Qualys Vulnerability Management Exam Answers
In today’s digital landscape, securing systems and identifying potential weaknesses has become a critical task. Understanding how to evaluate and address these risks is essential for any professional in the field of cybersecurity. Achieving proficiency in these areas can greatly enhance your ability to respond effectively to various threats and safeguard organizational assets.
Preparation for assessments in this domain requires more than just memorizing concepts; it involves gaining practical insights into how tools are applied and how to interpret results. This guide aims to provide key insights into the necessary knowledge and skills, enabling you to tackle challenges confidently and efficiently. By focusing on both theoretical understanding and hands-on application, you can ensure success and stay ahead of emerging security risks.
Effective study techniques and a clear grasp of core principles are vital in mastering the nuances of the field. Whether you’re new to the subject or looking to enhance your existing knowledge, a structured approach is crucial for success. This resource will guide you through the essential areas, offering practical tips to help you prepare thoroughly.
Qualys Vulnerability Management Exam Answers

When preparing for a comprehensive cybersecurity evaluation, it’s crucial to grasp both the theoretical concepts and practical applications of assessing system weaknesses. The ability to effectively identify, analyze, and address security gaps is fundamental for success in this type of assessment. Candidates must demonstrate a deep understanding of how different tools interact with organizational infrastructures to uncover potential risks and flaws.
Key Concepts for Success
Familiarity with core principles is essential. A well-rounded knowledge base allows candidates to approach complex scenarios with confidence. Understanding the tools at your disposal, how they are configured, and how to interpret their findings will help ensure that you’re well-prepared for the challenges presented. Focus should be placed on the critical aspects such as risk prioritization, remediation steps, and the broader context of maintaining a secure environment.
Preparation Tips and Study Resources
Effective preparation involves more than simply reviewing theoretical knowledge. Hands-on experience with the tools and scenarios is equally important. Exploring real-world cases, reviewing sample reports, and taking mock assessments can provide valuable insights. Leveraging study resources such as guides, online courses, and community forums can also help refine your understanding and ensure you’re ready for the test.
Overview of Qualys Vulnerability Management
In the realm of cybersecurity, it’s essential to have a comprehensive system in place to detect and address potential risks within an organization’s infrastructure. This process involves a combination of tools and methodologies aimed at identifying weak points, analyzing their impact, and taking corrective action to mitigate any threats. Successful implementation of such strategies helps protect critical assets from evolving cyber threats.
Security tools designed for these purposes are indispensable for organizations aiming to maintain a secure environment. These tools scan networks, applications, and systems to detect potential issues that could be exploited by malicious actors. The results from these scans are then analyzed to prioritize remediation efforts based on the severity of each identified risk. By applying these techniques, organizations can proactively reduce their attack surface and improve overall security posture.
Strategic implementation of these systems requires a clear understanding of both the tools available and the security challenges facing an organization. A well-rounded approach to these processes not only helps in identifying weaknesses but also enables businesses to address them efficiently, minimizing downtime and potential damage from cyber threats.
Key Topics in Vulnerability Management Exam

To effectively prepare for an assessment in the field of cybersecurity risk identification, it’s important to focus on the main subjects covered in such evaluations. These areas typically involve understanding the tools used for system analysis, interpreting scan results, and applying best practices for resolving discovered weaknesses. A deep understanding of these topics will not only help in passing the assessment but also provide valuable skills for managing security threats in real-world scenarios.
