Ndg Linux Essentials 2.0 Chapter 4 Exam Answers

In this section, we explore fundamental topics crucial for anyone pursuing a career in system management. By focusing on essential principles, users gain a deeper understanding of how to efficiently manage, secure, and navigate various operating systems.
The material covers various practical techniques, ensuring that administrators can confidently apply their knowledge in real-world environments. Emphasis is placed on effective command usage, file management, and user control, which form the backbone of system administration tasks.
Through targeted exercises and theoretical insights, readers will strengthen their technical capabilities and gain a clearer perspective on the challenges faced by professionals in this field. Prepare yourself for practical applications and deepen your expertise in maintaining smooth-running systems.
System Administration Certification Guide
This section provides a comprehensive overview of the key topics you need to master in order to succeed in the related certification. By focusing on practical skills, the guide helps you develop the necessary knowledge and techniques to navigate common system tasks efficiently.
Whether you’re preparing for your first certification or enhancing your expertise, this guide will walk you through essential concepts, command-line tools, file systems, and user management. Each topic is designed to build your understanding and boost your confidence in handling real-world challenges.
Core Topics Covered
- Understanding file permissions and access controls
- Managing users and groups effectively
- File system organization and structure
- Command-line proficiency and navigation
- Basic troubleshooting techniques for system problems
Study Tips and Resources
To maximize your chances of success, focus on mastering the following areas:
- Practice using command-line tools in different scenarios.
- Review file permission commands and understand their impact.
- Simulate user and group management tasks in a controlled environment.
- Familiarize yourself with file system layouts and structures.
Incorporating these practices into your study routine will ensure you’re well-prepared for the related certification challenge.
System Administration Certification Guide
This section provides a comprehensive overview of the key topics you need to master in order to succeed in the related certification. By focusing on practical skills, the guide helps you develop the necessary knowledge and techniques to navigate common system tasks efficiently.
Whether you’re preparing for your first certification or enhancing your expertise, this guide will walk you through essential concepts, command-line tools, file systems, and user management. Each topic is designed to build your understanding and boost your confidence in handling real-world challenges.
Core Topics Covered
- Understanding file permissions and access controls
- Managing users and groups effectively
- File system organization and structure
- Command-line proficiency and navigation
- Basic troubleshooting techniques for system problems
Study Tips and Resources
To maximize your chances of success, focus on mastering the following areas:
- Practice using command-line tools in different scenarios.
- Review file permission commands and understand their impact.
- Simulate user and group management tasks in a controlled environment.
- Familiarize yourself with file system layouts and structures.
Incorporating these practices into your study routine will ensure you’re well-prepared for the related certification challenge.
Key Concepts in Chapter 4 Exam
This section highlights the fundamental ideas that are crucial for understanding and mastering system administration tasks. It focuses on essential principles related to file management, user access, and system organization, all of which are critical for successful administration.
The concepts covered here will help you gain a deep understanding of how to handle and troubleshoot common system tasks, and will prepare you for the practical aspects of managing users, permissions, and files in an operating environment.
Critical Areas to Focus On
- File permissions and their importance in securing system data
- How to manage users and groups, and control access rights
- The layout and structure of the file system and directories
- Effective use of the command line for system tasks
- Techniques for troubleshooting common system issues
Preparation Tips for Mastering Key Concepts
- Practice setting and modifying file permissions through commands like chmod and chown.
- Familiarize yourself with system commands for managing users and groups, such as useradd and groupadd.
- Review directory structures and understand how files are organized within the system.
- Simulate troubleshooting scenarios to strengthen your problem-solving abilities.
By focusing on these concepts, you’ll be equipped with the knowledge needed to handle system management tasks effectively and confidently.
Understanding File Permissions
File permissions are an essential aspect of managing and securing an operating system. They determine who can access, modify, and execute files, ensuring that only authorized users can perform certain actions. Properly configuring permissions is crucial for maintaining system integrity and protecting sensitive data.
In most systems, permissions are divided into three categories: read, write, and execute. These permissions can be applied to three types of users: the owner of the file, the group associated with the file, and all others. Understanding how to assign and manage these permissions is fundamental for both system administrators and regular users.
Commands like chmod, chown, and chgrp are commonly used to manipulate file permissions. Knowing how to use these commands effectively allows users to control access at a granular level, ensuring that files are kept secure and properly managed.
