols like IPSec for encrypted communications |
| Authentication Mechanisms | Implementing robust authentication methods to verify user identity | Use multi-factor authentication (MFA) for added security |
Understanding CCNA Security Exam Format
Grasping the structure and requirements of any evaluation is crucial for success. In the context of network defense assessments, it’s important to familiarize yourself with the different question types and the scoring system. This knowledge enables you to manage your time effectively and tailor your preparation accordingly.
Typically, these assessments consist of multiple-choice questions, drag-and-drop activities, and scenario-based tasks. Each question is designed to test both your theoretical understanding and practical application of key principles. Familiarity with the format will help you navigate through the sections with confidence and accuracy.
Time management also plays a significant role in performance. As some sections may involve complex problem-solving, being able to quickly identify the right approach and answer is essential. Practicing under timed conditions can give you an edge during the actual assessment.
Key Concepts of Chapter 5 Overview
This section focuses on the fundamental principles necessary for protecting network environments from various cyber threats. It covers a range of tools and techniques that ensure the integrity and confidentiality of data while allowing for secure communication. Understanding these concepts is vital for anyone involved in managing and defending network infrastructures.
Topics explored include methods for controlling network traffic, configuring defensive measures, and monitoring for potential intrusions. In addition, attention is given to ensuring that systems are properly authenticated, authorized, and audited, allowing for more effective threat mitigation. Mastering these essential concepts will equip you with the knowledge needed to build and maintain secure digital ecosystems.
Common Topics in Chapter 5 Questions
The questions in this section typically cover a variety of critical topics related to network defense and protection. These areas focus on techniques and tools used to monitor, control, and secure data within a network environment. Being familiar with these subjects is essential for ensuring a well-rounded understanding of network infrastructure security.
Some of the most common themes include firewall configurations, the use of access control lists (ACLs), methods for preventing unauthorized access, and systems designed to detect potential intrusions. Additionally, encryption methods and secure remote access protocols are frequently addressed, as they play a key role in maintaining secure communications. Understanding these topics thoroughly will enhance your ability to implement effective security strategies.
Importance of Network Security Protocols
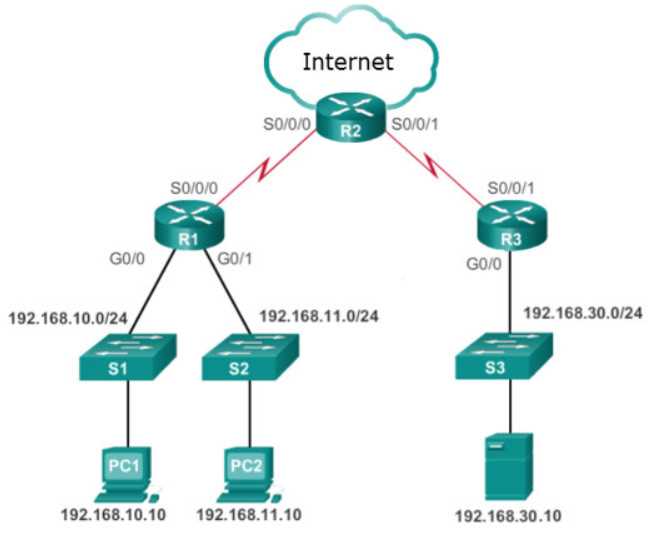
Network protocols are essential for ensuring the secure exchange of data across systems. These protocols provide the rules and guidelines that govern how devices communicate and authenticate each other within a network. Without strong protocols in place, sensitive information could be intercepted or compromised by malicious actors.
By implementing robust security protocols, organizations can protect the confidentiality, integrity, and availability of their network resources. Encryption protocols, for example, play a key role in safeguarding data during transmission, while authentication protocols ensure that only authorized users gain access to network services. Furthermore, monitoring protocols help detect and respond to potential threats in real time, minimizing the risk of an attack.
Overall, these protocols form the backbone of a network’s defense, enabling safe communication, data integrity, and reliable access controls. Without them, any network would be vulnerable to breaches and exploitation.
Role of Firewalls in Security Tests
Firewalls play a crucial role in protecting network systems by controlling the flow of traffic and preventing unauthorized access. During security evaluations, firewalls are one of the first lines of defense, ensuring that only legitimate traffic is allowed while blocking potential threats. Understanding how firewalls operate and how to properly configure them is essential for maintaining a secure environment.