Important Areas to Focus On
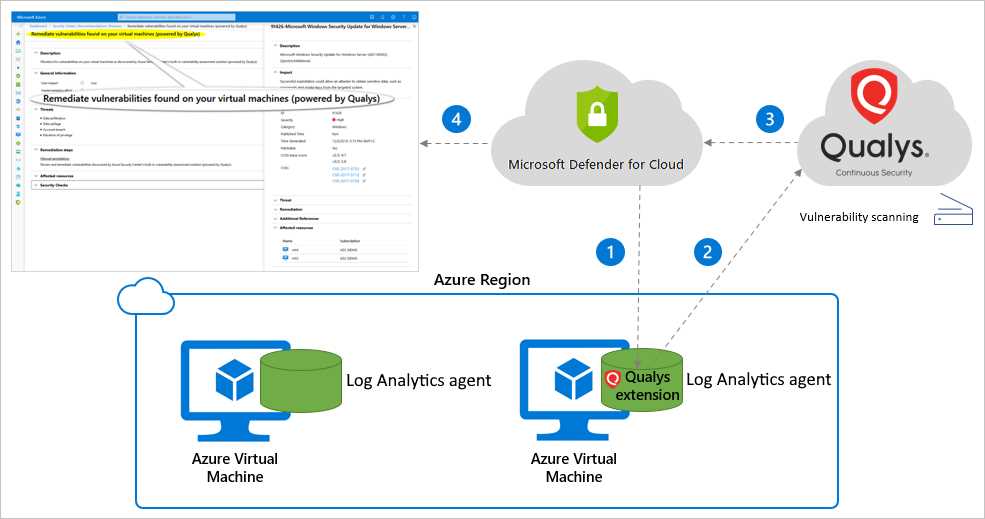
When preparing for the assessment, several key areas should be prioritized. These topics provide the foundation for a comprehensive understanding of the processes involved in identifying and addressing risks. Below is a summary of some of the core subjects that are typically covered:
| Topic | Description |
|---|---|
| Risk Assessment | Understanding how to assess the severity and potential impact of identified security issues. |
| Security Tools | Familiarity with scanning and analysis tools used to detect system weaknesses. |
| Remediation Processes | Steps to take in fixing detected issues, including patching and configuration changes. |
| Reporting and Prioritization | How to interpret scan results, prioritize fixes, and communicate findings effectively. |
| Compliance Standards | Knowledge of relevant industry regulations and standards for securing systems and networks. |
Practical Applications of Key Concepts
Each of these topics plays a crucial role in maintaining a secure environment. For example, risk assessment techniques help determine which issues should be addressed first, ensuring resources are focused on the most critical areas. Similarly, understanding how to use security tools effectively can greatly improve the accuracy of scans and reduce the likelihood of overlooking significant risks. Preparing for the evaluation involves not only learning the theory but also practicing these skills in real-world scenarios to ensure a complete grasp of the subject matter.
Essential Skills for Qualys Exam Success
Success in any cybersecurity assessment requires more than just theoretical knowledge; it involves the practical application of skills that allow you to analyze, identify, and resolve system weaknesses effectively. Developing a solid understanding of the tools and techniques used in risk detection and remediation is key. Here are some of the most important abilities you need to master to excel in this type of evaluation:
- Critical Thinking: The ability to analyze complex scenarios, interpret findings, and prioritize tasks based on their severity is vital. Clear judgment is necessary to make informed decisions about what actions should be taken first.
- Technical Proficiency: Understanding the technical aspects of the tools and systems being used is essential. You should be familiar with configuration settings, common issues, and how to properly conduct scans and interpret the results.
- Problem-Solving Skills: Once vulnerabilities or risks are identified, the next step is to implement solutions. This may involve patching systems, adjusting configurations, or applying mitigation strategies to reduce potential threats.
- Attention to Detail: A keen eye for small but significant details can make a difference when analyzing scan results. Overlooking minor issues could lead to larger security gaps down the line.
- Time Management: Knowing how to balance multiple tasks and meet deadlines is essential when working with complex systems. Being able to quickly prioritize and address the most pressing issues will save valuable time and resources.
In addition to these core abilities, it’s also important to stay current with the latest trends and technologies in the cybersecurity field. Tools and techniques evolve rapidly, so continuous learning and adaptability are crucial for long-term success. Practicing these skills in real-world scenarios and through mock assessments will give you the confidence needed to tackle any challenges you encounter during the evaluation.
Preparing for Vulnerability Assessment Test
Effective preparation for a cybersecurity assessment requires a combination of theoretical knowledge and practical skills. It’s important to understand both the tools and the processes involved in identifying and resolving weaknesses within an organization’s infrastructure. Focusing on core areas such as risk analysis, security protocols, and best practices will provide a solid foundation for the test.
Familiarity with tools and techniques is crucial when preparing for the evaluation. You should become proficient in using scanning tools, understanding the reports generated, and knowing how to address issues identified during scans. Practice with real-world scenarios can help build confidence and improve your ability to quickly identify and mitigate risks during the assessment.
Time management also plays a significant role in preparation. Being able to allocate your attention efficiently to various tasks during the assessment is essential. Focus on mastering techniques that allow you to handle multiple tasks simultaneously, prioritize critical issues, and make decisions quickly to address the most pressing security concerns.