Common Questions Explained
In this section, we’ll break down some of the most frequently asked questions related to system administration tasks. These questions cover key concepts and practical skills that are essential for anyone looking to manage and troubleshoot systems effectively. Understanding these concepts will not only help in preparation but also enhance overall technical competence.
Each question is designed to test your knowledge of critical tasks, from managing file access to understanding system structures. By reviewing these questions and their explanations, you can gain deeper insights into how systems operate and how to solve common administrative challenges efficiently.
For example, questions often focus on topics such as managing user permissions, configuring file systems, or using command-line tools. It’s important to understand both the theoretical principles and practical applications to perform well in these areas.
File System Structure
Understanding the layout and organization of a file system is crucial for system management. The file system determines how data is stored, accessed, and managed on a computer. It is essential for administrators to know the structure in order to navigate directories, manage storage, and efficiently locate files.
In most operating systems, the file system is organized hierarchically, with a single root directory at the top. Below this root, files and directories are arranged in a tree-like structure. This arrangement allows for efficient data retrieval and access control, as well as ensuring that files are stored logically and securely.
Key Directories in the File System
- / – The root directory, the starting point of the file system.
- /home – Contains personal directories for users.
- /etc – Stores system configuration files.
- /bin – Houses essential system binaries and executable files.
- /var – Holds variable data like logs, databases, and application files.
Important Concepts for File Management
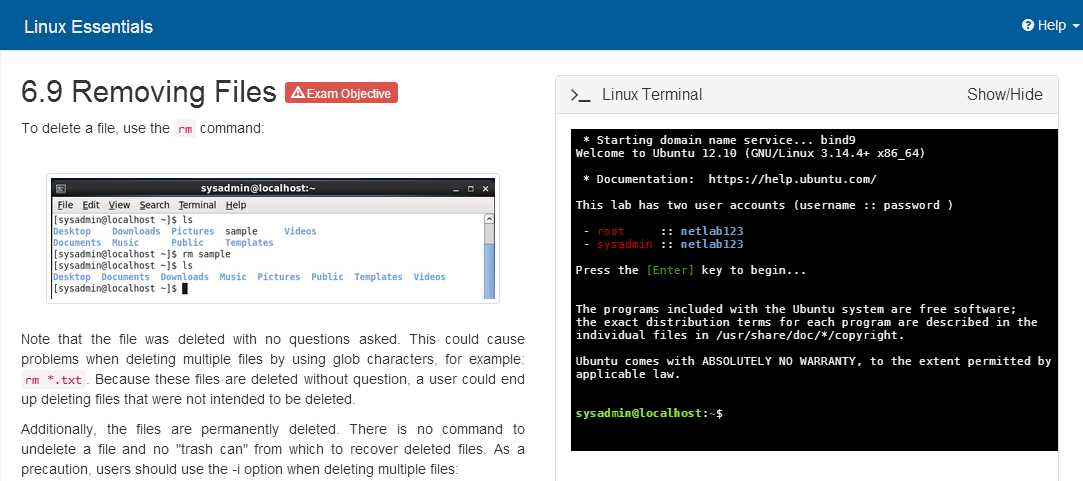
- Mounting – The process of attaching storage devices or file systems to the main system directory.
- File Paths – The exact location of a file within the file system hierarchy, either absolute or relative.
- File Types – Identifying files as regular files, directories, or special files (e.g., symbolic links or device files).
Understanding the structure and key components of the file system helps users manage data, secure the system, and troubleshoot effectively. It’s crucial to practice navigating the system and using commands to manipulate files and directories efficiently.
Importance of File Ownership
File ownership plays a critical role in managing access and security within a system. It determines who can read, modify, or execute a file, helping to control user privileges and protect sensitive data. Proper ownership ensures that files are only accessed or altered by authorized individuals, reducing the risk of unauthorized changes or data breaches.
Understanding how ownership works is essential for system administrators. Each file or directory typically has an owner and a group associated with it. The owner is the user who has primary control over the file, while the group defines the set of users who share access rights. File ownership is a core element in setting up access controls and permissions within an operating system.
How Ownership Affects File Permissions
When a file is created, it is assigned to a specific user and group. The user (owner) can set permissions for themselves, the group, and others. These permissions define whether a file can be read, written, or executed. By assigning proper ownership and configuring permissions appropriately, system administrators ensure the correct level of access is granted.
Managing Ownership
System administrators can change file ownership using commands like chown and chgrp. The chown command allows the user to assign a new owner to a file, while chgrp lets them change the associated group. Properly managing file ownership helps maintain system security and prevents unauthorized access to critical files.