In security assessments, firewalls are often tested to verify their effectiveness in several key areas:
- Traffic Filtering: Firewalls examine incoming and outgoing network traffic, filtering based on predefined rules to block unwanted data.
- Intrusion Prevention: By detecting and blocking malicious traffic, firewalls can prevent many types of cyberattacks.
- Access Control: Firewalls regulate access to and from networks, ensuring only authorized users and devices can communicate with protected resources.
- Logging and Monitoring: They keep detailed logs of network activity, providing insights into potential security incidents.
Properly configured firewalls are essential not only for preventing direct attacks but also for maintaining the overall integrity of the network by blocking potential vulnerabilities. Their role in security tests ensures that the network is protected against a wide range of external threats and unauthorized access attempts.
How to Prepare for CCNA Chapter 5
Effective preparation for network defense topics requires a combination of theoretical understanding and hands-on practice. By mastering key concepts and becoming familiar with common tools and configurations, you can ensure a solid foundation for tackling advanced network protection challenges. Proper study techniques and consistent practice are key to performing well in this section.
Start by reviewing the fundamental concepts related to traffic filtering, access control, and threat mitigation. Focus on understanding how firewalls, intrusion detection systems, and encryption protocols work together to protect a network. In addition to reading materials, practical exercises, such as lab simulations, help reinforce your knowledge and give you the opportunity to configure and test real-world scenarios.
Additionally, make use of practice tests to assess your readiness. This helps you familiarize yourself with the format of the material and identify areas that need further attention. Regular review of key concepts, combined with practical application, will ensure you are well-prepared for any challenges you may encounter.
Common Mistakes to Avoid in Exams

When preparing for any test, it’s important to be aware of common pitfalls that can hinder your performance. These mistakes often arise from a lack of attention to detail or inadequate preparation. By understanding what to avoid, you can approach the assessment with confidence and accuracy, minimizing the chances of errors that could cost valuable points.
One of the most frequent mistakes is rushing through questions without fully reading them. This can lead to misinterpreting the requirements and choosing incorrect answers. Another common error is failing to manage time effectively, which may result in incomplete responses or rushed solutions. It’s also easy to overthink certain questions, leading to second-guessing or changing answers unnecessarily.
| Common Mistake | Why It Happens | How to Avoid It |
|---|---|---|
| Rushing through questions | Impatience or lack of time management | Take your time to read each question thoroughly before answering |
| Overthinking answers | Second-guessing initial responses | Trust your first instinct and avoid unnecessary changes |
| Ignoring instructions | Failure to focus on exam guidelines | Always review the instructions carefully before starting |
| Skipping practice | Lack of preparation and familiarity with test format | Engage in regular practice tests and simulated scenarios |
By being mindful of these common mistakes and adopting a strategic approach to preparation, you can significantly improve your performance and increase your chances of success. A calm, focused mindset and proper planning are essential for achieving the best results.
Effective Time Management for Exam Success
Time management is a crucial aspect of performing well in any assessment. Without a structured approach to allocating your time, it becomes easy to get overwhelmed or leave questions unanswered. Effective time management allows you to tackle each section methodically, ensuring that you give adequate attention to every task and finish the evaluation on time.
To improve time management during an assessment, consider the following strategies:
- Prioritize difficult questions: Start with the questions that you find most challenging. This allows you to give them the time and attention they require while your mind is fresh.
- Set time limits for each section: Divide the total time available by the number of sections or questions, ensuring you don’t spend too much time on one task.
- Stay calm and focused: Panicking can waste precious time. Take deep breaths and move forward systematically, even if a question seems difficult at first.
- Review your answers: Leave time at the end to review your responses. This will allow you to correct any mistakes or rethink any answers you might be uncertain about.
By managing your time effectively, you ensure that you can complete each section of the test thoughtfully and with confidence, improving your chances of success. Practice these strategies during your preparation to build a sense of timing that works best for you.
Resources for Studying Network Protection
When preparing for an assessment in network defense, utilizing the right resources is essential for mastering the necessary concepts. These materials can help you build both theoretical knowledge and practical skills, making you well-prepared for challenges that may arise in real-world scenarios. From textbooks and online courses to hands-on labs, there are numerous tools available to aid your studies.
Here are some of the best resources to help you succeed:
- Official Study Guides: These comprehensive guides cover the core topics in detail and provide structured learning paths. They often include practice questions, examples, and review exercises to reinforce key concepts.