In addition to mastering the technical skills, ensure that you are well-versed in industry standards and best practices for securing systems. This knowledge will help you make informed decisions and apply the right approach when addressing the risks that arise in the test scenario.
Understanding the Exam Structure and Format
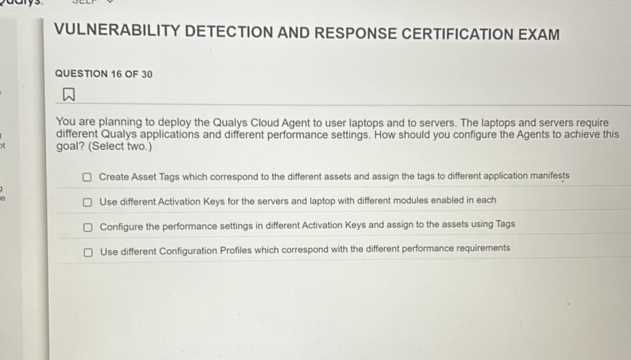
To succeed in any professional assessment, it is essential to have a clear understanding of its structure and format. Knowing what to expect allows candidates to focus their efforts on the most important aspects and manage their time effectively. Typically, these evaluations consist of various sections designed to test both theoretical knowledge and practical application, ensuring that individuals are prepared for real-world challenges.
Types of Questions
The test generally includes a mix of multiple-choice questions, scenario-based inquiries, and practical exercises. Multiple-choice questions often assess foundational knowledge, testing your understanding of key concepts and terminology. Scenario-based questions, on the other hand, are designed to evaluate your problem-solving abilities in a real-world context, where you must apply your knowledge to identify and address security risks.
Time Management and Strategy
Time management is a crucial aspect of preparing for this kind of evaluation. Candidates must be able to quickly analyze questions, prioritize responses, and allocate their time effectively across various sections. A well-thought-out strategy that involves carefully reading each question and managing time efficiently will help ensure that you can address all areas of the test without feeling rushed.
Common Mistakes to Avoid During the Exam
When preparing for a cybersecurity evaluation, it’s crucial to not only understand the material but also avoid common pitfalls that can undermine your performance. Being aware of these mistakes can help you navigate the assessment with confidence and increase your chances of success. These errors often arise from misinterpreting questions, improper time management, or failing to apply practical knowledge effectively.
Rushing Through Questions is one of the most frequent mistakes made during assessments. While it may be tempting to move quickly, especially when time is limited, this can lead to careless errors. It’s important to read each question thoroughly and consider all available options before making a decision. Rushing may result in overlooking critical details that could lead to incorrect answers.
Neglecting to Review Your Answers is another mistake that many candidates make. After completing the test, always take the time to review your responses. A fresh look at the questions can often reveal mistakes or misinterpretations that may have been missed during the first pass. This extra step can be the difference between a passing and failing score.
Failing to Manage Time Effectively can cause unnecessary stress and prevent you from completing the test in a timely manner. Be sure to allocate your time wisely across the different sections of the evaluation. If you’re stuck on a difficult question, move on and come back to it later if time allows. Managing your time ensures you can give each section the attention it deserves.
How to Study Effectively for Certification
To perform well in any professional assessment, a structured and focused study plan is key. Effective preparation not only involves reviewing concepts but also practicing their application in real-world scenarios. Building a deep understanding of core topics and continuously testing yourself will ensure that you’re well-prepared when the time comes to take the evaluation.
Start by reviewing the foundational concepts and terminology related to the field. Make sure you understand the core principles, as these will serve as the basis for more advanced topics. Use a variety of study materials, such as official guides, online courses, and practice exams, to reinforce your understanding and expose yourself to different types of questions.
Additionally, incorporate hands-on practice to enhance your skills. Theoretical knowledge alone isn’t enough–practical experience allows you to apply what you’ve learned in real situations. Try to simulate common scenarios you might encounter, as this will help you build confidence and problem-solving abilities.
Finally, ensure that you manage your study time effectively. Break down your preparation into manageable segments, focusing on one topic at a time. Don’t rush through the material–take time to review and reinforce each section before moving on. Consistent, focused study sessions are much more effective than cramming at the last minute.
Resources for Certification Preparation
Preparing for a cybersecurity certification requires access to the right tools, materials, and support. With the wealth of resources available, it can be difficult to know where to start. A combination of online courses, books, practice exams, and hands-on labs can provide the depth of knowledge and experience needed to succeed. Below are some of the most valuable resources you can use to enhance your preparation:
Online Learning Platforms
- Udemy: Offers a variety of courses tailored to cybersecurity professionals, with in-depth content and practice questions for better preparation.