Setting File Permissions and Attributes
Configuring file permissions and attributes is a fundamental task in system administration, as it ensures proper access control and file protection. By assigning specific permissions to users and groups, you can control who can read, modify, or execute files. Additionally, attributes can be set to modify how files are handled by the system, including whether they are immutable or can be modified by certain users.
Understanding the difference between permissions and attributes is essential for managing files securely. Permissions govern who can interact with the file, while attributes provide advanced control over its behavior. Both need to be carefully set to protect system data and maintain proper security practices.
File Permissions Overview
File permissions are typically defined for three categories: the file owner, the group, and others. These permissions include the ability to read, write, or execute a file. The table below shows the different types of permissions:
| Permission | Symbol | Numerical Value | Description |
|---|---|---|---|
| Read | r | 4 | Allows viewing the content of the file |
| Write | w | 2 | Allows modifying the file |
| Execute | x | 1 | Allows running the file as a program |
File Attributes and Modifications
In addition to basic permissions, file attributes provide more advanced settings. These attributes can make a file immutable, append-only, or prevent access by certain users. Commonly used attributes include:
- i (immutable) – Prevents the file from being modified or deleted.
- a (append-only) – Allows data to be added to the file but prevents modifications to the existing content.
- e (extent format) – Specifies the file is using extended attributes for metadata storage.
These attributes are typically set using the chattr command, offering additional layers of security and control over how files are handled by the system.
Linux User and Group Management
Managing users and groups is a fundamental aspect of system administration. It involves creating, modifying, and deleting user accounts, as well as organizing users into groups for easier permission management. Proper user and group management ensures that only authorized individuals can access certain resources and that different types of data are protected according to specific access policies.
By setting up users and assigning them to appropriate groups, administrators can enforce security policies that limit or grant access to files, directories, and system resources. Groups are particularly useful in scenarios where a set of users requires the same access level to particular resources, making it easier to manage permissions without configuring each user individually.
Creating and Managing Users
Creating a new user involves assigning a unique username, a home directory, and specific shell preferences. The useradd command is commonly used for this purpose. In addition to basic user creation, system administrators must also ensure that each user is given appropriate access rights.
- useradd – Command to create a new user account.
- passwd – Command to set or change a user’s password.
- usermod – Used to modify user attributes, such as changing the home directory or user group.
Creating and Managing Groups
Groups help organize users based on access needs. Instead of modifying permissions for each user individually, groups allow administrators to assign the same set of permissions to multiple users at once. The groupadd command is used to create a new group, and users can be added to groups using usermod or gpasswd.
- groupadd – Command to create a new group.
- groupdel – Command to delete a group.
- gpasswd – Allows management of group passwords.
By organizing users into groups and setting appropriate permissions for each group, administrators ensure that access control is more efficient, reducing the potential for security breaches.
Essential Linux Commands for Exam
Understanding key commands is crucial for success when working with command-line interfaces. These commands form the foundation for interacting with the system, managing files, users, and system resources. Whether you’re navigating directories, manipulating files, or configuring system settings, mastering these essential commands is necessary for efficient management and troubleshooting.
In any technical evaluation or real-world scenario, the ability to quickly and accurately execute commands can make a significant difference. This section covers some of the most commonly used commands that every system administrator or user should be familiar with.
File Management Commands
File management is at the core of many tasks, and the following commands are essential for creating, viewing, and modifying files:
- ls – Lists the contents of a directory. Use options like -l for detailed information or -a to include hidden files.
- cp – Copies files or directories from one location to another.
- mv – Moves or renames files and directories.
- rm – Removes files or directories. Be cautious with -r for recursive deletion.
- touch – Creates an empty file or updates the timestamp of an existing file.
System Information Commands
Knowing how to gather system information is critical for troubleshooting and maintaining system health. These commands help you monitor resources and gather insights:
- top – Displays a dynamic view of system processes and resource usage.
- df – Shows the disk space usage of mounted filesystems.
- free – Displays information about system memory usage.
- uname – Provides information about the system’s kernel and architecture.
- uptime – Shows how long the system has been running and system load averages.
Network Commands
Network-related commands are vital for diagnosing connectivity issues and managing network configurations:
- ping – Tests the connectivity between the local system and a remote host.
- ifconfig – Displays or configures network interface parameters (often replaced by ip in newer systems).
- netstat – Displays network connections, routing tables, and interface statistics.
- traceroute – Tracks the route packets take to reach a remote destination.