- Online Learning Platforms: Websites like Udemy, Pluralsight, and LinkedIn Learning offer video courses that explain complex topics in an easy-to-understand format. Many also provide quizzes and assessments to test your understanding.
- Hands-on Labs: Virtual labs allow you to practice real-world scenarios in a controlled environment. Tools like Cisco Packet Tracer and GNS3 provide simulated networks where you can experiment with configurations and troubleshoot issues.
- Discussion Forums: Online communities such as Reddit, Stack Exchange, and specialized networking forums allow you to ask questions, share insights, and learn from others’ experiences.
- Practice Tests: Taking mock exams or practice questions helps you familiarize yourself with the test format and time constraints. It also helps you pinpoint areas where you need to focus your efforts.
By incorporating a mix of these resources into your study plan, you will develop a well-rounded understanding of network protection principles and improve your chances of success in the assessment. Keep a consistent study schedule and regularly test your knowledge to ensure you’re ready when the time comes.
How to Approach Multiple-Choice Questions
Multiple-choice questions can often be tricky, but with the right approach, they become easier to navigate. The key to answering them correctly lies in understanding the question thoroughly, evaluating all available options, and applying logical reasoning. With a strategic mindset, you can increase your accuracy and make the best choices even when faced with challenging options.
Here are some tips for effectively handling multiple-choice questions:
- Read the question carefully: Before jumping into the answer choices, make sure you understand exactly what the question is asking. Look for keywords and instructions to avoid misinterpreting the question.
- Evaluate all options: Never settle for the first option that seems correct. Review all answer choices to ensure that you are selecting the most accurate one.
- Eliminate clearly incorrect answers: Start by crossing out any options that you know are wrong. This improves your odds of selecting the correct answer from the remaining choices.
- Look for clues in the wording: Pay attention to qualifying words like “always,” “never,” “most,” or “least.” These can give you hints about which answers are more likely to be correct.
- Trust your instincts: If you’re unsure after evaluating all options, go with your first choice. Second-guessing often leads to mistakes.
By following these steps, you can maximize your performance in multiple-choice sections. Remember to stay calm, stay focused, and approach each question methodically to ensure you’re making the best choices under time constraints.
| Strategy | Description |
|---|---|
| Read carefully | Understand the question and instructions before selecting an answer |
| Eliminate incorrect choices | Rule out answers that are clearly wrong to increase your chances |
| Look for keywords | Identify clues in the wording of the question and options |
| Trust your instincts | Don’t second-guess; often, your first choice is correct |
Deep Dive into Security Technologies
Understanding the various technologies used to protect network infrastructure is essential for anyone working in the field of network defense. These technologies help safeguard data, prevent unauthorized access, and maintain the integrity of systems and communications. By gaining a deeper insight into the mechanisms behind these tools, you can better grasp how they work together to form a robust defense against threats.
Common Network Protection Technologies
Several core technologies are commonly employed to enhance network protection. These solutions address various vulnerabilities and offer both proactive and reactive measures. Below are the key technologies you should be familiar with:
- Firewalls: These devices act as barriers between trusted internal networks and untrusted external networks. They filter incoming and outgoing traffic based on predefined security rules.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity and known threats. They alert administrators of potential breaches or unauthorized access attempts.
- Intrusion Prevention Systems (IPS): Similar to IDS, IPS actively works to block or prevent malicious activity based on detected threats in real time.
- Virtual Private Networks (VPN): VPNs create encrypted tunnels over the internet, allowing remote users to securely access the network from anywhere.
- Anti-Malware Software: These tools are designed to detect, quarantine, and remove malicious software from the system, helping to mitigate the risk of malware infections.
Advanced Security Measures

In addition to basic technologies, more advanced tools and strategies are employed to strengthen network protection. These technologies typically involve specialized configurations and may require a higher level of expertise to implement and manage effectively:
- Network Access Control (NAC): NAC enforces policies regarding who can access network resources and under what conditions. It helps ensure that only compliant devices and users can access critical systems.
- Two-Factor Authentication (2FA): This security measure requires users to provide two forms of verification before accessing sensitive information or systems, adding an additional layer of protection beyond passwords.
- Data Loss Prevention (DLP): DLP systems help prevent sensitive data from being transmitted or accessed by unauthorized users, reducing the risk of data breaches.
- Endpoint Detection and Response (EDR): EDR solutions monitor and respond to threats on individual devices, providing real-time analysis and remediation for endpoints like laptops, desktops, and mobile devices.
