Vulnerability Detection and Response Certification Exam Answers

In today’s digital world, understanding how to identify and mitigate risks is essential for professionals in the cybersecurity field. The ability to recognize potential threats and effectively manage them is a key skill required for tackling modern security challenges. Mastering these concepts not only enhances one’s expertise but also prepares individuals for career advancement in security roles.
Preparation for these challenges requires both theoretical knowledge and practical experience. By engaging in specialized tests, individuals can assess their grasp of essential concepts, ensuring they are well-equipped to handle real-world security situations. Success in these areas reflects a comprehensive understanding of security management and a commitment to safeguarding systems and data.
Effective preparation demands a deep dive into the most common techniques, tools, and procedures used by experts. With the right approach, professionals can sharpen their skills, increase their confidence, and demonstrate their readiness to take on the complex issues facing modern IT environments.
Vulnerability Detection and Response Exam Answers
Mastering the skills needed to navigate real-world security challenges is crucial for anyone looking to advance in the field of cybersecurity. Whether you’re preparing for a professional assessment or seeking to deepen your knowledge, understanding key concepts is essential. This section will guide you through the most critical topics, offering insights into how to approach these challenges effectively.
Key Areas to Focus On
Successful preparation involves focusing on several core areas. It’s not just about theoretical knowledge; practical application of security principles plays a major role. Below are the key topics that should be prioritized during preparation:
- Threat Identification – Learn how to pinpoint potential risks in various environments.
- Mitigation Strategies – Understand how to apply appropriate countermeasures to minimize security breaches.
- Incident Management – Develop the skills to respond quickly and effectively to ongoing threats.
- Security Tools – Get familiar with the tools that professionals use to detect, analyze, and manage risks.
Practical Tips for Mastery
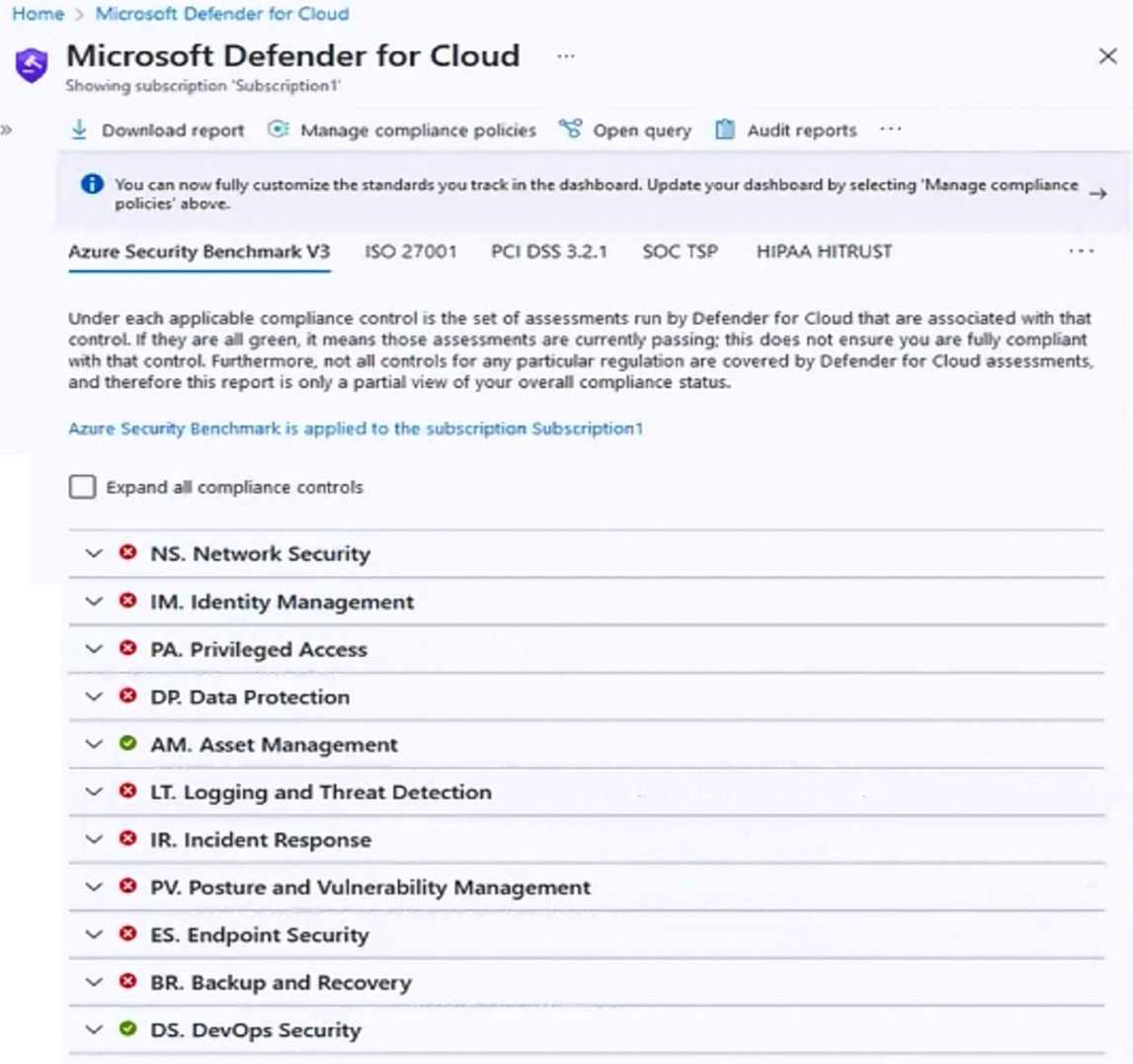
To truly master the subject matter, it’s important to engage with hands-on practice. Below are some tips to help enhance your understanding:
- Practice Real-World Scenarios: Simulate security challenges to strengthen your problem-solving skills.