- Pluralsight: Known for high-quality technical training, Pluralsight offers specific courses on risk assessment, security tools, and best practices.
- LinkedIn Learning: Features courses that cover a wide range of cybersecurity topics, providing both introductory and advanced lessons.
Books and Study Guides
- Official Study Guides: These guides often cover the exact syllabus of the certification and include sample questions, exam tips, and detailed explanations of key topics.
- Cybersecurity Essentials: Books that offer a comprehensive understanding of the field and provide context for real-world application.
- Practice Exam Books: These books provide sample questions and answers, which help simulate exam conditions and identify areas that require more focus.
By leveraging a combination of these resources, you can tailor your study plan to suit your learning style and needs, ensuring a well-rounded preparation for the certification.
Role of Risk Assessment in Cybersecurity
In today’s digital landscape, identifying and addressing weaknesses within an organization’s infrastructure is crucial for maintaining security. Risk assessment plays a central role in protecting systems and sensitive data from threats by helping security teams prioritize and mitigate potential risks. This proactive approach ensures that organizations can defend against evolving cyber threats and maintain a secure environment.
Effective risk assessment involves a structured process that encompasses multiple stages. It helps organizations identify potential entry points for malicious actors, evaluate the severity of threats, and implement appropriate safeguards. Without this process, companies may struggle to detect vulnerabilities and respond quickly to emerging risks.
Key Benefits of Risk Assessment
- Proactive Threat Detection: By regularly identifying and assessing risks, organizations can anticipate potential threats before they become critical issues.
- Resource Optimization: Prioritizing risks ensures that organizations focus their resources on the most significant threats, improving overall efficiency.
- Compliance and Regulatory Adherence: Risk assessments help organizations meet industry standards and regulations related to cybersecurity, ensuring compliance.
Core Elements of a Risk Assessment Strategy
- Risk Identification: The first step involves discovering potential weaknesses or security gaps in the system.
- Risk Evaluation: After identifying risks, the next step is to assess the likelihood of these threats materializing and their potential impact.
- Mitigation and Response: Once risks are evaluated, security teams implement appropriate measures to minimize potential damage and address vulnerabilities.
In summary, risk assessment is a critical component of a robust cybersecurity strategy. It allows organizations to stay one step ahead of threats, protect sensitive data, and ensure the integrity of their systems.
Tools and Their Applications in Cybersecurity
In the field of cybersecurity, utilizing the right tools is essential to identify, assess, and address potential security gaps within an organization’s systems. These tools help security professionals streamline their processes, improve their response times, and ensure that critical vulnerabilities are mitigated effectively. A comprehensive suite of tools is designed to provide a wide range of capabilities, from scanning and monitoring to reporting and remediation.
These tools are typically employed across various stages of the security lifecycle, allowing organizations to gain visibility into their infrastructure, detect potential weaknesses, and take action to minimize risks. Their applications extend from simple vulnerability scanning to more complex threat detection and compliance monitoring, offering users the ability to continuously assess their security posture.
Key Tools in Cybersecurity
- Network Scanners: These tools automatically scan networks for potential weaknesses, mapping out vulnerabilities and providing detailed reports on where defenses are lacking.
- Configuration Management Tools: Used to ensure that devices, software, and network configurations comply with security policies and standards, reducing the chances of misconfigurations leading to vulnerabilities.
- Compliance Tools: Essential for ensuring that an organization’s security practices meet regulatory standards, these tools help in tracking and reporting compliance across various industry regulations.
Applications of These Tools
- Continuous Monitoring: Tools that provide real-time monitoring capabilities allow security teams to detect potential threats as they occur and respond quickly.
- Risk Assessment: By assessing an organization’s infrastructure, tools can identify and prioritize risks based on severity, enabling teams to focus on critical issues first.
- Automated Reporting: With automated reporting, cybersecurity tools generate actionable insights and detailed reports, helping organizations stay informed about their security posture.
Using the right combination of these tools is crucial for an efficient and effective cybersecurity strategy. They provide essential capabilities that support proactive defense, streamlined risk management, and enhanced compliance, which ultimately safeguard the organization from potential threats and data breaches.