Mastering the use and configuration of these technologies is critical for ensuring comprehensive protection across the entire network infrastructure. By understanding their roles and how they interconnect, you can develop a more effective defense strategy to combat modern threats.
Practice Questions for Chapter 5 Review

To assess your understanding of the material covered in the fifth section, it’s essential to engage in practice questions. These questions not only reinforce key concepts but also help identify areas where further review may be needed. By challenging yourself with questions based on the topics covered, you can better prepare for real-world scenarios and testing environments.
Here are some example questions to guide your review process:
- Question 1: What is the primary function of a network firewall, and how does it contribute to overall network protection?
- Question 2: Describe the differences between an Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS). How does each contribute to identifying and mitigating threats?
- Question 3: What role does a Virtual Private Network (VPN) play in securing remote communication? Explain its key features and benefits.
- Question 4: Explain the concept of access control lists (ACLs) and their significance in controlling network traffic. How can ACLs be used to enhance security?
- Question 5: Define what a man-in-the-middle attack is and discuss potential methods to prevent such attacks in a network environment.
By working through these questions, you can gauge your comprehension of the material and ensure you are well-prepared for practical application and further studies. Keep in mind that answering these questions without looking at the solutions will provide a more effective learning experience.
Understanding Access Control Lists
Access control lists (ACLs) are a fundamental concept in network management, allowing administrators to define and manage permissions for users or devices. These lists specify which resources can be accessed, by whom, and under what conditions. By configuring ACLs, network traffic can be filtered, ensuring only authorized devices or users are allowed access to specific services and resources.
In essence, ACLs work as filters, controlling both inbound and outbound traffic to improve security and optimize network performance. They are primarily used to restrict or allow data flow based on various parameters such as IP addresses, protocols, ports, or even specific applications. Understanding how to configure and apply these rules is essential for managing a secure network environment.
Types of Access Control Lists
There are two main types of ACLs that are commonly used in network security:
- Standard ACLs: These lists filter traffic based on the source IP address only, making them simple to configure and apply. However, they offer limited granularity.
- Extended ACLs: Extended ACLs allow for more complex filtering by including additional criteria such as destination IP addresses, protocol types, and port numbers.
Best Practices for Implementing ACLs
When working with ACLs, it’s crucial to follow best practices to maximize their effectiveness and minimize the risk of misconfigurations:
- Order of Rules: ACLs process rules from top to bottom. Ensure more specific rules are placed at the top to avoid unintended matches.
- Minimize the Scope: Apply ACLs only where necessary to avoid network-wide performance degradation.
- Test Configurations: Always test ACLs in a controlled environment to verify they are functioning as expected before deployment.
- Monitor and Review: Regularly monitor ACLs for changes in network traffic patterns and review them periodically to ensure they remain aligned with current network requirements.
By mastering the use of access control lists, network administrators can significantly enhance the security posture of their networks while ensuring that traffic is appropriately managed and monitored.
Benefits of Hands-On Lab Exercises
Hands-on lab exercises play a crucial role in mastering technical concepts and developing practical skills. They provide learners with the opportunity to apply theoretical knowledge in real-world scenarios, enhancing their understanding and problem-solving abilities. By actively engaging with the material, individuals can gain a deeper insight into the workings of complex systems and technologies.
One of the key benefits of hands-on labs is the ability to experience firsthand how different configurations, protocols, and tools interact in a controlled environment. This practical exposure helps bridge the gap between textbook knowledge and real-world application, allowing learners to build confidence in their abilities to tackle technical challenges.
Practical Experience
Unlike passive learning methods, hands-on labs encourage active participation and experimentation. This direct involvement enables individuals to:
- Develop critical thinking skills: Solving problems in a lab environment helps enhance decision-making and troubleshooting capabilities.
- Learn through trial and error: Mistakes made during lab exercises provide valuable learning experiences and help solidify concepts.
- Build technical proficiency: Repeated exposure to tools and technologies helps to develop competence and familiarity with complex systems.
Enhanced Retention
Hands-on labs improve retention by engaging multiple senses and providing practical application of knowledge. Studies have shown that learners are more likely to retain information when they actively work with the material, rather than just reading or listening. By performing tasks themselves, individuals reinforce what they have learned, making the information easier to recall when needed.
Confidence in Real-World Situations
Engaging in hands-on practice boosts self-confidence, as learners gain experience in handling real-life scenarios. When faced with similar challenges in the future, individuals will feel more capable and prepared. This confidence is essential not only for exams but also in professional environments where practical skills are paramount.