- Use Lab Environments: Set up a virtual environment to experiment with various techniques without the risk of affecting live systems.
- Stay Updated: Continuously update your knowledge as cybersecurity is a constantly evolving field.
- Join Professional Communities: Engage with others in the field to share experiences and insights.
Focusing on these areas will ensure you’re well-prepared to tackle real-world security challenges, boosting both your confidence and expertise in the process.
Overview of Vulnerability Detection Certifications
Achieving professional recognition in the field of security requires a deep understanding of risk management, mitigation strategies, and effective threat handling. Specialized assessments are designed to test individuals on their ability to manage and safeguard digital environments against potential threats. These qualifications not only validate your expertise but also enhance career opportunities by demonstrating your proficiency in addressing security challenges.
Types of Professional Qualifications
There are several industry-recognized qualifications that focus on developing the skills needed for managing digital security risks. Below are some of the key certifications that professionals can pursue to advance their careers:
| Certification | Focus Area | Level |
|---|---|---|
| Certified Information Systems Security Professional (CISSP) | Comprehensive security principles and best practices | Advanced |
| Certified Ethical Hacker (CEH) | Penetration testing and ethical hacking techniques | Intermediate |
| CompTIA Security+ | Foundational knowledge in security concepts | Entry |
| Certified Information Security Manager (CISM) | Risk management and organizational security | Advanced |
Benefits of Pursuing Certifications
Obtaining these qualifications offers numerous advantages. They provide recognition of your skills, enhance your employability, and demonstrate your commitment to staying current in an ever-evolving field. Additionally, many certifications help professionals understand emerging security trends, enabling them to adapt and implement the latest solutions in digital defense.
Key Concepts in Response Procedures
Effective handling of security breaches involves more than just detecting threats. It requires a structured approach to mitigating risks, minimizing damage, and ensuring systems return to normal operation swiftly. A well-organized response plan is essential for professionals to maintain control during critical incidents, limit exposure, and restore security measures. Understanding the core principles behind these actions is key to mastering this aspect of cybersecurity.