Commonly Asked Questions in the Assessment
When preparing for a certification or assessment in the field of cybersecurity, it’s important to anticipate the types of questions that might be asked. These assessments are designed to test your understanding of various core concepts and your ability to apply them in real-world scenarios. The questions often cover a broad range of topics related to system security, risk mitigation, and effective practices for maintaining a secure environment.
Below are some of the commonly asked questions that candidates may encounter. These questions typically evaluate both theoretical knowledge and practical skills necessary for addressing potential security issues and ensuring that systems are resilient against threats.
Frequently Asked Questions

- What are the different types of risks organizations face? – This question aims to test your understanding of the various threats that can compromise an organization’s security, including network, software, and operational risks.
- How would you prioritize security vulnerabilities? – Candidates may be asked to explain how they would assess and prioritize security weaknesses based on factors such as severity, impact, and exploitability.
- What is the role of patch management in system security? – This question focuses on understanding the importance of regularly updating software and systems to protect against known threats.
- Describe the process of conducting a risk assessment. – Candidates should demonstrate knowledge of how to identify, assess, and mitigate risks to secure infrastructure.
- What are the key differences between preventive and detective security controls? – This question aims to assess knowledge about different types of security controls and their applications in reducing risks.
Practical Application Questions
- How would you handle a security breach in a cloud-based environment? – Candidates may be asked to outline steps for responding to and mitigating a breach in a cloud infrastructure.
- Explain how automated tools can enhance cybersecurity efforts. – This question tests your knowledge of how automation can improve efficiency in detecting and addressing security issues.
- What strategies would you use to ensure compliance with industry security standards? – This question focuses on understanding how to align an organization’s practices with regulatory requirements such as GDPR or HIPAA.
By preparing for these questions and understanding the core concepts, candidates can increase their chances of success and demonstrate their ability to effectively manage and address cybersecurity challenges.
Best Practices for Remediating Security Weaknesses
Addressing security weaknesses within a system is a critical component of any comprehensive security strategy. Effective remediation ensures that potential risks are minimized and that an organization’s infrastructure remains resilient against evolving threats. The process involves identifying weaknesses, determining their impact, and applying the appropriate measures to fix or mitigate them in a timely manner.
To ensure the highest level of protection, it’s essential to follow industry-recognized best practices when remediating security gaps. These practices help prioritize actions, reduce exposure to threats, and establish a proactive approach to security. Below are several key practices that should be followed to achieve successful remediation.
Key Best Practices
- Prioritize Remediation Based on Risk: Not all weaknesses pose the same level of threat. It’s important to assess and prioritize them according to their severity, exploitability, and potential impact on the organization. This ensures that the most critical issues are addressed first.
- Apply Patches and Updates Regularly: One of the simplest yet most effective ways to remediate security flaws is by ensuring that all software and systems are up to date. Applying patches promptly reduces the risk of exploitation from known vulnerabilities.
- Implement Strong Access Controls: Limiting access to sensitive systems and data is key to reducing the potential impact of a security breach. Properly configured access controls, such as role-based access and least privilege policies, can prevent unauthorized access to critical assets.
- Conduct Root Cause Analysis: When addressing security weaknesses, it is important to understand the root cause to prevent future occurrences. A thorough analysis helps identify underlying issues such as misconfigurations, weak processes, or insufficient training.
Continuous Monitoring and Testing
- Monitor for New Threats: Security is an ongoing process. After remediation, continuous monitoring is essential to detect new vulnerabilities that may arise. Regular scans and assessments help ensure that the system remains secure over time.
- Test Remediation Effectiveness: Once vulnerabilities are remediated, it is important to test whether the fixes are effective. This can include retesting systems and applications to verify that the weaknesses have been fully addressed and no new issues have been introduced.
- Document and Review Remediation Efforts: Keeping detailed records of remediation efforts helps track progress and provides valuable insight into how well security measures are functioning. Regular reviews of the remediation process allow for adjustments and improvements to be made as necessary.
By following these best practices, organizations can build a robust approach to remediation that not only fixes existing weaknesses but also strengthens their overall security posture, reducing the likelihood of future incidents.