Mastering these fundamental commands will help streamline tasks and enhance your ability to manage a system effectively, whether in practice or during an assessment.
How to Troubleshoot Linux Systems
Troubleshooting is a critical skill when managing any computing environment. Identifying and resolving issues efficiently ensures the system runs smoothly and minimizes downtime. When problems arise, it’s essential to follow a systematic approach, use the right tools, and interpret system messages accurately to diagnose and fix errors.
To troubleshoot effectively, one needs to understand the basic components and services of the system, as well as how to gather useful information. This section will guide you through some essential steps and techniques to diagnose and resolve common problems in a structured manner.
Step-by-Step Troubleshooting Process
When faced with an issue, follow these general steps to identify and address the problem:
- Identify the problem: Clearly define the issue. Is the system unresponsive, or is a specific application or service failing?
- Gather information: Check logs, system status, and error messages to gather as much information as possible. Useful log files include /var/log/syslog and /var/log/messages.
- Replicate the issue: Try to replicate the problem in a controlled environment. This helps in understanding whether the issue is persistent or intermittent.
- Isolate the cause: Narrow down the root cause by systematically eliminating potential sources of the issue. Start by checking hardware, then move to software configurations.
- Resolve the issue: Once the cause is identified, apply the necessary fix. This could involve reconfiguring settings, reinstalling software, or performing updates.
- Test the system: After making changes, test the system to ensure the issue is resolved and the system operates as expected.
Common Tools for Troubleshooting
Several tools and commands can help with system diagnostics and troubleshooting:
- dmesg – Displays kernel-related messages that can help identify hardware issues or driver problems.
- journalctl – Allows you to view system logs on systems using systemd, which can provide valuable information about system services and errors.
- top – Monitors system processes and resource usage, which is useful when troubleshooting performance-related issues.
- ps – Lists running processes. Use this to identify and manage processes that may be consuming excessive resources.
- netstat – Helps identify network connections and troubleshoot network-related problems.
- strace – Traces system calls made by programs, useful for debugging applications that are malfunctioning.
Common Troubleshooting Scenarios
Here are a few common issues you might encounter and how to troubleshoot them:
- System not booting: Check the boot sequence, verify the boot loader and disk partitions, and review logs for disk or filesystem errors.
- Slow system performance: Use commands like top or iotop to identify resource hogs and optimize the system for better performance.
- Service not starting: Check the service status with systemctl, review log files, and ensure necessary dependencies are installed and configured correctly.
- Network connectivity issues: Use ping and traceroute to identify network problems and check network configurations.
By following these troubleshooting steps and using the appropriate tools, you can efficiently diagnose and resolve most issues in a timely manner, ensuring the system operates smoothly.
How to Troubleshoot Linux Systems
Troubleshooting is a critical skill when managing any computing environment. Identifying and resolving issues efficiently ensures the system runs smoothly and minimizes downtime. When problems arise, it’s essential to follow a systematic approach, use the right tools, and interpret system messages accurately to diagnose and fix errors.
To troubleshoot effectively, one needs to understand the basic components and services of the system, as well as how to gather useful information. This section will guide you through some essential steps and techniques to diagnose and resolve common problems in a structured manner.
Step-by-Step Troubleshooting Process
When faced with an issue, follow these general steps to identify and address the problem:
- Identify the problem: Clearly define the issue. Is the system unresponsive, or is a specific application or service failing?
- Gather information: Check logs, system status, and error messages to gather as much information as possible. Useful log files include /var/log/syslog and /var/log/messages.
- Replicate the issue: Try to replicate the problem in a controlled environment. This helps in understanding whether the issue is persistent or intermittent.
- Isolate the cause: Narrow down the root cause by systematically eliminating potential sources of the issue. Start by checking hardware, then move to software configurations.
- Resolve the issue: Once the cause is identified, apply the necessary fix. This could involve reconfiguring settings, reinstalling software, or performing updates.
- Test the system: After making changes, test the system to ensure the issue is resolved and the system operates as expected.
Common Tools for Troubleshooting
Several tools and commands can help with system diagnostics and troubleshooting:
- dmesg – Displays kernel-related messages that can help identify hardware issues or driver problems.
- journalctl – Allows you to view system logs on systems using systemd, which can provide valuable information about system services and errors.
- top – Monitors system processes and resource usage, which is useful when troubleshooting performance-related issues.
- ps – Lists running processes. Use this to identify and manage processes that may be consuming excessive resources.
- netstat – Helps identify network connections and troubleshoot network-related problems.