Several fundamental concepts form the backbone of any effective crisis management strategy. These principles guide professionals in their efforts to neutralize risks and recover from security incidents. Below are some of the core elements that define a robust response procedure:
| Concept | Description |
|---|---|
| Incident Detection | Identifying and confirming the occurrence of a security breach or threat. |
| Impact Assessment | Evaluating the severity of the incident and its potential effects on systems and data. |
| Containment | Isolating affected systems to prevent the spread of the incident to other areas of the network. |
| Eradication | Removing the root cause of the incident and eliminating any malicious code or threats. |
| Recovery | Restoring systems to normal functionality and ensuring that no residual risks remain. |
| Post-Incident Analysis | Reviewing the incident to understand what happened, what went well, and what needs improvement in future responses. |
Mastering these concepts not only ensures that professionals can handle incidents effectively but also prepares them for managing future risks with confidence. A comprehensive understanding of these steps enhances one’s ability to react appropriately during a crisis, ultimately improving organizational security and resilience.
Importance of Vulnerability Detection Skills
The ability to identify weaknesses in digital systems is essential for maintaining robust security. Without the capability to spot potential threats before they are exploited, organizations risk severe damage, including data breaches, financial loss, and reputational harm. Developing the skills needed to pinpoint these threats is a critical aspect of cybersecurity, enabling professionals to prevent attacks and safeguard valuable resources.
Key Reasons for Developing These Skills
Strong detection capabilities play a vital role in creating proactive security measures. Below are the primary reasons why honing these skills is crucial for any security professional:
- Early Identification: Being able to identify risks before they cause harm helps prevent potential breaches from escalating.
- Enhanced Risk Management: Accurate threat identification allows for better resource allocation and focused mitigation efforts.
- Cost Reduction: Detecting issues early minimizes the need for expensive remediation or recovery after a major incident.
- Improved Security Posture: A proactive approach strengthens the overall defense of digital assets and builds trust with stakeholders.
Practical Benefits in Cybersecurity Careers

Mastering these skills not only strengthens an organization’s security infrastructure but also provides individuals with a competitive edge in the job market. Professionals with advanced detection abilities are highly valued by employers, as they can quickly address emerging threats, ensuring minimal disruption and damage. Additionally, these skills are essential for maintaining compliance with industry standards and regulations, which is increasingly critical in today’s regulatory landscape.
Preparation Tips for the Certification Exam

Achieving success in a professional assessment requires more than just theoretical knowledge. It’s important to build a solid understanding of the core principles and gain practical experience with real-world scenarios. By preparing thoroughly, you can enhance your problem-solving abilities and boost your confidence to tackle any challenge that may arise during the evaluation.
Effective Study Strategies
Adopting the right approach to studying is key to mastering the necessary skills. Here are some strategies to consider when preparing:
- Understand Core Concepts: Focus on grasping the fundamental principles that underpin the subject matter, as they form the basis for more advanced topics.
- Practice with Real-World Scenarios: Engage in simulations or labs to apply your knowledge in realistic settings, strengthening your problem-solving abilities.
- Break Down Study Sessions: Avoid cramming; instead, break down your study material into manageable sections and review them regularly to reinforce learning.
- Use Diverse Learning Resources: Complement textbooks with online tutorials, videos, and practice tests to gain a well-rounded understanding of the material.
Stay Focused and Confident
Maintaining focus and building confidence is crucial during the preparation process. Setting achievable goals and tracking progress will help keep you motivated. Additionally, ensure that you take breaks to avoid burnout and stay mentally sharp. The more consistently you study and practice, the more confident you will be on the day of the assessment.
Understanding the Exam Structure and Format
To succeed in any professional assessment, it’s essential to understand its structure and how questions are framed. Familiarizing yourself with the format allows you to tailor your preparation effectively, ensuring that you are well-prepared for the various sections and types of questions. Knowing what to expect can significantly reduce anxiety and improve your performance during the test.
Overview of the Test Format
The structure of the evaluation typically consists of several key sections, each designed to assess different aspects of your skills. Below is an outline of the main components you can expect:
- Multiple-Choice Questions: These questions test your knowledge of theoretical concepts and best practices in the field.
- Scenario-Based Questions: You will be presented with real-world scenarios to evaluate your problem-solving and decision-making abilities.
- Practical Tasks: Some assessments include hands-on activities that simulate actual tasks to assess your practical skills.
- Time Limit: Most tests have a time constraint, so managing your time efficiently during the test is crucial.