How to Interpret Scan Results
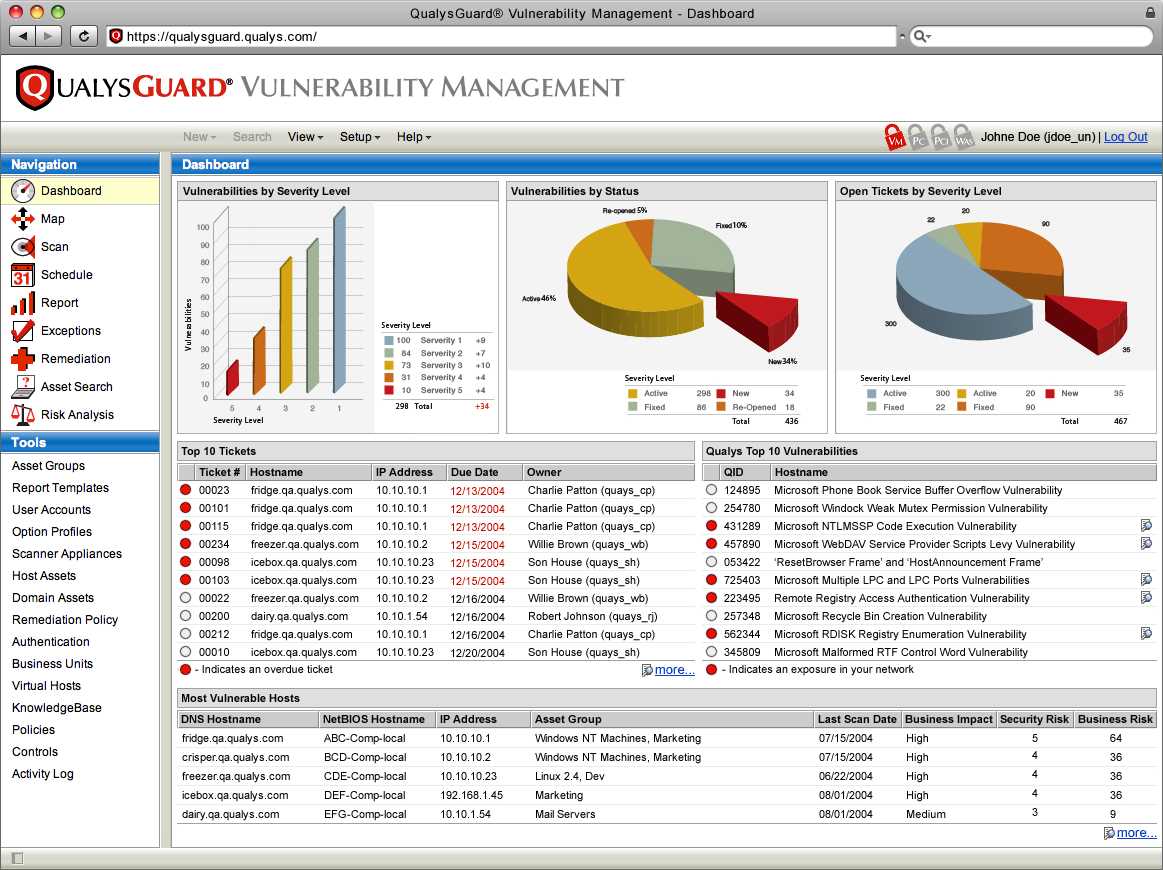
After performing a system scan to identify potential security risks, the results often need to be carefully analyzed to determine their significance and what actions should be taken. Properly interpreting scan results allows organizations to make informed decisions about which issues to address first, based on their potential impact and severity. In this section, we will discuss how to read and understand scan outputs, so you can respond effectively to any identified concerns.
When reviewing the results of a scan, several key elements should be considered: the severity of the identified issues, the specific assets affected, and any recommended actions. Understanding these factors will guide the remediation process and help ensure that security gaps are addressed appropriately.
Key Elements of Scan Results
- Severity Levels: Scan results typically categorize issues based on their severity. This can range from low to critical, depending on the potential impact of the issue. High-severity vulnerabilities often require immediate attention to prevent exploitation.
- Affected Systems: The scan will highlight which systems or components are impacted by the identified issues. This information is vital for prioritizing remediation efforts and ensuring that high-risk systems are addressed first.
- Recommendations: Scan results will usually include recommended actions to address the identified weaknesses. This may involve patching software, adjusting configurations, or implementing security controls to mitigate risk.