- strace – Traces system calls made by programs, useful for debugging applications that are malfunctioning.
Common Troubleshooting Scenarios
Here are a few common issues you might encounter and how to troubleshoot them:
- System not booting: Check the boot sequence, verify the boot loader and disk partitions, and review logs for disk or filesystem errors.
- Slow system performance: Use commands like top or iotop to identify resource hogs and optimize the system for better performance.
- Service not starting: Check the service status with systemctl, review log files, and ensure necessary dependencies are installed and configured correctly.
- Network connectivity issues: Use ping and traceroute to identify network problems and check network configurations.
By following these troubleshooting steps and using the appropriate tools, you can efficiently diagnose and resolve most issues in a timely manner, ensuring the system operates smoothly.
Best Practices for System Administration
System administrators play a crucial role in maintaining the stability, security, and performance of an organization’s infrastructure. Following industry-recognized best practices is essential to ensure systems are managed efficiently and issues are minimized. These practices are designed to enhance the reliability of services, streamline daily tasks, and prevent long-term problems. By adhering to proven strategies, administrators can ensure that systems remain secure, scalable, and resilient.
The following are some of the most important best practices that every system administrator should follow in order to optimize system management and mitigate potential risks.
Essential Best Practices
| Best Practice | Details |
|---|---|
| Regular Backups | Ensure that all critical data, configurations, and system states are backed up regularly. Test the backups to ensure they can be restored quickly in case of system failure. |
| Automated Updates | Implement a process to automatically apply security patches and software updates. This reduces vulnerabilities and ensures that the system remains up-to-date. |
| Access Control | Apply the principle of least privilege when managing user access. Ensure that users have only the permissions necessary to perform their tasks and regularly audit access controls. |
| System Monitoring | Set up comprehensive monitoring to track system performance, resource usage, and security events. This allows proactive detection of potential issues before they affect operations. |
| Security Audits | Regularly perform security audits and vulnerability scans to identify and fix any weaknesses in the system. Implement hardening techniques to improve security. |
| Documentation | Document every change made to the system, including configuration updates, installed software, and network settings. Clear documentation aids in troubleshooting and streamlines future management. |
| Disaster Recovery Plan | Develop and maintain a disaster recovery plan that includes steps for system restoration after a failure. Ensure that backup procedures align with recovery objectives. |
Additional Tips for Effective System Administration
In addition to the essential best practices, there are a few extra tips that can further improve the effectiveness of a system administrator:
- Automate Repetitive Tasks: Use scripting and automation tools to handle routine tasks such as software updates, log rotation, and backups.
- Use Version Control: Manage configuration files and scripts using version control systems like Git. This allows easy tracking of changes and quick rollback when necessary.
- Test Changes in a Staging Environment: Before applying changes to production systems, test them in a staging environment to avoid disrupting critical services.
- Monitor System Logs: Regularly check system logs for signs of unusual activity. Set up alerts for key log events to ensure timely responses to potential issues.
- Implement Resource Optimization: Monitor system resources such as CPU, memory, and disk usage to identify performance bottlenecks and take corrective actions before they affect users.
By following these best practices and staying informed about emerging technologies and trends, system administrators can create and maintain a robust, secure, and high-performance computing environment for their organization.
Test Your Knowledge with Practice Questions
Testing your understanding through practice questions is one of the most effective ways to solidify your knowledge and prepare for real-world applications. This section presents a series of questions that will challenge your grasp of key concepts and skills. By practicing with these questions, you can assess your readiness, identify areas for improvement, and gain confidence in your abilities.
Incorporating regular practice into your study routine helps reinforce what you’ve learned and enhances your problem-solving skills. Whether you are preparing for a certification or aiming to strengthen your expertise, these questions will provide valuable insights into the practical aspects of system management.
Practice Questions
Answer the following questions to test your knowledge:
- What command would you use to check the permissions of a file?
Answer:ls -l - How can you add a new user to the system?
Answer:useradd [username] - Which command is used to change file ownership?
Answer:chown [user]:[group] [file] - What is the purpose of the
chmodcommand?
Answer:chmodis used to modify file permissions, specifying who can read, write, or execute a file. - Which file system permission corresponds to the number 7?
Answer: Full permissions (read, write, and execute).
Review and Reflect
After answering the questions, take time to review any areas where you were unsure or made errors. Understanding why a particular answer is correct, and why others are not, is key to deepening your knowledge. This process helps you retain information and apply it more effectively in practical scenarios.