Preparing for Each Section
Each part of the evaluation requires a different preparation strategy. For multiple-choice questions, focus on memorizing key facts and principles. For scenario-based questions, practice applying your knowledge to solve problems in realistic contexts. When dealing with practical tasks, set up test environments to practice technical skills. Understanding these different formats will help you prioritize your preparation efforts and approach the assessment with confidence.
Common Questions on Vulnerability Detection
When preparing for a professional assessment in the field of security, it’s essential to understand the most frequently asked questions. These queries often cover critical concepts, methodologies, and practical scenarios related to identifying and addressing risks in digital systems. By reviewing common questions, you can gain deeper insights into the subject matter and better anticipate what may come up in the test.
Here are some typical questions that candidates may encounter:
- What are the most common types of security weaknesses? Understanding the different categories of flaws, such as configuration errors or outdated software, is crucial for effective risk management.
- How can organizations prioritize risks? This involves assessing the potential impact and likelihood of different threats to ensure that resources are allocated effectively.
- What tools are used for identifying potential weaknesses? Knowing the various tools available for scanning systems, such as vulnerability scanners, is important for efficient threat detection.
- What are the best practices for patch management? Keeping systems updated is one of the most effective ways to prevent exploitation of known weaknesses.
- How should vulnerabilities be documented and tracked? Proper record-keeping is essential for ongoing risk management and ensures that no issues are overlooked during remediation.
By understanding these typical questions, candidates can ensure they have a strong grasp of essential concepts, better equipping themselves for the challenges ahead.
Effective Strategies for Passing the Exam
Achieving success in a professional evaluation requires more than just understanding the material; it involves strategic preparation and smart techniques during the test itself. By following effective strategies, candidates can enhance their chances of performing well, manage their time efficiently, and minimize stress. A well-thought-out approach is key to navigating through the various components of the assessment with confidence and accuracy.
Key Preparation Techniques
Proper preparation is the first step in setting yourself up for success. Below are some strategies to help you focus your efforts:
- Master Core Principles: Ensure you fully understand the foundational concepts, as these will be the basis for many questions.
- Review Practical Scenarios: Many assessments test your ability to apply knowledge to real-world situations. Practice with scenarios to improve your problem-solving skills.
- Use Practice Tests: Taking practice tests under timed conditions helps you become familiar with the format and identify areas for improvement.
- Set a Study Schedule: Break your study sessions into focused intervals, allowing for regular review and reducing burnout.
Test-Taking Tips
Once you’ve prepared, it’s important to know how to approach the actual test. Here are some tips to help you perform at your best:
| Strategy | Benefit |
|---|---|
| Read Instructions Carefully | Ensure you understand the requirements for each section to avoid unnecessary mistakes. |
| Manage Time Wisely | Allocate sufficient time for each question, ensuring you don’t rush through critical sections. |
| Stay Calm Under Pressure | Maintain focus even if you encounter difficult questions; it’s better to skip and return later. |
| Double-Check Your Work | Revisit your answers if time allows, especially for multiple-choice or scenario-based questions. |
By adopting these strategies, you will be well-prepared to tackle the evaluation with clarity and confidence, ensuring the best possible outcome.
How to Study for Response Scenarios

To excel in scenarios where you need to apply your knowledge to real-world situations, it’s crucial to approach your preparation with a strategic mindset. These types of challenges often require you to think critically, assess risks, and make decisions under pressure. The ability to navigate complex situations with a clear, methodical approach is key to performing well.
Focus on Practical Application
While theoretical knowledge is important, being able to apply what you’ve learned in realistic situations is what will truly set you apart. Here are some ways to enhance your skills:
- Understand Common Situations: Familiarize yourself with the most common types of issues that might arise in professional environments. These could include security breaches, system misconfigurations, or software vulnerabilities.
- Practice Problem-Solving: Engage in case studies or simulations to sharpen your ability to assess a situation and determine the best course of action.
- Analyze Past Scenarios: Look at historical examples of security incidents or technical failures. Understanding how they were handled can provide valuable insights into best practices and common pitfalls.
Build Your Decision-Making Framework
In high-pressure situations, being able to make decisions quickly and accurately is essential. To build this skill:
- Develop a Step-by-Step Approach: Break down each situation into manageable steps. Identify what information you need, assess the risks, and prioritize actions.