Reading Scan Output
| Field | Description |
|---|---|
| Issue Name | Identifies the nature of the detected weakness, such as missing patches or misconfigured settings. |
| Severity | Ranks the issue’s potential impact on the system, from low to critical. |
| Risk Score | A numerical value that represents the level of threat posed by the issue. |
| Solution/Recommendation | Outlines the steps that should be taken to remediate the issue. |
| Affected Systems | Lists the systems, servers, or applications that are impacted by the identified issues. |
Once the results have been reviewed, it’s important to prioritize remediation based on the severity and risk score. Critical issues that pose an immediate threat to the organization should be addressed first, while lower-severity issues can be mitigated later. Understanding how to interpret scan results is an essential skill for anyone involved in maintaining a secure environment.
Time Management Tips and Tricks
Effective time management is key to performing well in any timed assessment. Having a clear strategy for allocating time across different sections ensures that you can complete all questions without feeling rushed. By following certain techniques, you can enhance focus and increase the likelihood of answering every question accurately within the allotted time.
One of the most important aspects of managing time during an assessment is to prioritize tasks based on their difficulty and the points assigned. Understanding how much time to spend on each question, while maintaining a steady pace, helps avoid wasting time on more challenging questions at the expense of easier ones.
Strategic Planning Before the Test
- Review the Entire Test: At the beginning of the assessment, quickly scan all the sections and questions. This gives you a sense of the overall structure and allows you to identify which sections require more time and focus.
- Set Time Limits: Break down your time according to the number of questions and sections. For example, if you have 60 minutes and 50 questions, aim to spend no more than 1 minute per question.
- Start with Easy Questions: Begin with questions you are confident about to build momentum. This helps conserve time for more complex or time-consuming questions later on.
During the Test: Focus and Efficiency
- Stay on Track: Keep an eye on the clock and make sure you stick to the time limits you’ve set. If you’re stuck on a question, move on and come back to it later if needed.
- Answer What You Know First: For questions you find particularly challenging, answer any parts you can confidently address and mark the rest to review later.
- Avoid Overthinking: Trust your initial instincts and avoid spending too much time second-guessing yourself. If you’re unsure, choose the best possible answer based on your knowledge.
By planning ahead and staying disciplined during the test, you can maximize your chances of completing all questions effectively within the given time frame. Proper time management not only reduces stress but also ensures a more organized approach to the assessment.
Staying Up-to-Date with Key Features
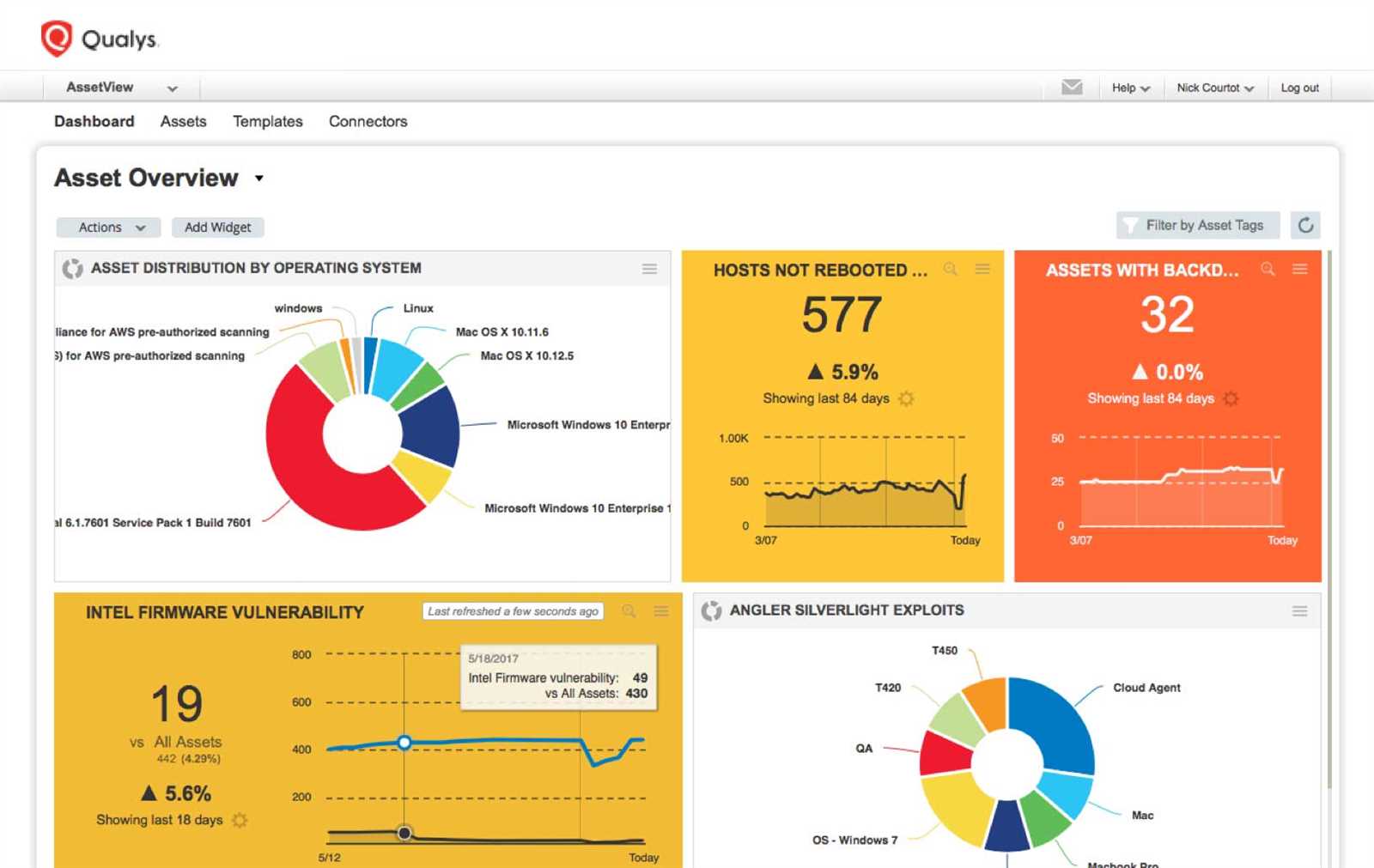
Keeping up with the latest tools and features in the field is essential for maintaining a competitive edge. As technology evolves rapidly, new functionalities and improvements are introduced frequently. Staying informed about these updates ensures you can fully leverage the available resources and optimize your approach for maximum efficiency.