Remember, mastery of these skills comes with continuous practice. Test yourself regularly and continue refining your understanding of the core principles.
Exam Tips for Linux Essentials
Preparing for any certification or assessment requires more than just memorizing facts; it involves understanding key concepts, practicing skills, and developing effective test-taking strategies. This section provides tips that can help you succeed in your preparation and perform confidently during the evaluation. With the right approach, you can approach your assessment with a clear strategy and minimize test-related stress.
Following the best practices outlined here will not only improve your knowledge but also enhance your ability to apply what you’ve learned under pressure. Let’s dive into some essential tips to guide your preparation.
Effective Study Techniques
- Understand Core Concepts: Focus on mastering the fundamental principles that are frequently tested. A strong understanding of concepts such as file permissions, user management, and system commands will give you a solid foundation.
- Use Practice Tests: Take as many practice tests as possible. These help you familiarize yourself with the format, question types, and timing constraints, boosting your confidence.
- Hands-on Practice: Beyond reading, get hands-on experience. Use virtual machines or cloud labs to practice executing commands, managing files, and troubleshooting issues in a simulated environment.
- Focus on Weak Areas: Identify the topics where you feel less confident and spend extra time reviewing those areas. Don’t neglect your strengths, but prioritize your weaknesses for improvement.
Test-Taking Strategies
- Read Questions Carefully: Always read each question thoroughly before answering. Ensure you understand what is being asked to avoid making assumptions.
- Time Management: Keep an eye on the clock during the test. If you encounter a challenging question, move on and come back to it later if time allows.
- Eliminate Wrong Answers: If you’re unsure about an answer, use the process of elimination. Narrowing down the choices increases your chances of selecting the correct one.
- Stay Calm: Test anxiety can hinder your performance. Take deep breaths, stay calm, and approach each question methodically.
Additional Resources
Use multiple resources to aid in your studies. In addition to textbooks, online tutorials, and practice exams, consider joining online forums and discussion groups. Engaging with others can provide new perspectives and help reinforce your learning.
Table of Key Areas to Focus On
| Topic | Key Focus Areas |
|---|---|
| System Commands | Master frequently used commands like ls, cd, chmod, and ps. |
| User Management | Understand how to add, modify, and delete users, groups, and permissions. |
| File System Hierarchy | Know the basic structure and location of files and directories. |
| File Permissions | Be familiar with how to assign and change file permissions using chmod and chown. |
By integrating these strategies into your study routine, you will be better prepared to tackle the assessment and demonstrate your skills effectively. Remember, consistent practice and a focused approach are key to success.
Next Steps After Chapter 4 Exam
Completing an important assessment is just the beginning of your journey towards mastering key concepts. Once you’ve finished the test, it’s time to reflect on your performance, identify areas of improvement, and plan the next steps to further enhance your knowledge. This stage is crucial for reinforcing what you have learned and ensuring long-term success in your learning path.
After completing the assessment, it’s important to analyze both your strengths and weaknesses. This allows you to focus on areas where you may need additional practice while continuing to reinforce concepts you have already mastered. By taking a strategic approach to the next phase of your preparation, you can continue progressing and stay on track for your future goals.
Review and Reflect
- Analyze Results: Take the time to review your performance carefully. Identify the questions that challenged you, and understand why you got them wrong. This reflection will provide insights into your gaps in knowledge.
- Focus on Weak Areas: If there were specific topics where you struggled, dedicate extra time to revisiting them. For example, if system commands or file permissions were difficult, go over the material again, practice the commands, and experiment in a real-world environment.
- Reinforce What You Know: While it’s important to improve weak areas, don’t forget to continue practicing and reinforcing the concepts you already know. A solid understanding of the basics is the key to building more advanced skills.
Further Learning and Practical Application
- Hands-On Practice: Practical experience is vital for solidifying theoretical knowledge. Set up virtual machines or use cloud environments to apply what you’ve learned. Test commands, manage files, and work on system configurations.
- Explore Advanced Topics: Once you feel comfortable with the basics, begin to explore more advanced topics such as automation, network management, or security. This will broaden your skill set and deepen your understanding.
- Consider Certification: If you haven’t already, consider pursuing a formal certification to validate your skills and knowledge. Certifications can help you stand out in your career and demonstrate your expertise.
By taking the time to review and practice after completing the test, you’ll be well on your way to mastering the subject and applying your knowledge effectively. Keep challenging yourself, and continue your learning journey with a growth mindset!