- Review Best Practices: Study the most effective methodologies for managing complex scenarios. Knowing standard procedures will help you act decisively when needed.
- Simulate Real-Life Scenarios: Use tools and practice platforms to simulate emergency situations. This will help you react under pressure and refine your decision-making abilities.
By focusing on practical applications and honing your decision-making skills, you will be better equipped to tackle response scenarios with confidence and accuracy.
Tools Used in Vulnerability Detection
In the realm of cybersecurity, identifying weaknesses in systems and applications is essential to safeguarding networks and data. Various tools are designed to automate and streamline this process, helping professionals quickly spot potential risks. These tools allow users to scan, analyze, and mitigate issues before they can be exploited. The proper selection of tools can significantly enhance the efficiency of any security team, ensuring faster identification and resolution of threats.
Below are some commonly used tools in the field:
- Nessus: A widely-used tool for vulnerability scanning that helps security professionals detect configuration errors, missing patches, and other security flaws in both network devices and applications.
- OpenVAS: An open-source tool for assessing the security of systems, providing comprehensive scans and reporting on vulnerabilities within network infrastructures.
- Qualys: A cloud-based platform offering continuous vulnerability management and policy compliance, known for its ability to track and remediate risks across a wide array of environments.
- Burp Suite: A popular tool for web application security testing, providing a wide range of capabilities from manual testing to automated vulnerability scanning.
- Metasploit: Primarily used for penetration testing, Metasploit allows security professionals to identify weaknesses by simulating attacks on systems and assessing their defenses.
These tools are vital for effective risk management, allowing cybersecurity experts to proactively assess, detect, and address potential threats across a range of environments.
Handling Real-World Threats in the Exam
In many assessments designed to test practical skills, real-world scenarios are often used to evaluate a candidate’s ability to respond to actual threats. These situations may involve simulated attacks, system breaches, or other security challenges that professionals face in their day-to-day roles. Preparing for such scenarios requires a combination of theoretical knowledge and hands-on experience, allowing candidates to make decisions under pressure and apply their expertise effectively.
Key Strategies for Tackling Real-World Scenarios
To perform well when confronted with these types of challenges, it’s important to follow a structured approach. Here are some strategies to consider:
- Prioritize Issues: In a simulated threat, it’s essential to identify which issues need immediate attention. Focus on critical vulnerabilities first to mitigate any potential damage.
- Analyze the Situation: Take time to evaluate the scope of the threat, gather as much information as possible, and assess the potential impact. Understanding the full context will lead to better decision-making.
- Implement Mitigation Measures: Once the most pressing issues are identified, take immediate action to mitigate the risks. This could include patching systems, isolating infected machines, or blocking malicious traffic.
- Communicate Clearly: In a real-world scenario, effective communication is key. Ensure that all stakeholders are informed of the situation and any actions being taken.
- Document Your Actions: Proper documentation is essential for future analysis and for fulfilling regulatory requirements. Keep track of what steps were taken and any changes made during the incident.
Practice with Simulated Scenarios
Hands-on experience is one of the best ways to prepare for handling threats in real-time. Simulations and practice scenarios help you hone your skills, understand common attack vectors, and improve your response time. Many platforms offer training environments where you can test your knowledge in a safe, controlled setting.
By adopting these strategies and engaging in practice exercises, you will be well-equipped to handle real-world challenges effectively, whether in a professional setting or during an assessment designed to test your abilities.
Best Resources for Exam Preparation
Preparing for an assessment focused on cybersecurity skills requires access to high-quality resources that help sharpen your knowledge and practical abilities. With the increasing number of tools and concepts involved, having the right materials can make a significant difference in your success. These resources can range from books and online courses to hands-on labs and practice tests that simulate real-world situations.
Top Study Materials to Consider
Here are some valuable resources that can assist you in your preparation journey:
- Official Training Materials: Most vendors offer official study guides and materials that directly align with the content covered in assessments. These are a great starting point for structured learning.
- Online Courses: Platforms such as Coursera, Udemy, and LinkedIn Learning offer in-depth courses on relevant topics, taught by experts in the field. These courses often include video tutorials, quizzes, and practical labs.