Understanding the latest capabilities helps you adapt to changes, make informed decisions, and ensure you are using the most effective methods available. By staying updated, you can refine your skills, troubleshoot effectively, and streamline workflows, which is crucial for staying ahead in the industry.
How to Keep Current

- Follow Official Release Notes: Always check the release notes for updates and new features. These documents provide detailed information on changes and improvements.
- Join Online Communities: Participate in forums, webinars, and online groups related to your tools. This allows you to learn from others’ experiences and share insights.
- Attend Training Sessions: Many platforms offer continuous learning through webinars and tutorials. These sessions often cover new features and best practices, keeping you informed.
Practical Application of New Features

- Test New Tools: Whenever a new feature is released, take the time to experiment with it. Testing in a controlled environment ensures that you understand its capabilities and limitations.
- Integrate Updates into Workflows: Once you’re comfortable with new features, incorporate them into your daily tasks to improve your processes and increase productivity.
By actively engaging with the latest tools and features, you can enhance your effectiveness, troubleshoot more efficiently, and continue growing in your field.
Staying Up-to-Date with Key Features
Keeping up with the latest tools and features in the field is essential for maintaining a competitive edge. As technology evolves rapidly, new functionalities and improvements are introduced frequently. Staying informed about these updates ensures you can fully leverage the available resources and optimize your approach for maximum efficiency.
Understanding the latest capabilities helps you adapt to changes, make informed decisions, and ensure you are using the most effective methods available. By staying updated, you can refine your skills, troubleshoot effectively, and streamline workflows, which is crucial for staying ahead in the industry.
How to Keep Current
- Follow Official Release Notes: Always check the release notes for updates and new features. These documents provide detailed information on changes and improvements.
- Join Online Communities: Participate in forums, webinars, and online groups related to your tools. This allows you to learn from others’ experiences and share insights.
- Attend Training Sessions: Many platforms offer continuous learning through webinars and tutorials. These sessions often cover new features and best practices, keeping you informed.
Practical Application of New Features
- Test New Tools: Whenever a new feature is released, take the time to experiment with it. Testing in a controlled environment ensures that you understand its capabilities and limitations.
- Integrate Updates into Workflows: Once you’re comfortable with new features, incorporate them into your daily tasks to improve your processes and increase productivity.
By actively engaging with the latest tools and features, you can enhance your effectiveness, troubleshoot more efficiently, and continue growing in your field.