In summary, hands-on lab exercises are an invaluable resource for mastering technical subjects, offering practical experience, improved retention, and enhanced confidence. By incorporating these exercises into their learning routine, individuals can ensure a more comprehensive and effective understanding of the material.
Tips for Passing the Certification Test
Successfully completing a certification test requires a strategic approach that combines knowledge, practice, and proper time management. By understanding key concepts, engaging in practical exercises, and mastering test-taking strategies, you can improve your chances of success. Below are some essential tips to help you prepare effectively and confidently for the test.
Master the Key Concepts
Before attempting the certification test, it is crucial to thoroughly understand the core principles of the subject. Focus on grasping the fundamentals and the practical applications of the material. This foundation will not only help you answer questions more accurately but will also give you confidence when approaching more complex scenarios during the test.
Practice with Real-World Scenarios

Engaging in hands-on practice is one of the most effective ways to reinforce your knowledge. Set up simulations or labs to experiment with real-world configurations, tools, and techniques. This will allow you to develop problem-solving skills and familiarize yourself with the actual tasks that you might encounter during the test.
Understand the Question Format
Familiarizing yourself with the types of questions that appear on the test can help you approach each one strategically. Multiple-choice, drag-and-drop, and simulation questions each require different techniques. Practice answering questions from previous tests or use study materials that simulate the real exam environment. This will allow you to gauge the difficulty level and become comfortable with the format.
Review Key Areas Frequently
Repetition is key to retention. Set aside regular study sessions to go over your notes, flashcards, and practice questions. Focus particularly on the areas that are most challenging for you. By consistently revisiting difficult topics, you reinforce your understanding and improve your chances of recalling the information during the test.
Manage Your Time Effectively
Time management is essential when taking any test. Practice solving questions within a time limit to ensure you can complete the test in the allotted time. During the actual test, prioritize questions you find easier and return to more challenging ones later. This strategy helps you maximize your performance and avoid spending too much time on difficult questions.
Stay Calm and Focused

Maintaining a calm and focused mindset during the test is crucial for optimal performance. If you encounter a question you’re unsure about, take a deep breath and move on. Stress can cloud your judgment and lead to mistakes. Trust in your preparation and approach each question with a clear mind.
By following these tips, you can significantly increase your chances of passing the certification test. A solid understanding of the material, combined with effective preparation strategies, will help you achieve success and earn your certification.
Post-Test: What to Do Next
After completing a certification assessment, it’s important to reflect on your performance and take the right steps to move forward. Whether you passed or need to retake the test, the post-test phase offers valuable opportunities for growth and improvement. Here’s a guide on how to handle the next steps after your assessment.
Evaluate Your Performance
The first thing to do after finishing the test is to evaluate how you performed. If the results are available immediately, take a moment to review your scores and identify areas where you did well and where improvement is needed. Reflect on the types of questions that challenged you and assess whether there were any unexpected topics. If your score was lower than expected, this is a chance to understand why and focus on the areas that need attention in future attempts.
Celebrate Your Success or Plan for Improvement
If you passed, congratulations on your accomplishment! Take the time to celebrate your success and acknowledge the effort you’ve put into preparing. This achievement is a major milestone in your professional development. Consider updating your resume or portfolio to reflect your new certification and look for opportunities to apply your knowledge in real-world situations.
If the results were not as expected, don’t get discouraged. A failed attempt is not the end of the road, but an opportunity to reassess your study strategy. Review the areas that you struggled with, and make a plan to fill in any gaps in your understanding. Consider using different study materials or enrolling in a course for more structured learning. Retaking the test with better preparation will put you in a strong position to succeed next time.
Stay Engaged with the Learning Community
Whether you passed or are preparing for a retake, staying engaged with the learning community is important. Participate in online forums, study groups, or workshops to continue improving your skills. Learning from others, sharing experiences, and discussing difficult topics can provide fresh perspectives and enhance your knowledge base.
In addition to formal studying, real-world experience can be invaluable. Look for internships, volunteer opportunities, or projects where you can apply what you’ve learned. Hands-on practice will reinforce the concepts you’ve studied and help you retain the information more effectively.
Remember, the journey doesn’t stop after the test. Keep learning, stay motivated, and continue pushing towards your professional goals. Every step you take, whether in success or failure, brings you closer to mastery and growth in your field.