- Books: Books focused on network security, incident management, and risk analysis provide a solid theoretical foundation. Look for books that offer practice questions at the end of chapters to reinforce learning.
- Practice Tests: Taking practice tests is one of the best ways to prepare for any challenge. Many websites offer simulated tests that mirror the actual assessment, helping you get comfortable with the format and timing.
- Interactive Labs: Hands-on labs, like those provided by platforms such as Hack The Box or TryHackMe, allow you to apply what you’ve learned in realistic environments, enhancing your practical skills.
Additional Helpful Resources
To supplement your study, consider these tools and strategies:
- Online Communities: Joining forums or online groups such as Reddit’s cybersecurity threads or Stack Overflow allows you to engage with peers, share experiences, and get advice on tricky topics.
- Webinars and Workshops: Attend live events or workshops hosted by security organizations or experts. These events often offer valuable insights into the latest trends and challenges in the industry.
- Blogs and Research Papers: Follow reputable cybersecurity blogs and read research papers to stay updated on the latest security threats and defensive strategies.
Utilizing these resources will ensure a well-rounded preparation plan, equipping you with both the theoretical knowledge and practical experience needed to excel in the assessment.
Key Differences Between Detection and Response
When it comes to managing security events, there are two crucial stages that professionals focus on: identifying threats and managing their aftermath. While these stages are interconnected, they each serve distinct roles within the cybersecurity framework. Understanding the differences between these two areas is essential for creating an effective strategy for addressing security risks.
Identification vs. Mitigation
The first major distinction lies in the purpose of each process. Identification involves recognizing potential risks or breaches in real time, allowing security professionals to spot unusual activity that may indicate a threat. This phase is about gathering insights, monitoring for anomalies, and pinpointing any system irregularities that may signify an attack.
On the other hand, mitigation focuses on taking immediate action to neutralize or limit the impact of the identified issue. This stage involves applying strategies, such as isolating affected systems, implementing fixes, or strengthening security measures to prevent further damage.
Tools and Techniques Used
Each phase also relies on different sets of tools and techniques to achieve its objectives. The identification phase often utilizes advanced monitoring systems, scanning tools, and analytical methods to detect irregularities. These tools are designed to provide real-time alerts that enable professionals to respond swiftly.
For mitigation, response teams use a broader range of techniques, including incident containment, patching vulnerabilities, updating security configurations, and conducting post-event analysis to ensure that the same threat doesn’t reoccur.
While both stages play a pivotal role in maintaining cybersecurity, understanding their differences helps ensure that each phase is handled by the right tools and expertise, ultimately contributing to a more robust defense system.
Assessing Your Readiness for the Test
Preparing for a challenging evaluation requires careful reflection on your knowledge, skills, and familiarity with the required concepts. Before you step into the actual assessment, it is crucial to evaluate your current level of preparedness to identify any gaps in your understanding. This self-assessment allows you to focus on areas that need further attention, ensuring that you approach the test with confidence.
Start by reviewing the core topics and ensuring you understand the main concepts thoroughly. It’s important to be comfortable with both theoretical knowledge and practical applications. Test your understanding by attempting practice questions, simulating real test conditions to gauge how well you can apply your knowledge under pressure.
Additionally, consider timing yourself during practice sessions to assess how efficiently you can manage your time during the real evaluation. This is essential to ensure you can complete all sections within the given time frame without feeling rushed.
Finally, seek feedback from peers or mentors who have already undergone the process. They can provide insights into areas you may have overlooked or offer tips on approaching difficult questions. By thoroughly assessing your readiness, you increase your chances of success and reduce any potential surprises during the actual assessment.
Frequently Asked Questions About the Exam
When preparing for a complex evaluation, it’s natural to have questions about the process, structure, and expectations. Understanding the key details beforehand can help alleviate any confusion and improve your overall readiness. Here are some of the most common inquiries from those preparing for the assessment.
What Topics Will Be Covered?
The content of the assessment typically spans a wide range of subjects related to system security, risk management, incident handling, and various technical practices. You will be tested on both theoretical knowledge and practical applications in real-world scenarios.
How Should I Prepare Effectively?
Effective preparation involves reviewing key concepts, studying practice materials, and familiarizing yourself with tools used in the industry. Taking practice tests is also an excellent way to assess your current understanding and identify areas that need improvement.
Is There a Time Limit?
Yes, there is usually a time limit during the evaluation. You will need to manage your time wisely to ensure that you can complete all sections without rushing. Timing yourself during practice tests can help you get used to the pace.
How Many Questions Will Be on the Test?
The number of questions may vary depending on the assessment format, but typically, you can expect a mixture of multiple-choice questions, scenario-based questions, and practical tasks. Be sure to check the guidelines provided before the assessment.
What Happens If I Don’t Pass?
If you don’t pass the assessment, most programs allow you to retake it after a specified period. Use the feedback from the first attempt to focus your study efforts on areas where you may have struggled.
By understanding the format and expectations, you can approach the evaluation with confidence, knowing what to expect and how best to prepare.
How to Stay Updated on Security Threats
Keeping up with the latest threats is crucial for anyone involved in cybersecurity. The landscape of risks is constantly evolving, and staying informed is key to defending against emerging challenges. Whether you’re an IT professional, a security analyst, or just someone interested in keeping their systems secure, there are several ways to stay on top of new developments.
Subscribe to Industry News and Alerts
One of the best ways to stay informed is by subscribing to reputable security news websites and alert services. Many organizations provide regular updates on the latest threats, vulnerabilities, and best practices for mitigating risks. Some useful resources include:
- US-CERT – The United States Computer Emergency Readiness Team provides alerts and updates on cybersecurity threats.
- CVE Details – A comprehensive database of publicly known cybersecurity vulnerabilities.
- Security Week – A site offering in-depth analysis of recent security events and trends.
Participate in Security Forums and Communities
Engaging with the cybersecurity community is another valuable way to stay updated. Online forums, discussion boards, and communities like Reddit’s /r/netsec or Stack Exchange’s Information Security section are excellent places to share knowledge, ask questions, and learn from experienced professionals. Many cybersecurity experts and organizations actively participate in these communities, offering insights into the latest trends and threats.
By using these methods, you can ensure that you’re always aware of the latest threats and vulnerabilities, allowing you to take proactive steps in securing your systems.
Tips for Post-Exam Success and Career Growth
Successfully completing a professional assessment is just the beginning of your journey in the cybersecurity field. Once you’ve passed, it’s important to focus on continuing your development, enhancing your skills, and leveraging your knowledge for career advancement. This section provides actionable steps you can take to further your success after the assessment.
1. Leverage Your New Knowledge
After completing an assessment, it’s essential to reinforce what you’ve learned by applying it in real-world scenarios. Hands-on practice is one of the most effective ways to solidify concepts and improve problem-solving skills. Here are a few ways to do that:
- Participate in Capture the Flag (CTF) challenges – These competitions help you refine your skills in a simulated environment.
- Volunteer for open-source security projects – Contributing to real projects allows you to gain practical experience while giving back to the community.
- Set up your own test environments – Experimenting with different tools, techniques, and strategies can boost your confidence and competence.
2. Expand Your Network

Networking is a key component of career growth. Connecting with others in the cybersecurity field can open up new opportunities for collaboration, mentorship, and job offers. Consider these strategies:
- Attend industry conferences and webinars – These events provide great opportunities to meet experts, share knowledge, and stay updated on trends.
- Join professional organizations – Groups like (ISC)², ISACA, or local security meetups can provide a sense of community and additional learning resources.
- Seek a mentor – Find someone with more experience who can guide your career and help you navigate challenges.
3. Keep Your Skills Current
Cybersecurity is a rapidly evolving field, so continuous learning is crucial. Stay ahead of the curve by regularly updating your skills and staying informed about new threats, technologies, and best practices. Some tips for ongoing education include:
- Take advanced courses – Explore more in-depth topics or specialized areas such as penetration testing or threat intelligence.
- Earn additional credentials – Look for other industry-recognized credentials to further boost your resume.
- Subscribe to security blogs and podcasts – Regularly read or listen to the latest discussions on new vulnerabilities and mitigation techniques.
By following these steps, you can ensure long-term career success and growth in the cybersecurity industry, while continually advancing your skills and knowledge.